Unlocking Cryptography Fundamentals 🔐 - Be The H.A.C.R. Episode 4
Dive into the basics of cryptography in this fourth episode of Be The H.A.C.R. Learn essential concepts and techniques to protect information and secure communications.

Hacking Simplified
772 views • May 22, 2020
About this video
Basic Cryptography - Be The H.A.C.R. - Ep - 04
In this fourth episode, I would talk about basic cryptography.
First we will understand the basics of cryptography and then move on to the mission.
There we will try understanding the logic of the given crypto and solve it manually.Watch this video till the end to see a trick as to how you could solve it with 5 lines of code in a much faster and reliable way.
Some of the things you'd learn about in this video :
Some ancient cryptography and how it's relevant to the mission
Basics of modern cryptography
Difference between encryption, encoding and hashing.
Also difference between steganography and cryptography
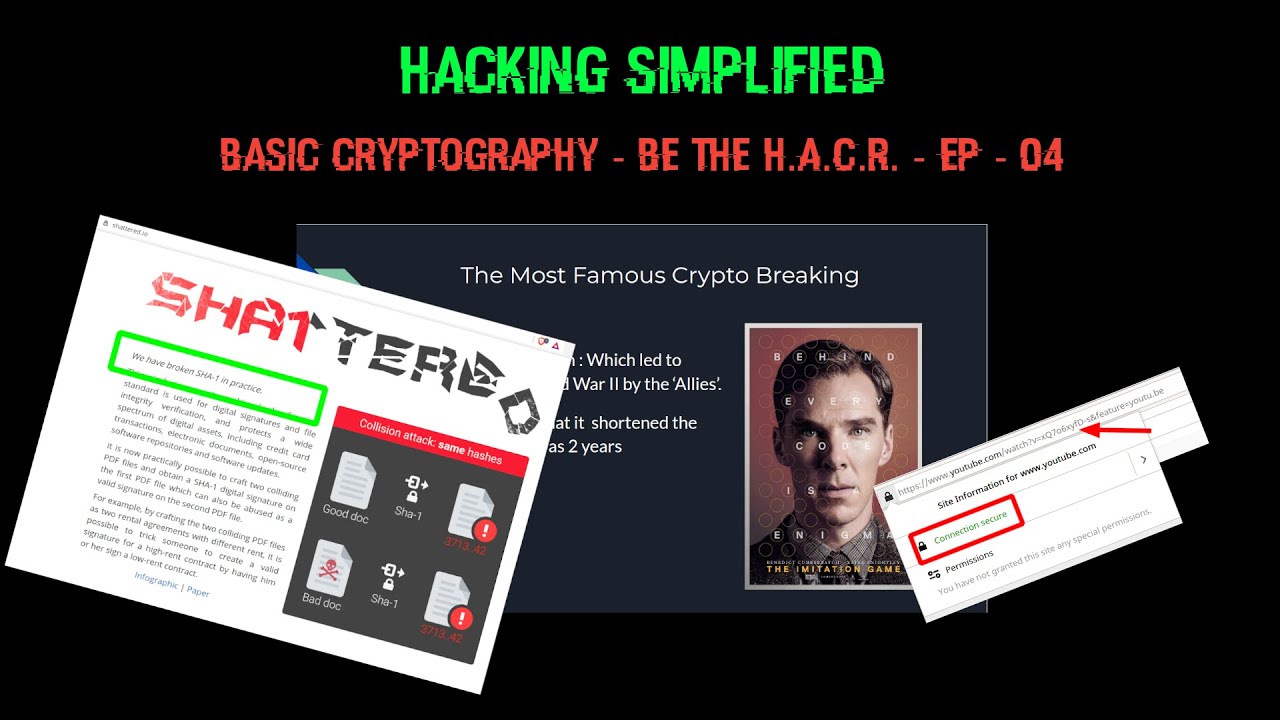
What are hashes, some of it's types and about hash collision attack
Generating hashes locally on your system
How you could verify if the file you downloaded has been tampered with or not ?
How cryptography is keeping this connection, the connection on which you're watching this youtube video, secure.
Then we will close the slides by discussing one of the most famous crypto-fails of all time, the breaking of enigma, which led to turning the tides in favor of Allies during WW2.
During the missions -
Break the cipher manually
Then automate it using python
We will also learn about ASCII coding and know about some other character encoding schemes.
We will wrap today's session with 5 liner python code - no coding background
---------------------------------------------------------------------------------------------------------------------------
Links from the video :
Slides : https://docs.google.com/presentation/d/1Mr77FLnIsswdBPGevZpviXlxeaSGEfKaelrB5HdtISM/
HTS Mission 6 : https://www.hackthissite.org/missions/basic/6/
---------------------------------------------------------------------------------------------------------------------------
---------------------------------------------------------------------------------------------------------------------------
Key Takeaways :
1. Cryptography, or cryptology, is the practice and study of techniques for secure communication in the presence of third parties called adversaries.
2. Difference between Hashing, Encoding, Encryption and Steganography
3. Hashing is used to verify the integrity of files
4. ASCII is one of the many character encoding methods
5. Let machines do the boring work - Automate the boring stuff with code
---------------------------------------------------------------------------------------------------------------------------
Detailed Google FeedBack Form : https://forms.gle/rA9oy5wqN5GSLkh8A
Join the telegram channel to get latest articles related to cybersecurity and hacking : https://t.me/hackingsimplified42
Thank you everyone.
Hope it was worth your time.
---------------------------------------------------------------------------------------------------------------------------
About the Channel :
You would've started or would like to start hacking, wait no more, start here.
You're in the right place.
Hack
Automate
Code
Repeat
Be The H.A.C.R.
This is the first episode in a long series of videos.
This series will include :
1. Web exploitation - Common attack vectors ( OWASP top 10, how to find targets, automating your toolset etc )
2. Windows exploitation - Real atacks using metasploit, creating FUD ( Fully UnDetectable ) meterpreter payload and also on vulnerable machines & other online services like vulnhub & hackthebox
3. Hardware attacks like - Bad USB attacks - Practical and where you could get the cheap Hardware
All these will have working updated techniques.
These all will have demo wherever possible, so stay tuned.
Whereas on the channel :
1. Automate your toolset - Script and let machines do the boring work
2. Write your own virus - I wrote in my 2nd year at college, However now the skillsets have improved drastically, so better obfuscation techniques.
3. Linux basics - Since this will help you work more productively.
A lot of exciting things to come.
---------------------------------------------------------------------------------------------------------------------------
#hacking #HackingSimplified #StartHacking #beTheHACR #hackthissite #crypto #cryptography #cipher #enigma #shattered #hash #hashes #encoding #encryption #decryption
#howtobeahacker #hackingCourse #decipher #decryption #bugBounty #bug #bounty #aes #base64 #ASCII
How to hack | How to start hacking | How to start with hacking | Hackthissite |Bug Bounty | BugBounty | Crypto | Cryptography | Hacking Course | Hacking | Hacker | Encryption | ASCII |
Decryption | Encoding | Decoding | base64 | AES | Enigma | WW2 Hack | Simple Hacking | Simplify Hacking | Hacking Simplified | HackingSimplified | Hacking Simplified 42 | HackingSimplified42
In this fourth episode, I would talk about basic cryptography.
First we will understand the basics of cryptography and then move on to the mission.
There we will try understanding the logic of the given crypto and solve it manually.Watch this video till the end to see a trick as to how you could solve it with 5 lines of code in a much faster and reliable way.
Some of the things you'd learn about in this video :
Some ancient cryptography and how it's relevant to the mission
Basics of modern cryptography
Difference between encryption, encoding and hashing.
Also difference between steganography and cryptography
What are hashes, some of it's types and about hash collision attack
Generating hashes locally on your system
How you could verify if the file you downloaded has been tampered with or not ?
How cryptography is keeping this connection, the connection on which you're watching this youtube video, secure.
Then we will close the slides by discussing one of the most famous crypto-fails of all time, the breaking of enigma, which led to turning the tides in favor of Allies during WW2.
During the missions -
Break the cipher manually
Then automate it using python
We will also learn about ASCII coding and know about some other character encoding schemes.
We will wrap today's session with 5 liner python code - no coding background
---------------------------------------------------------------------------------------------------------------------------
Links from the video :
Slides : https://docs.google.com/presentation/d/1Mr77FLnIsswdBPGevZpviXlxeaSGEfKaelrB5HdtISM/
HTS Mission 6 : https://www.hackthissite.org/missions/basic/6/
---------------------------------------------------------------------------------------------------------------------------
---------------------------------------------------------------------------------------------------------------------------
Key Takeaways :
1. Cryptography, or cryptology, is the practice and study of techniques for secure communication in the presence of third parties called adversaries.
2. Difference between Hashing, Encoding, Encryption and Steganography
3. Hashing is used to verify the integrity of files
4. ASCII is one of the many character encoding methods
5. Let machines do the boring work - Automate the boring stuff with code
---------------------------------------------------------------------------------------------------------------------------
Detailed Google FeedBack Form : https://forms.gle/rA9oy5wqN5GSLkh8A
Join the telegram channel to get latest articles related to cybersecurity and hacking : https://t.me/hackingsimplified42
Thank you everyone.
Hope it was worth your time.
---------------------------------------------------------------------------------------------------------------------------
About the Channel :
You would've started or would like to start hacking, wait no more, start here.
You're in the right place.
Hack
Automate
Code
Repeat
Be The H.A.C.R.
This is the first episode in a long series of videos.
This series will include :
1. Web exploitation - Common attack vectors ( OWASP top 10, how to find targets, automating your toolset etc )
2. Windows exploitation - Real atacks using metasploit, creating FUD ( Fully UnDetectable ) meterpreter payload and also on vulnerable machines & other online services like vulnhub & hackthebox
3. Hardware attacks like - Bad USB attacks - Practical and where you could get the cheap Hardware
All these will have working updated techniques.
These all will have demo wherever possible, so stay tuned.
Whereas on the channel :
1. Automate your toolset - Script and let machines do the boring work
2. Write your own virus - I wrote in my 2nd year at college, However now the skillsets have improved drastically, so better obfuscation techniques.
3. Linux basics - Since this will help you work more productively.
A lot of exciting things to come.
---------------------------------------------------------------------------------------------------------------------------
#hacking #HackingSimplified #StartHacking #beTheHACR #hackthissite #crypto #cryptography #cipher #enigma #shattered #hash #hashes #encoding #encryption #decryption
#howtobeahacker #hackingCourse #decipher #decryption #bugBounty #bug #bounty #aes #base64 #ASCII
How to hack | How to start hacking | How to start with hacking | Hackthissite |Bug Bounty | BugBounty | Crypto | Cryptography | Hacking Course | Hacking | Hacker | Encryption | ASCII |
Decryption | Encoding | Decoding | base64 | AES | Enigma | WW2 Hack | Simple Hacking | Simplify Hacking | Hacking Simplified | HackingSimplified | Hacking Simplified 42 | HackingSimplified42
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
772
Likes
33
Duration
20:28
Published
May 22, 2020
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now