Unlocking Secrets with Steganography: A Guide to Stenography in Ethical Hacking 🔐
Discover how Steghide and steganography techniques are used by ethical hackers to hide and uncover data within files. Learn the essentials of this powerful security tool!

AmsR HuB
72 views • Nov 12, 2024
About this video
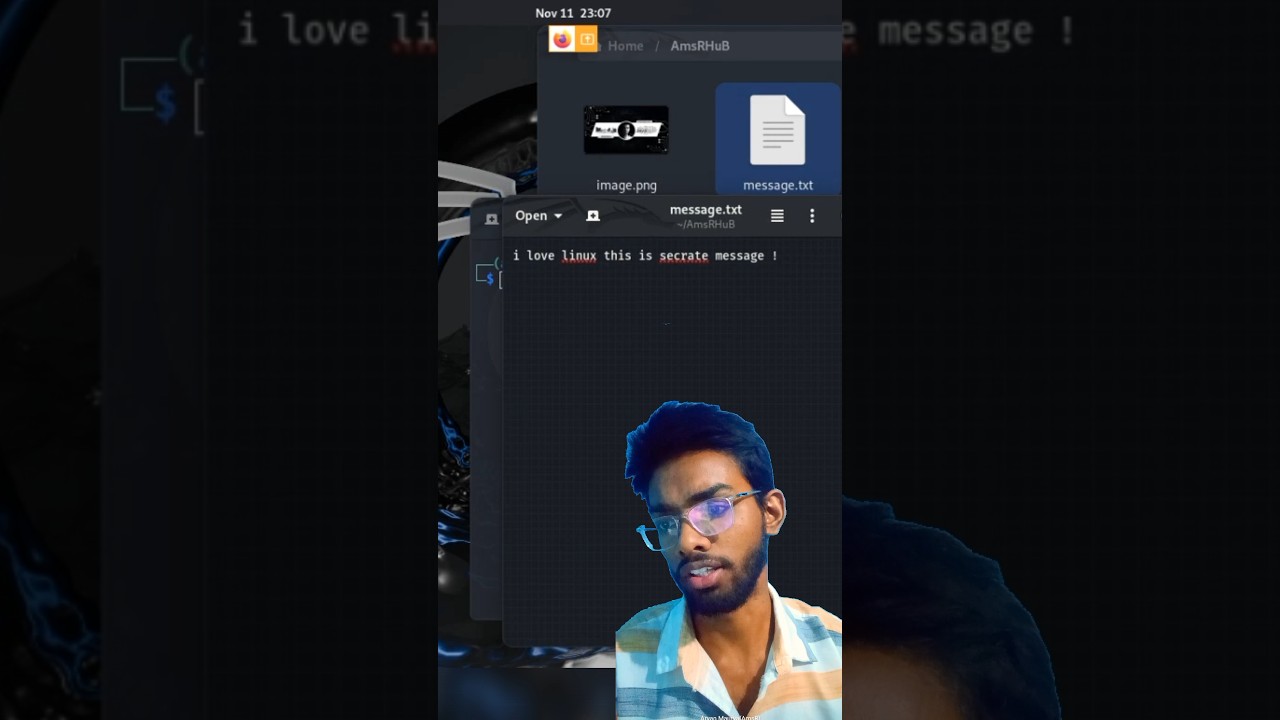
In the context of **ethical hacking**, **Steghide** is a popular tool used for **steganography**, which is the practice of concealing data within other, seemingly innocuous files such as images, audio, or video files. Steghide allows an attacker or ethical hacker to hide data within these types of files and retrieve it later without arousing suspicion.
### Key Features of Steghide:
1. **Data Hiding**: Steghide can embed data (like text files, executables, or other data) inside multimedia files (e.g., JPEG, BMP, WAV, AU).
2. **Encryption**: When embedding data, Steghide can optionally encrypt the hidden data using a passphrase, making it more secure and harder to detect or extract without the correct key.
3. **Compression**: The hidden data can also be compressed to minimize the file size and further obscure the presence of the hidden data.
4. **Supported Formats**: It supports multiple file formats for embedding data, such as image files (JPEG, BMP), audio files (WAV, AU), etc.
### Basic Usage of Steghide:
#### Embedding Data:
To embed data into a cover file (e.g., an image or audio file), you would use a command like:
```bash
steghide embed -cf image.jpg -ef secret.txt
```
Where:
- `-cf image.jpg` is the cover file (in this case, an image).
- `-ef secret.txt` is the file containing the data you want to hide (in this case, a text file).
You will be prompted to enter a passphrase, which will be used to encrypt the hidden data.
#### Extracting Data:
To extract the hidden data from the cover file, you would use:
```bash
steghide extract -sf image.jpg
```
Where `-sf image.jpg` is the file containing the hidden data.
If the data was encrypted, you’ll need the passphrase to extract the contents.
### Ethical Hacking Context:
Steghide and other steganography tools are often used in **penetration testing** or **red teaming** exercises to test if sensitive data can be hidden within seemingly benign files and to check whether security mechanisms are in place to detect or prevent this kind of activity.
Ethical hackers may also use such tools to check for potential vulnerabilities in communication channels, such as embedding malware or confidential information within media files to test detection systems.
However, it's important to note that using steganography tools like Steghide without authorization or for malicious purposes is illegal and unethical. In ethical hacking, such tools should only be used within the confines of an agreed-upon testing environment or under the permission of the target system owner.
#hacker #coding #coder #stegnography #steghide #kali #linux #programming
### Key Features of Steghide:
1. **Data Hiding**: Steghide can embed data (like text files, executables, or other data) inside multimedia files (e.g., JPEG, BMP, WAV, AU).
2. **Encryption**: When embedding data, Steghide can optionally encrypt the hidden data using a passphrase, making it more secure and harder to detect or extract without the correct key.
3. **Compression**: The hidden data can also be compressed to minimize the file size and further obscure the presence of the hidden data.
4. **Supported Formats**: It supports multiple file formats for embedding data, such as image files (JPEG, BMP), audio files (WAV, AU), etc.
### Basic Usage of Steghide:
#### Embedding Data:
To embed data into a cover file (e.g., an image or audio file), you would use a command like:
```bash
steghide embed -cf image.jpg -ef secret.txt
```
Where:
- `-cf image.jpg` is the cover file (in this case, an image).
- `-ef secret.txt` is the file containing the data you want to hide (in this case, a text file).
You will be prompted to enter a passphrase, which will be used to encrypt the hidden data.
#### Extracting Data:
To extract the hidden data from the cover file, you would use:
```bash
steghide extract -sf image.jpg
```
Where `-sf image.jpg` is the file containing the hidden data.
If the data was encrypted, you’ll need the passphrase to extract the contents.
### Ethical Hacking Context:
Steghide and other steganography tools are often used in **penetration testing** or **red teaming** exercises to test if sensitive data can be hidden within seemingly benign files and to check whether security mechanisms are in place to detect or prevent this kind of activity.
Ethical hackers may also use such tools to check for potential vulnerabilities in communication channels, such as embedding malware or confidential information within media files to test detection systems.
However, it's important to note that using steganography tools like Steghide without authorization or for malicious purposes is illegal and unethical. In ethical hacking, such tools should only be used within the confines of an agreed-upon testing environment or under the permission of the target system owner.
#hacker #coding #coder #stegnography #steghide #kali #linux #programming
Video Information
Views
72
Duration
0:55
Published
Nov 12, 2024
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.