অ্যাসিমেট্রিক ক্রিপ্টোগ্রাফি: পাবলিক ও প্রাইভেট কী এর কার্যপ্রণালী 🔐
শেখুন কিভাবে অ্যাসিমেট্রিক ক্রিপ্টোগ্রাফিতে পাবলিক ও প্রাইভেট কী ব্যবহৃত হয় এবং এটি কিভাবে নিরাপত্তা নিশ্চিত করে।

Engineering Bangla
857 views • Jan 19, 2020
About this video
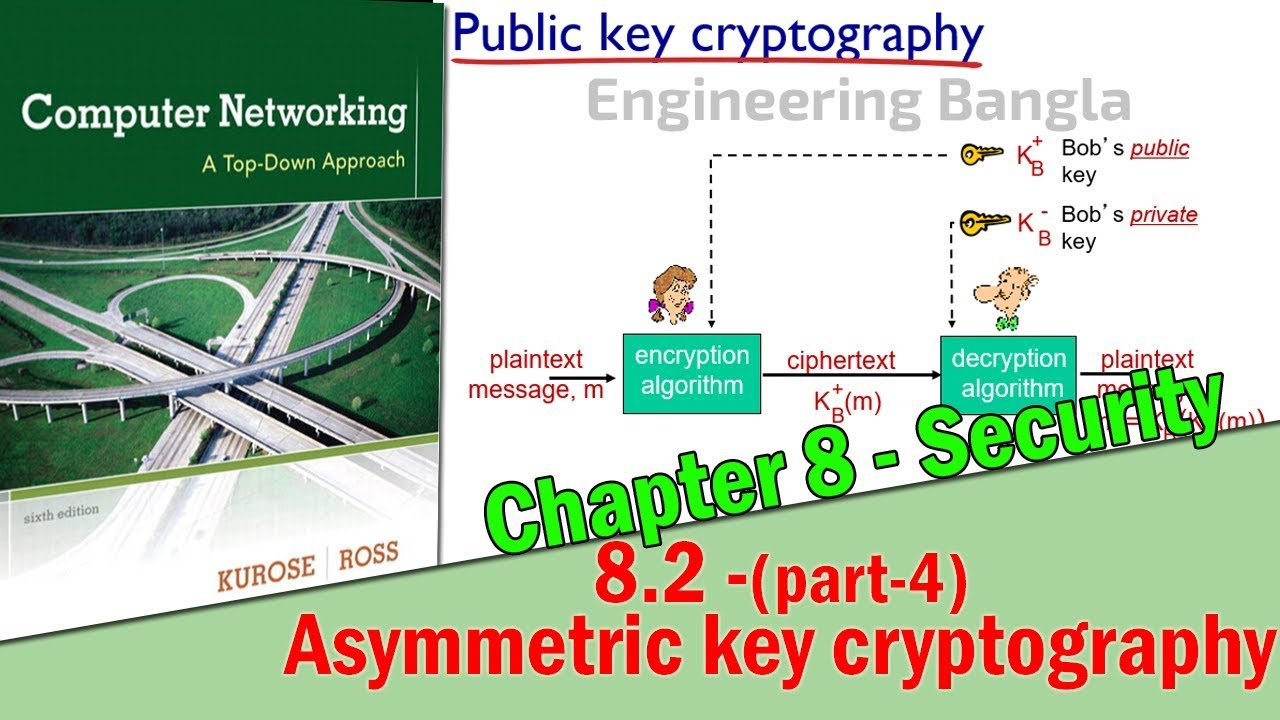
8.2 (part-4) - Asymmetric (public,private) key cryptography of Security | Computer Network Bangla
In public key encryption, two different keys are used to encrypt and decrypt data.One is the public key and other is the private key. These two keys are mathematically related. They come as a pairs.
The public key encryption is also called asymmetric key encryption because two different keys are used.
Public key algorithm is used for different purpose from private key algorithm. It is used for verification and authentication.
#EngineeringBnagla
#ComputerNetwork
In public key encryption, two different keys are used to encrypt and decrypt data.One is the public key and other is the private key. These two keys are mathematically related. They come as a pairs.
The public key encryption is also called asymmetric key encryption because two different keys are used.
Public key algorithm is used for different purpose from private key algorithm. It is used for verification and authentication.
#EngineeringBnagla
#ComputerNetwork
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
857
Likes
14
Duration
4:02
Published
Jan 19, 2020
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.