Unlocking RSA: The Key to Stronger Cybersecurity & Data Protection 🔐
Discover how the RSA algorithm enhances cybersecurity by ensuring data confidentiality, integrity, and authentication. Learn why it's vital in preventing data breaches and safeguarding your digital assets.

Naresh KSHETRI
5.1K views • Mar 24, 2024
About this video
#cybersecurity #databreach #datarisk #cybersecuritygoals #breachimpact #cryptography #confidentiality #integrity #authentication #nonrepudiation #symmetriccryptography #rsaalgorithm #primenumber #privatekey #secretkeys #alicebob
* Hello everyone, welcome back, in this video, I am explaining RSA algorithm of asymmetric cryptography (developed in 1977, based on difficulty of factoring prime numbers) !
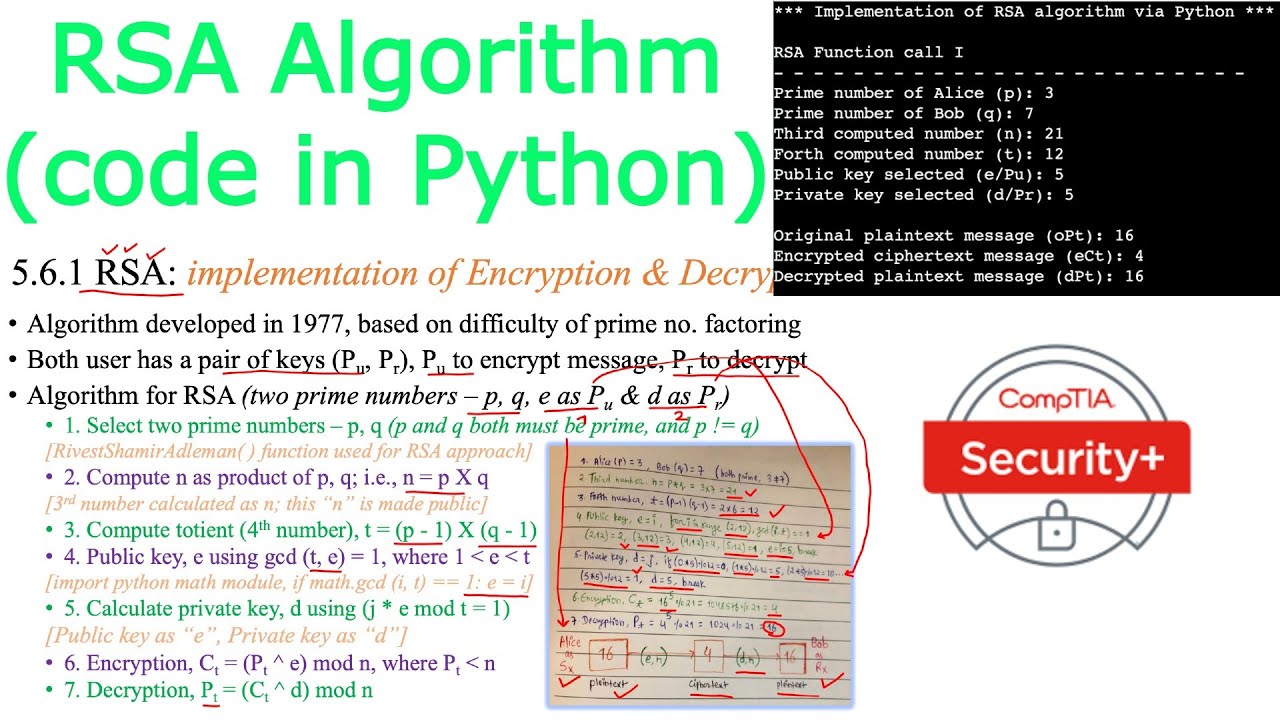
* The RSA algorithm is as follows:
1. Select 2 prime numbers – p, q (both must be prime, and p != q) [RivestShamirAdleman( ) function module]
2. Compute n as product of p, q; i.e., n = p X q [3rd no calculated as n; this “n” is made public]
3. Compute totient (4th number), t = (p - 1) X (q - 1)
4. Public key, e using gcd (t, e) = 1, where 1 "is less than" e "is less than" t [import math, if math.gcd (i, t) == 1: e = i]
5. Calculate private key, d using (j * e mod t = 1) [Public key as “e”, Private key as “d”]
6. Encryption, Ct = (Pt ^ e) mod n, where Pt "is less than" n
7. Decryption, Pt = (Ct ^ d) mod n
* Also, the python code implementation of the RSA algorithm in OnlineGDB compiler (https://www.onlinegdb.com/) with project codes in two python files (rsa-algorithm.py, RivestShamirAdleman.py) in GitHub repository (link provided below).
* YouTube channel link: https://www.youtube.com/@NareshKSHETRI
* Cybersecurity playlist in my Channel: https://www.youtube.com/playlist?list=PL7-xjgCdZq85ZwT6L6UHLc39rGGGX60Wc
* Python code in GitHub repository: https://github.com/kshetrinaresh/CybSec
* LinkedIn (let us connect): https://www.linkedin.com/in/NareshKshetri/
* Website (Google Sites): https://sites.google.com/view/NareshKshetri
* Please like, share, & subscribe if the video was helpful !
* Hello everyone, welcome back, in this video, I am explaining RSA algorithm of asymmetric cryptography (developed in 1977, based on difficulty of factoring prime numbers) !
* The RSA algorithm is as follows:
1. Select 2 prime numbers – p, q (both must be prime, and p != q) [RivestShamirAdleman( ) function module]
2. Compute n as product of p, q; i.e., n = p X q [3rd no calculated as n; this “n” is made public]
3. Compute totient (4th number), t = (p - 1) X (q - 1)
4. Public key, e using gcd (t, e) = 1, where 1 "is less than" e "is less than" t [import math, if math.gcd (i, t) == 1: e = i]
5. Calculate private key, d using (j * e mod t = 1) [Public key as “e”, Private key as “d”]
6. Encryption, Ct = (Pt ^ e) mod n, where Pt "is less than" n
7. Decryption, Pt = (Ct ^ d) mod n
* Also, the python code implementation of the RSA algorithm in OnlineGDB compiler (https://www.onlinegdb.com/) with project codes in two python files (rsa-algorithm.py, RivestShamirAdleman.py) in GitHub repository (link provided below).
* YouTube channel link: https://www.youtube.com/@NareshKSHETRI
* Cybersecurity playlist in my Channel: https://www.youtube.com/playlist?list=PL7-xjgCdZq85ZwT6L6UHLc39rGGGX60Wc
* Python code in GitHub repository: https://github.com/kshetrinaresh/CybSec
* LinkedIn (let us connect): https://www.linkedin.com/in/NareshKshetri/
* Website (Google Sites): https://sites.google.com/view/NareshKshetri
* Please like, share, & subscribe if the video was helpful !
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
5.1K
Likes
6
Duration
7:58
Published
Mar 24, 2024
User Reviews
3.8
(1) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now