Understanding Network Security: The DES and 3DES Encryption Algorithms 🔐
Learn the fundamentals of network security with a focus on the DES and 3DES encryption algorithms. Perfect for students and professionals aiming to strengthen their cybersecurity knowledge. Educational content based on expert references.

Aleesa Ali
85 views • May 31, 2021
About this video
Disclaimer : This video is for education purpose.
References:
Introduction:
Christof Parr, Jan Pelzl., 2014. The Data Encrpytion Standard (DES) and Alternatives. Understanding Cryptography. Springer. 56.
Initial permutation:
Saikumar, I., 2017. DES-Data Encryption Standard. International Research Journal of Engineering and Technology, 4(3). (Su)
Key Transformation:
GeeksforGeeks. (2020, April 3). Data encryption standard (DES) | Set 1. https://www.geeksforgeeks.org/data-encryption-standard-des-set-1/
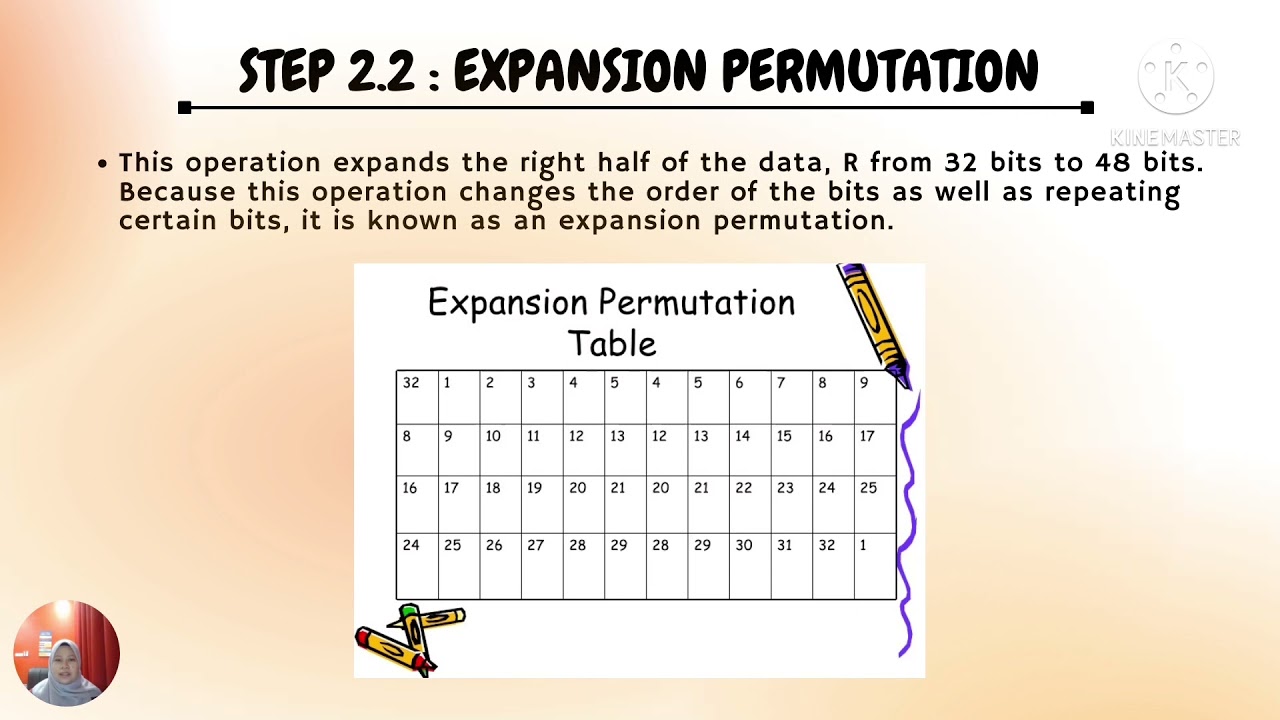
Expansion Permutation:
Noor Dhia Kadhm Al-Shakarchy
Journal of Kerbala University 10 (4), 13-21, 2012 (Zati)
S-Box permutation:
Christof Parr, Jan Pelzl., 2014. The Data Encrpytion Standard (DES) and Alternatives. Understanding Cryptography. Springer.
P-Box Permutation:
Zobeiri, M. and Maybodi, B.M.N., 2017. Introducing dynamic P-Box and S-Box based on modular calculation and key encryption for adding to current cryptographic systems against the linear and differential cryptanalysis. ARPN Journal of Engineering and Applied Sciences, 12, pp.856-862.
XOR and Swap:
Bhattacharya, S. (2016, October 16). Cryptography - Data Encryption System (DES). C#Corner. https://www.c-sharpcorner.com/article/cryptography-data-encryption-standard-des/
Final Permutation:
Saikumar, I., 2017. DES-Data Encryption Standard. International Research Journal of Engineering and Technology, 4(3).
3Des:
Zobeiri, M. and Maybodi, B.M.N., 2017. Introducing dynamic P-Box and S-Box based on modular calculation and key encryption for adding to current cryptographic systems against the linear and differential cryptanalysis. ARPN Journal of Engineering and Applied Sciences, 12, pp.856-862.
Conclusion:
Noor Dhia Kadhm Al-Shakarchy
Journal of Kerbala University 10 (4), 13-21, 2012 (Zati)
References:
Introduction:
Christof Parr, Jan Pelzl., 2014. The Data Encrpytion Standard (DES) and Alternatives. Understanding Cryptography. Springer. 56.
Initial permutation:
Saikumar, I., 2017. DES-Data Encryption Standard. International Research Journal of Engineering and Technology, 4(3). (Su)
Key Transformation:
GeeksforGeeks. (2020, April 3). Data encryption standard (DES) | Set 1. https://www.geeksforgeeks.org/data-encryption-standard-des-set-1/
Expansion Permutation:
Noor Dhia Kadhm Al-Shakarchy
Journal of Kerbala University 10 (4), 13-21, 2012 (Zati)
S-Box permutation:
Christof Parr, Jan Pelzl., 2014. The Data Encrpytion Standard (DES) and Alternatives. Understanding Cryptography. Springer.
P-Box Permutation:
Zobeiri, M. and Maybodi, B.M.N., 2017. Introducing dynamic P-Box and S-Box based on modular calculation and key encryption for adding to current cryptographic systems against the linear and differential cryptanalysis. ARPN Journal of Engineering and Applied Sciences, 12, pp.856-862.
XOR and Swap:
Bhattacharya, S. (2016, October 16). Cryptography - Data Encryption System (DES). C#Corner. https://www.c-sharpcorner.com/article/cryptography-data-encryption-standard-des/
Final Permutation:
Saikumar, I., 2017. DES-Data Encryption Standard. International Research Journal of Engineering and Technology, 4(3).
3Des:
Zobeiri, M. and Maybodi, B.M.N., 2017. Introducing dynamic P-Box and S-Box based on modular calculation and key encryption for adding to current cryptographic systems against the linear and differential cryptanalysis. ARPN Journal of Engineering and Applied Sciences, 12, pp.856-862.
Conclusion:
Noor Dhia Kadhm Al-Shakarchy
Journal of Kerbala University 10 (4), 13-21, 2012 (Zati)
Video Information
Views
85
Likes
10
Duration
13:02
Published
May 31, 2021
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.