Unlocking Data Security: Latest Advances in Cryptography & Secure Hardware 🔐
Discover cutting-edge techniques in cryptography and secure hardware that revolutionize data outsourcing. Join us for expert insights and Q&A in this comprehensive tutorial!

IEEE ICDE
230 views • May 6, 2020
About this video
Table of Contents (powered by https://videoken.com)
0:01:36 Advances in Cryptography and Secure Hardware for Data Outsourcing
0:03:38 Contents
0:06:42 Q/A
0:07:14 Cloud Computing
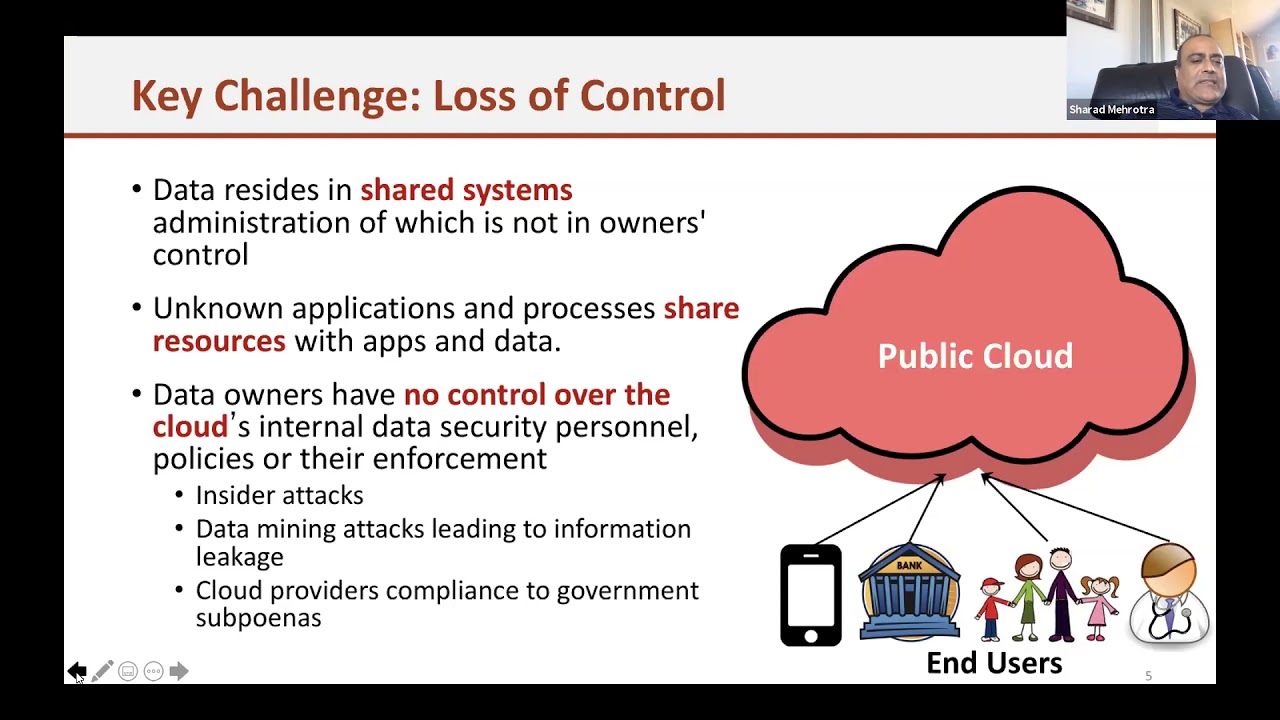
0:09:29 Key Challenge: Loss of Control
0:12:09 Implications of Loss of Control
0:13:43 What is The Solution?
0:13:53 Secure Computing
0:17:42 Common Attacks in Data Outsourcing
0:22:26 Adversarial Cloud Model
0:24:02 Defining Security
0:27:17 Security Goal: IND-CKA1: Real Game Model with Leakage Profile
0:31:15 Cloud Layers and Security
0:35:32 Encryption-based Cryptographic Approaches
0:37:02 MPC and Secret Shared Mechanisms
0:39:43 Cryptographic Techniques vs Security Threats
0:41:25 Cryptographic Techniques - Design Criteria
0:43:16 Exploiting Trusted Platform
0:45:46 Trusted Platform - Challenges
0:47:42 Security Techniques vs Computation Cost
0:49:16 Secure Data Outsourcing: Challenge
0:50:40 Data Sensitivity
0:51:43 Partitioned Data Security Challenge
0:55:28 Cryptographic Solutions
0:56:57 Problems
0:57:13 Searchable Encryption: Ciphertext Generation
0:58:48 Searchable Encryption: Search at the Cloud
1:01:40 Indexable Searchable Encryption
1:05:40 Create Index using Prefix Family: Top-Down V
1:07:27 Execute a Point Query using the Index
1:08:56 Execute a Range Query
1:10:48 Issues with the Index (PB-Tree)
1:12:37 Order Preserving Encryption (OPE)
1:13:54 Mutable OPE (mOPE)
1:18:16 What we have discussed so far?
1:18:52 Bucketization
1:21:11 What We Have Seen in Bucketization?
1:22:06 Precomputed Joins: Different Representation of Data
1:26:36 Other Encryption-based Join Approaches
1:27:00 What we have seen so far?
1:27:21 Encryption-based Systems
1:28:15 Pros and Cons of Encryption-based Techniques
1:30:16 Secret-Sharing-based Data
Outsourcing
0:01:36 Advances in Cryptography and Secure Hardware for Data Outsourcing
0:03:38 Contents
0:06:42 Q/A
0:07:14 Cloud Computing
0:09:29 Key Challenge: Loss of Control
0:12:09 Implications of Loss of Control
0:13:43 What is The Solution?
0:13:53 Secure Computing
0:17:42 Common Attacks in Data Outsourcing
0:22:26 Adversarial Cloud Model
0:24:02 Defining Security
0:27:17 Security Goal: IND-CKA1: Real Game Model with Leakage Profile
0:31:15 Cloud Layers and Security
0:35:32 Encryption-based Cryptographic Approaches
0:37:02 MPC and Secret Shared Mechanisms
0:39:43 Cryptographic Techniques vs Security Threats
0:41:25 Cryptographic Techniques - Design Criteria
0:43:16 Exploiting Trusted Platform
0:45:46 Trusted Platform - Challenges
0:47:42 Security Techniques vs Computation Cost
0:49:16 Secure Data Outsourcing: Challenge
0:50:40 Data Sensitivity
0:51:43 Partitioned Data Security Challenge
0:55:28 Cryptographic Solutions
0:56:57 Problems
0:57:13 Searchable Encryption: Ciphertext Generation
0:58:48 Searchable Encryption: Search at the Cloud
1:01:40 Indexable Searchable Encryption
1:05:40 Create Index using Prefix Family: Top-Down V
1:07:27 Execute a Point Query using the Index
1:08:56 Execute a Range Query
1:10:48 Issues with the Index (PB-Tree)
1:12:37 Order Preserving Encryption (OPE)
1:13:54 Mutable OPE (mOPE)
1:18:16 What we have discussed so far?
1:18:52 Bucketization
1:21:11 What We Have Seen in Bucketization?
1:22:06 Precomputed Joins: Different Representation of Data
1:26:36 Other Encryption-based Join Approaches
1:27:00 What we have seen so far?
1:27:21 Encryption-based Systems
1:28:15 Pros and Cons of Encryption-based Techniques
1:30:16 Secret-Sharing-based Data
Outsourcing
Video Information
Views
230
Likes
2
Duration
01:30:44
Published
May 6, 2020
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.