Search Results for "Optimizing Private Key Operations"
Find videos related to your search query. Browse through our collection of videos matching "Optimizing Private Key Operations". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Optimizing Private Key Operations"
51 results found

11:28
PRIVATE PRIVATE PRIVATE PRIVATE PRIVATE PRIVATE PRIVATE - YouTube
John Stone
8 views
8:09
Private Wealth Circle, Private Wealth Circle Review, Private Wealth Circle Scam, Private Wealth Circle System, Private Wealth Circle System
Markleecrosby
418 views

6:28
Key Of The Kaaba History In Urdu | key of kaaba family | kaaba,key of kaaba,key of the kaaba history in urdu,key of kaaba history,key of kaaba history in urdu,history of khana kaba,key of kaaba history in english,amazing history of key of khana kaaba
Knowldge Factory
10 views

3:55
difference between public key and private key, what is public key and private key, o level exam,
tech MCQ & theory
3.4K views

1:10
e-Capsule Private Browser HD Key Gen (e-Capsule Private Browser HDe-capsule private browser hd 2015)
Joshua Rogers
1 views

0:39
sbb key programmer review,Sbb Key Programmer,sbb car key programmer,sbb key programmer v33 manual,sbb key programmer v33,key programmer sbb
lara-baby
8 views

2:55
The difference between Private key and public Key || Symmetric key and Asymmetric key cryptography
Pooja Patel
10 views

3:11
Public key vs Private key ll Symmetric key vs Asymmetric key
Guptasmartclasses
38 views

9:55
what is symmetric key cryptography and asymmetric key cryptography , public key and private key
sawji gyaan
10 views

9:49
How to find Private Key in RSA algorithm | How to calculate private Key "d" in RSA algorithm
Chirag Bhalodia
17.7K views
34:25
Optimizing the HIV cascade: Promising global key population innovations
HIV-NAT Thailand
215 views

0:35
Key west florida accommodations, key west vacation rentals, key west condos, key west hideaways, key west nightlife
Tommy Lee
57 views

6:43
Network & Cyber Security Lecture: Symmetric key Encryption (Private Key) Key Based Cryptography
Sanjay Pathak
1.8K views

11:18
Symmetric Key Cryptography VS Asymmetric Key Cryptography | Private vs Public Key Cryptography
Simple Snippets
8.7K views

29:00
Asymmetric Key Encryption (Private key vs public key encryption)
iq pop
48 views

7:11
What is BODMAS Rule | PEMDAS | Easy Way | Order of Mathematical Operations | Order of Operations
Epic Learning
35.5K views

5:15
How Crypto wallets work | 🗝🔐Private keys & Public Keys | Private aur Public key kya hai | Hindi/Urdu
Haroon VOICE
816 views

25:09
Card-based cryptographic protocols for three-input functions using private operations
Fields Institute
139 views

0:40
Private Equity Funds: Business Structure and Operations For Kindle
asarkhalekhale
1 views

2:32
Optimizing IBM App Connect start-up times
IBM Developer
404 views
0:13
AI-Powered People Counting System: Optimizing Traffic Control and Safety Management
ToyTech Machines
133.8K views
13:47
3. Optimizing Linear Regression models using RapidMiner Studio
Kira Kung
12 views
5:55
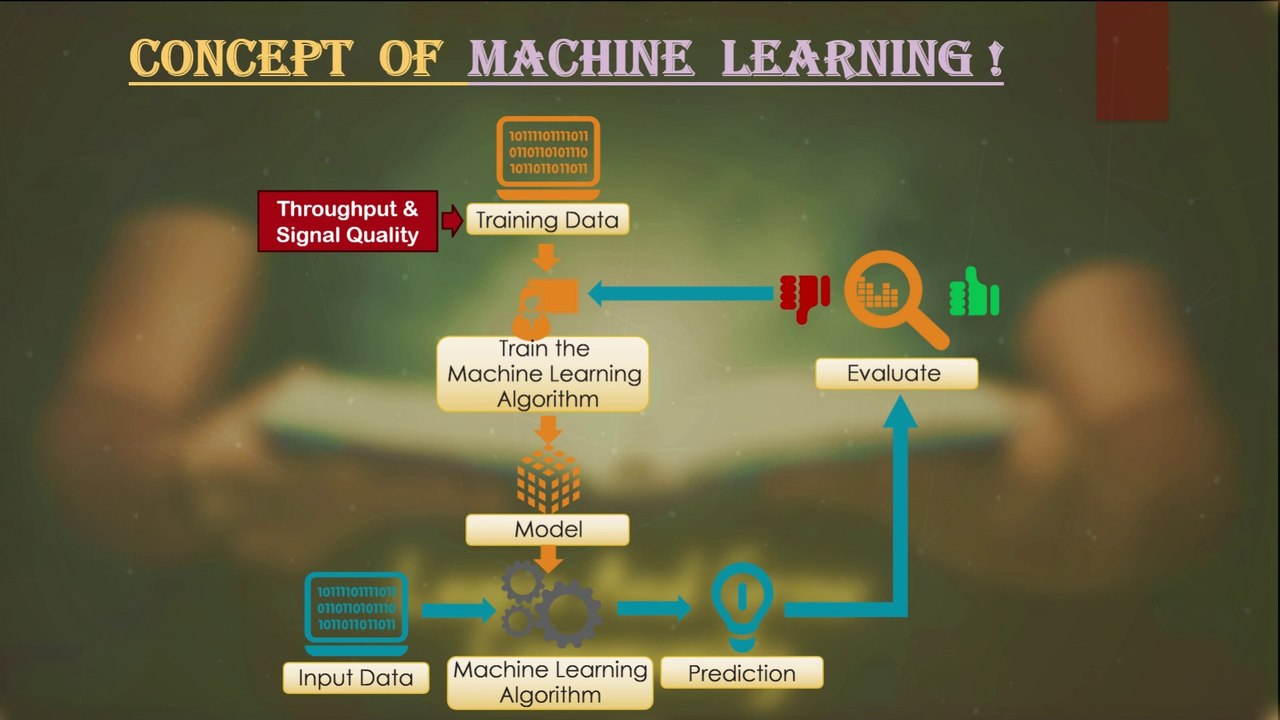
Session 16: Optimizing Open RAN with Machine Learning | concept overview
Learn And Grow Community
3 views

1:32
Optimizing the RSA Algorithm for Polynomial Encryption
vlogize
6 views

2:20
Optimizing Miller-Rabin Primality Test in Python
Roel Van de Paar
61 views
0:39
corporate finance - Give A brief On Optimizing
MBA Case Study Solutions
2 views

1:02:37
Who is Afraid of Vectors�Optimizing Cryptography Using SSE, AVX, NEON, and Co.
Microsoft Research
906 views
![[Read] High Performance Spark: Best Practices for Scaling and Optimizing Apache Spark Complete](/image/s2.dmcdn.net/v/Ro02j1cm027HAcD0S/xx720.pagespeed.ic.nYVFOmg42E.jpg)
0:31
[Read] High Performance Spark: Best Practices for Scaling and Optimizing Apache Spark Complete
yidami3943
2 views

0:39
Full E-book High Performance Spark: Best Practices for Scaling and Optimizing Apache Spark For
dm_89d7152604c4add70ca0b3d8f37b3069
2 views

0:37
Optimizing Data Center Efficiency with Algorithms
CyberGuard
3 views

0:53
Optimizing Computational Models in Semiconductor Manufacturing
Advantest
87 views

0:54
"Operationally, computing power is the biggest issue. It requires optimizing all these resources"
Beryl Elites
1.5K views

2:07
Optimizing FPGA Logic Block Architecture For Arithmetic | VLSI Projects for Final Year
Takeoff Edu Group
332 views

2:01
Optimizing Your DFS Lineup: The Best RBs for Wild Card Weekend
SportsGrid
1.0K views

2:43
Optimizing Fantasy Football Picks: Wide Receivers Insight
SportsGrid
47.0K views

2:42
Optimizing Fantasy Football Drafts: The Value of Derrick Henry
SportsGrid
898 views

13:10
RAG vs Fine-Tuning vs Prompt Engineering: Optimizing AI Models
IBM Technology
444.3K views

1:07
‘World’s Tallest Autonomous Robots’ Begin Optimizing Warehouse Management in the U.K.
Veuer
1.3K views

3:15
Optimizing Your Brain Game
LifeMinute.tv
12.3K views

6:57
Key Management and Key Distribution in Cryptography | Key Management | Key Distribution
Chirag Bhalodia
100.9K views

1:10
Magic Key Extractor Key Gen (Magic Key Extractormagic key extractor 2015)
Brenda Diaz
27 views

1:00
Key locksmith Dubai, key repairing, key making, key locksmith, locksmith Dubai
Ummeammarah11
2 views

0:48
°FIFA 14° °KEYGEN°°KEY GENERATOR°°ACTIVATION°°PRODUCT KEY°°SERIAL KEY°°LICENCE KEY
morientesmalaka
241 views
![Mirrakey License Key Generator Key Gen [Mirrakey License Key Generatormirrakey license key generator 2015]](/image/s2.dmcdn.net/v/8_ZGQ1e0GZW5oh8l_/xx720.pagespeed.ic.P1ZMrUV2OK.jpg)
1:50
Mirrakey License Key Generator Key Gen [Mirrakey License Key Generatormirrakey license key generator 2015]
Bob Sanderson
6 views

3:17
Best Key West Restaurants | Best Key West Nightclubs | Best Key West DJs | Whats Hot Key West
LJ Cange
1 views

19:02
Asymmetric Encryption With OpenSSL (Private Key & Public Key)
NeuralNine
15.7K views

1:01
What’s the difference between a public key and a private key? #web3 #blockchain #crypto #nft
Dr. Brook Sheehan
484 views

10:05
RSA Example Lecture 1 | p=7, q=11, plaintext=m=9, Find public key (e), private key (d) & ciphertext
TRN CSE Tutorials
2.2K views

2:34:59
Encryption & Decryption Techniques for Symmetric Key Cryptography | Private Key Cryptography
Shiv Yog Classes
4 views

1:00
What is the difference between public key and private key encryption
Sigma Cyber Security
515 views

1:40
Cmiami Private Key checker
Zipix
812 views
Page 1 Next