Understanding Symmetric & Asymmetric Cryptography: Key Generation, Encryption & Decryption 🛡️
Learn clear examples of how symmetric and asymmetric cryptography work, including key generation, encryption, and decryption processes for enhanced data security.

Cryptography & Cyber Security Solutions
63 views • Jan 6, 2018
About this video
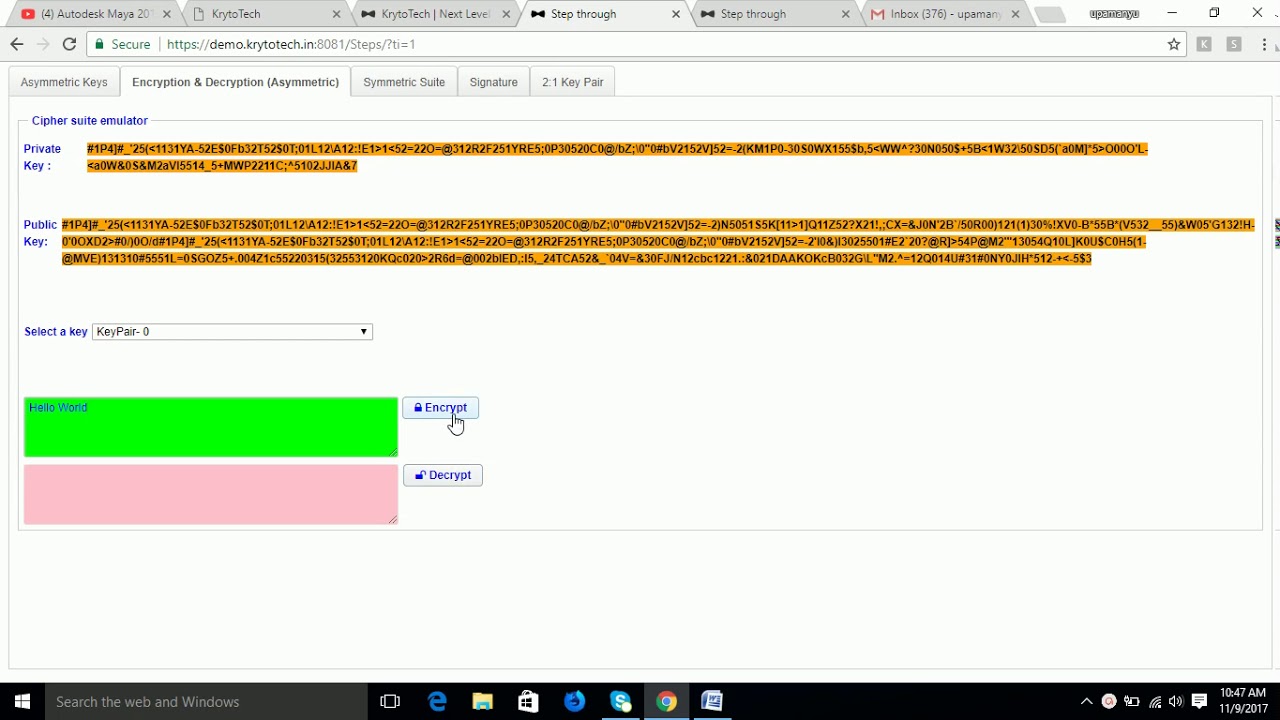
Example of Symmetric and Asymmetric Cryptography key Generation Encryption and Decryption
Video Information
Views
63
Duration
0:59
Published
Jan 6, 2018
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.