Unlocking Anamorphic Cryptography: Baby-Step Giant-Step Recovery Explained 🔐
Discover how the Baby-Step Giant-Step algorithm enhances cryptographic security in anamorphic cryptography. Learn from experts William J. Buchanan and Jamie Gilchrist about the latest breakthroughs in 2022.

Computer Science & IT Conference Proceedings
28 views • Sep 28, 2025
About this video
Anamorphic Cryptography using Baby-Step Giant-Step Recovery
William J. Buchanan, and Jamie Gilchrist, Edinburgh Napier University, UK
Abstract
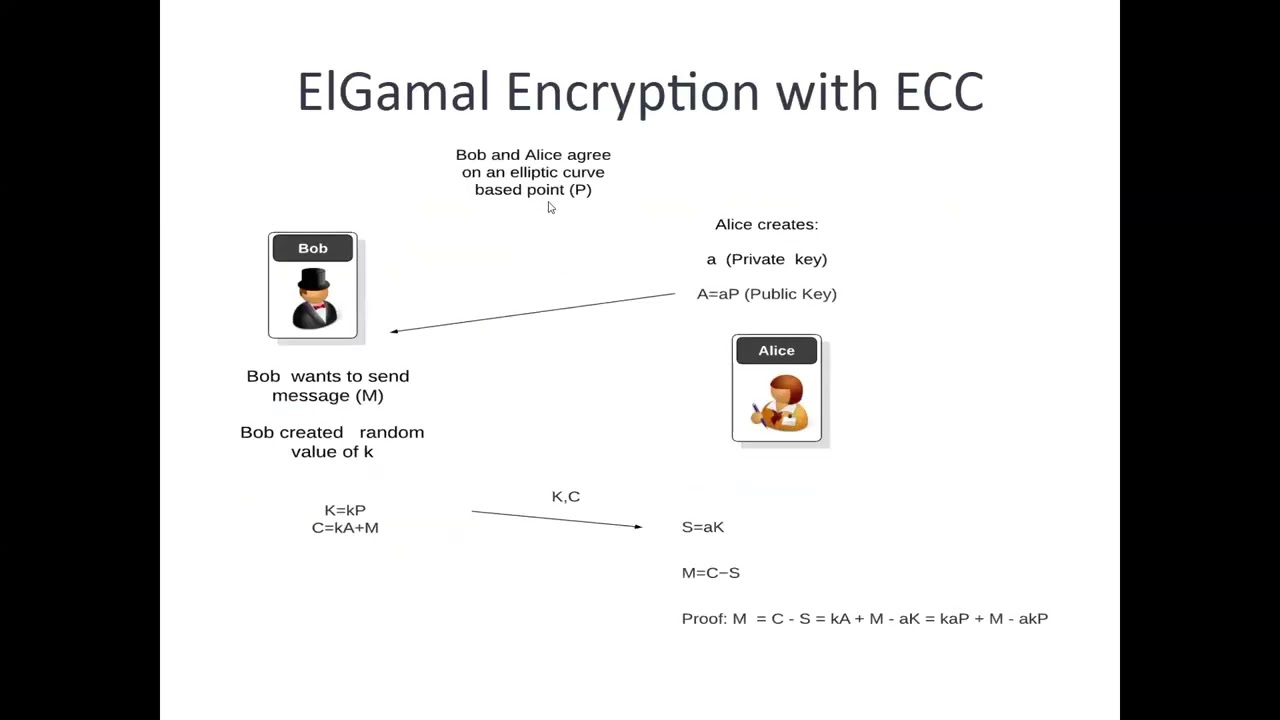
In 2022, Persianom, Phan and Yung outlined the creation of Anamorphic Cryptography. With this, we can create a public key to encrypt data, and then have two secret keys. These secret keys are used to decrypt the cipher into different messages. So, one secret key is given to the Dictator (who must be able to decrypt all the messages), and the other is given to Alice. Alice can then decrypt the ciphertext to a secret message that the Dictator cannot see. This paper outlines the implementation of Anamorphic Cryptography using ECC (Elliptic Curve Cryptography), such as with the secp256k1 curve. This gives considerable performance improvements over discrete logarithm-based methods with regard to security for a particular bit length. Overall, it outlines how the secret message sent to Alice is hidden within the random nonce value, which is used within the encryption process, and which is cancelled out when the Dictator decrypts the ciphertext. It also shows that the BSGS (Baby-step Giant-step) variant significantly outperforms unoptimised elliptic curve methods.
Keywords
Partially Homomorphic Encryption, Fully Homomorphic Encryption, IP subnetting, BFV
Full Text : https://aircconline.com/csit/papers/vol15/csit151704.pdf
Abstract URL: https://aircconline.com/csit/abstract/v15n17/csit151704.html
Volume URL : https://airccse.org/csit/V15N17.html
#cryptography #bfv #encryption #informationsecurity #security #blockchain #cybersecurity
William J. Buchanan, and Jamie Gilchrist, Edinburgh Napier University, UK
Abstract
In 2022, Persianom, Phan and Yung outlined the creation of Anamorphic Cryptography. With this, we can create a public key to encrypt data, and then have two secret keys. These secret keys are used to decrypt the cipher into different messages. So, one secret key is given to the Dictator (who must be able to decrypt all the messages), and the other is given to Alice. Alice can then decrypt the ciphertext to a secret message that the Dictator cannot see. This paper outlines the implementation of Anamorphic Cryptography using ECC (Elliptic Curve Cryptography), such as with the secp256k1 curve. This gives considerable performance improvements over discrete logarithm-based methods with regard to security for a particular bit length. Overall, it outlines how the secret message sent to Alice is hidden within the random nonce value, which is used within the encryption process, and which is cancelled out when the Dictator decrypts the ciphertext. It also shows that the BSGS (Baby-step Giant-step) variant significantly outperforms unoptimised elliptic curve methods.
Keywords
Partially Homomorphic Encryption, Fully Homomorphic Encryption, IP subnetting, BFV
Full Text : https://aircconline.com/csit/papers/vol15/csit151704.pdf
Abstract URL: https://aircconline.com/csit/abstract/v15n17/csit151704.html
Volume URL : https://airccse.org/csit/V15N17.html
#cryptography #bfv #encryption #informationsecurity #security #blockchain #cybersecurity
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
28
Duration
32:56
Published
Sep 28, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.