Search Results for "Cybersecurity Capstone: Breach Response Case Studies"
Find videos related to your search query. Browse through our collection of videos matching "Cybersecurity Capstone: Breach Response Case Studies". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Cybersecurity Capstone: Breach Response Case Studies"
50 results found

2:25
Cybersecurity Capstone: Breach Response Case Studies Week 1 Quiz Answer | Incident Management
Course Fry
840 views

0:52
Case no 9 Episode 13 promo|case no 9 |case no.9| case no 9 episode 13 full|case no 9. 13 promo#viral
Pakistani Drama Review
25.5K views

0:51
Case no 9 Episode 11 promo| case no 9 |case no.9| case no 9 episode 10 full|case no 9-11 promo#viral
Pakistani Drama Review
57.5K views

0:54
Case no 9 Episode 12 promo|case no 9 |case no.9| case no 9 episode 11 full|case no 9. 12 promo#viral
Pakistani Drama Review
3.3K views

2:00
Parliament Security Breach: Mahesh Kumawat, sixth accused in LS security breach, arrested| Oneindia
Oneindia
223 views
7:01
Data Breach News | 16 Billion Logins Stolen In Mega Data Breach Threatening Apple, Google And More
NDTV
44.9K views

0:07
Read Analysis of Multidimensional Poverty: Theory and Case Studies (Economic Studies in Inequality
Green Maisie
0 views

0:08
Read Analysis of Multidimensional Poverty: Theory and Case Studies (Economic Studies in Inequality
Robinson1987
0 views

6:13
Imran Khan Pr Ciphar Case Batna Hi Nahi | The cipher case of Imran Khan is not being made.. The cipher case is being dragged unnecessarily... The day the cipher was waved?... The cipher case is not a crime... This crime has been added. ... Aitzaz Ahsan
Update Pakistan News
6 views

0:06
Read Handbook of Item Response Theory Three Volume Set: Handbook of Item Response Theory Volume
Baldassare
0 views

0:28
China’s response to NASA on lunar samples studies
CGTN Europe
2.5K views

2:58
What is a Breach? | Cybersecurity
Aldridge
520 views

0:47
How Do Data Breaches Happen? #HIPAA #EDI #cybersecurity #breach #IT #technology #tech #healthcare
HIPAA Vault
82 views
0:12
Network Security and Data Breach Cybersecurity Measures
Insurance Insight
2 views

0:05
Download Research Methods in Cultural Studies: Research Methods for Cultural Studies (Research
Macdonald Brooke
4 views

0:06
Download Endogenous Economic Fluctuations: Studies in the Theory of Rational Beliefs (Studies
Caecilius170
1 views

0:06
Read Generative Social Science: Studies in Agent-Based Computational Modeling (Princeton Studies
Khan Olivia
1 views

0:05
Read Research Methods in Cultural Studies: Research Methods for Cultural Studies (Research
Aliya Tairov
2 views

0:07
Read Empirical Studies of the Therapeutic Hour (Empirical Studies of Psychoanalytic Theories
Klouka
0 views

0:07
Download Empirical Studies of the Therapeutic Hour (Empirical Studies of Psychoanalytic Theories
Vaso Rodi
1 views
![[PDF] Empirical Studies of the Therapeutic Hour (Empirical Studies of Psychoanalytic Theories;](/image/s1.dmcdn.net/v/H5o_J1e0s1N0ulMv3/x720)
0:31
[PDF] Empirical Studies of the Therapeutic Hour (Empirical Studies of Psychoanalytic Theories;
Giraldo Pat
3 views

7:51
Why Do African Students Consider STEM Studies Superior to Social Studies, Business and Sociology?
Jerry Rawlings
9 views

4:23
4 Case Study #3 The Equifax Breach
AC CONSULTING
72 views

2:26
What is Cybersecurity? | Cybersecurity in 2 Minutes | Cybersecurity Online Training | Edureka
edureka!
274.3K views

0:05
Cybersecurity roadmap for beginners | Cybersecurity roadmap | Cybersecurity #shorts #trendingshorts
Bang On Theory
152.0K views

2:53:42
🔥Cybersecurity basics | Cybersecurity Basic Knowledge | Cybersecurity | 2024 | Simplilearn
Simplilearn
265.7K views

0:59
My Cybersecurity Journey | How to Get into Cybersecurity | Cybersecurity careers | #ytshorts
Meera Tamboli
141.3K views

29:29
Most Common CyberSecurity Threats | CyberSecurity Attacks | CyberSecurity For Beginners |Simplilearn
Simplilearn
11.8K views

0:21
Time Complexity of sorting methods - Best Case, Average Case, Worst Case/ Data structure - I
Education Guru
50 views

2:36
Case No.9 Next Episode 12 & 13 Teaser Breakdown | Case No 9 Ep 12 Promo | Case No 9 Ep 12 Ful Teaser
Pak Promos Point
25.5K views

0:48
Case No.9 Episode 13 Teaser | Case No 9 Episode 13 Promo | Saba Qamar Case No 9 Drama | Har Pal Geo
Social Slush
19.4K views

3:06
Case No 9 Ep 12 & 13 Teaser | Case No.9 Ep 12 Promo Review | Case No 9 Ep 12 Full Story Breakdown
PAK Dramas Reviews
6.0K views

0:22
Iphone X MagSafe Case Iphone All Models Case Available #magsafe #case #asiastore #shortsvideo #asia
Ammarrao23
438.0K views

11:46
Day-6 | Possessive Case | Noun Case | Case in English Grammar | How to use Apostrophe 's in English
Best English Guru
4 views

13:09
Day-7 | Possessive Case | Noun Case | Case in English Grammar | How to use Apostrophe 's in English
Best English Guru
1 views

4:24
ciphar case ky hawale se tehlka khaiz news | We had submitted a petition file in the Islamabad High Court regarding the cipher case, we have received information that our case has been cancelled, it has been one and a half months since Imran Khan
Update Pakistan News
4 views

6:55
عمران خان پر 200 سے اوپر کیس بناۓ گئے | What will be the hearing in the cipher case in Adiala Jail today? The Election Commission is also going to jail, the Al-Qader Trust case and the Tashah Khana case will also be heard today! Who is behind these cases?
Update Pakistan News
5 views

0:25
Proiecte case moderne, modele case moderne, planuri case moderne
Proiecte Case
1 views

3:24
Gen AI Capstone Project Cybersecurity Agent Using Gemini
Candy Chan
69 views

3:20
What Are Quantum-resistant Algorithms For Future Cybersecurity? - Crisis Response Coach
Crisis Response Coach
1 views

3:15
How Will Quantum Cryptography Change Cybersecurity Measures? - Crisis Response Coach
Crisis Response Coach
3 views
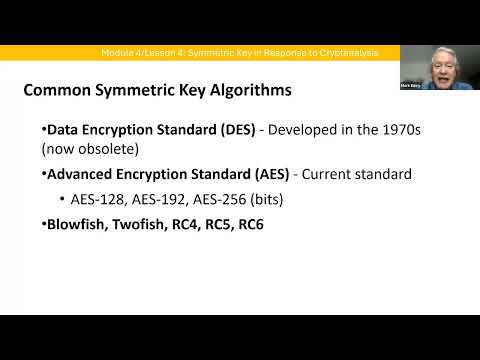
14:20
Foundations of Cybersecurity: Symmetric Key in Response to Cryptanalysis Video Lecture
TeachCyber
70 views

0:19
Unlocking the Secrets of Ancient Romance and Economic Case Studies
RizzJesusYoutube
6 views
0:41
Practical Crypto Investing Playbook: Real Case Studies and Expert Interviews
MoonSignalss
23 views

0:49
The Durable Crypto Playbook Through Expert Insights and Real Case Studies
CoinWorld
76 views

0:43
Crypto Playbook 2025: Real World Tips from Experts and Case Studies
CoinWorld
38 views
0:44
Unseen Pre-Surge Drivers in Five Crypto Case Studies
Crypto World
35 views
0:43
Crypto Foundations to Real Wins: Expert Interviews and Case Studies
Crypto Frontier
36 views
![[CS161 FA25] Public-Key Encryption, Digital Signatures, Certificates, Passwords, Case Studies](/image/i.ytimg.com/vi/PEPJVzhHUWw/hqdefault.jpg)
2:50:25
[CS161 FA25] Public-Key Encryption, Digital Signatures, Certificates, Passwords, Case Studies
CS 161 (Computer Security) at UC Berkeley
374 views

0:16
Effortless Case Studies: Automate Your Workflow with AI
Zapier
3.3K views