Unlocking Security: The Power of Symmetric Key Cryptography 🔐
Discover how symmetric key cryptography uses techniques like XOR to protect data. Perfect for understanding essential cybersecurity methods in computer science!

Computer Science Lessons
4.4K views • Mar 9, 2019
About this video
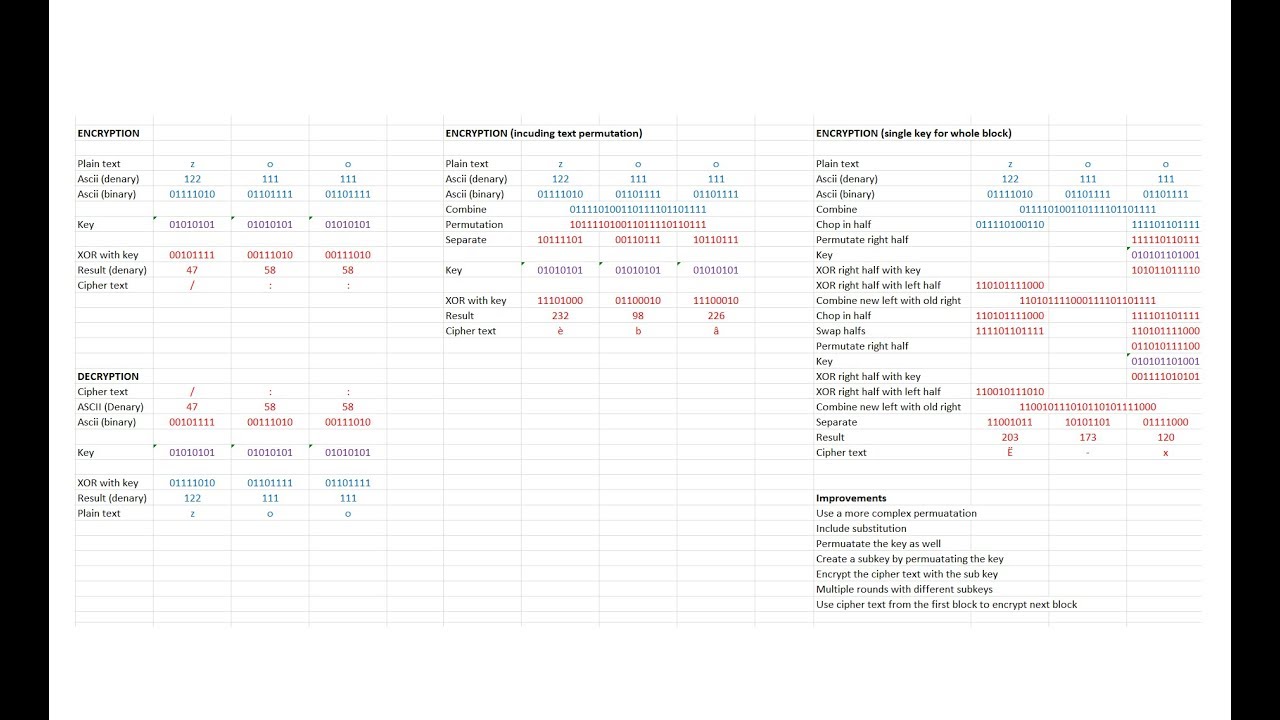
This is the fifth in a series about cryptography; an extremely important aspect of computer science and cyber security. It reviews how the XOR logical operation can be used to encrypt at the bit level in symmetric key cryptography, then shows how this can be combined with permutation steps to create an even stronger cipher. It mentions a number of principles used in modern day block ciphers such as DES and AES, including the Feistel cipher, block ciphers, block chaining, the use of multiple sub keys and multiple encryption rounds.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
4.4K
Likes
99
Duration
11:02
Published
Mar 9, 2019
User Reviews
4.6
(4) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.