Understanding Asymmetric Cryptography: The Key to Secure Communication 🔐
Discover the fundamentals of Asymmetric Cryptography and how it ensures secure data exchange. Perfect for cybersecurity enthusiasts and beginners alike!

CYBERIQ BY ROSHAN
62 views • Jul 11, 2025
About this video
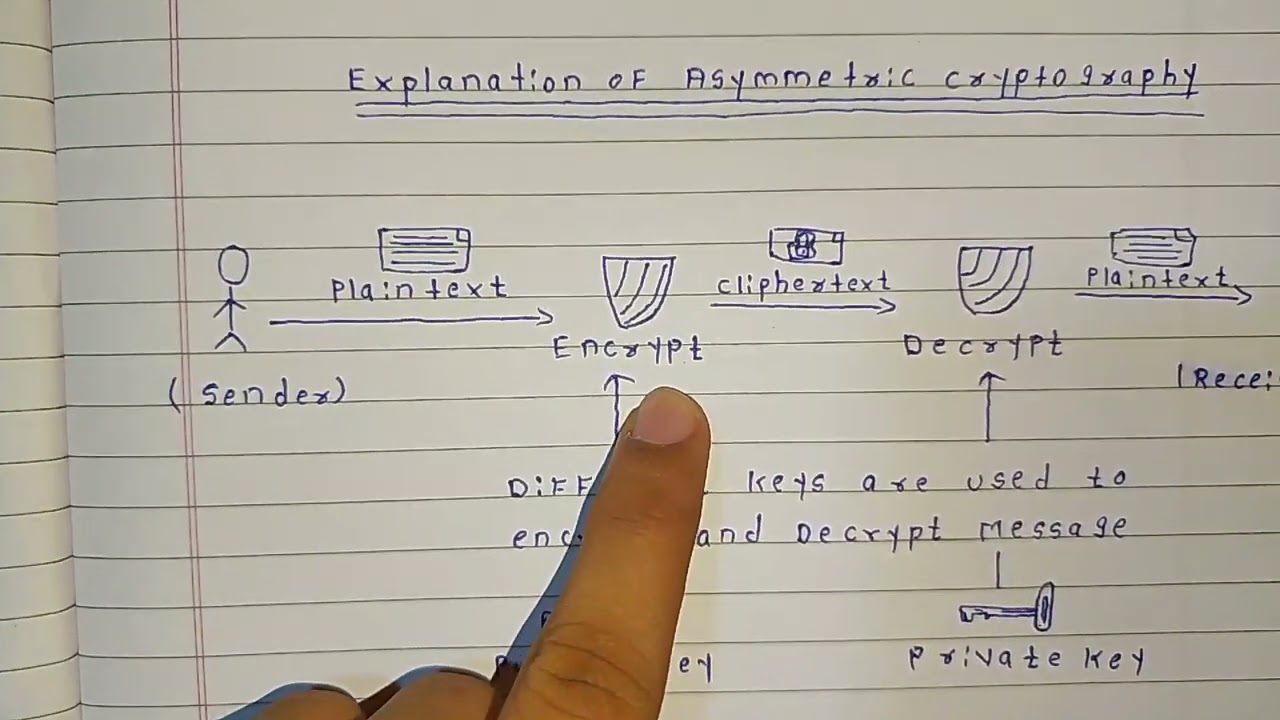
🔐 What is Asymmetric Cryptography? 🔐
Welcome to Cyber IQ by Roshan! In this video, we explore Asymmetric Cryptography—a key concept in cyber security. Unlike symmetric encryption, this method uses two keys: a public key to encrypt and a private key to decrypt. It’s the backbone of secure communication, digital signatures, and online privacy. From WhatsApp messages to secure banking, asymmetric encryption is everywhere! 🛡️
Whether you're a beginner or brushing up for competitive exams, this video simplifies the concept with real-life examples.
📺 Watch now and level up your Cyber IQ!
#CyberSecurity #AsymmetricCryptography #CyberIQbyRoshan
THANK YOU 😊
Welcome to Cyber IQ by Roshan! In this video, we explore Asymmetric Cryptography—a key concept in cyber security. Unlike symmetric encryption, this method uses two keys: a public key to encrypt and a private key to decrypt. It’s the backbone of secure communication, digital signatures, and online privacy. From WhatsApp messages to secure banking, asymmetric encryption is everywhere! 🛡️
Whether you're a beginner or brushing up for competitive exams, this video simplifies the concept with real-life examples.
📺 Watch now and level up your Cyber IQ!
#CyberSecurity #AsymmetricCryptography #CyberIQbyRoshan
THANK YOU 😊
Video Information
Views
62
Likes
12
Duration
3:42
Published
Jul 11, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now