Understanding Active Attacks in Cybersecurity 🔒 | Quick Explanation with Examples
Discover what active attacks are, how they differ from passive attacks, and why they pose a significant threat to your systems and data. Watch this short for clear insights and real-world examples!

Security For You
460 views • Jun 14, 2025
About this video
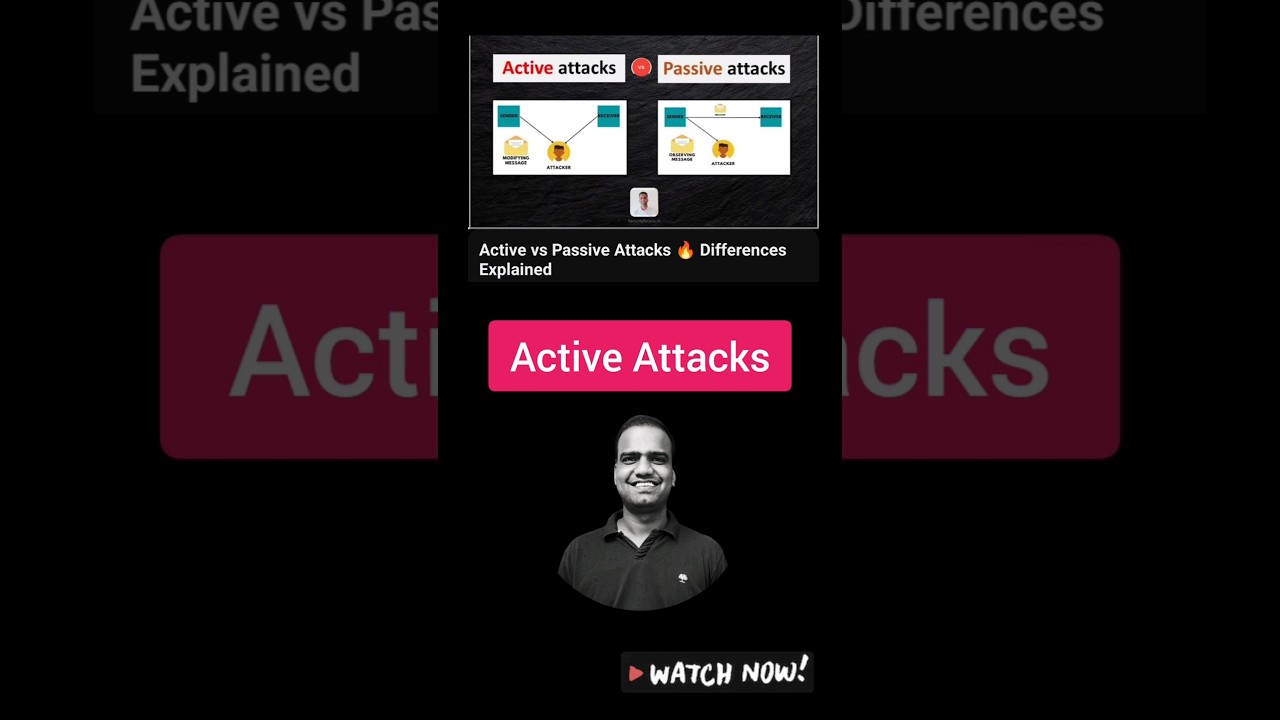
In this quick cybersecurity short, we explain what active attacks are and why they pose a serious threat to systems and data.
Unlike passive attacks that only observe or monitor, active attacks involve direct interference with system operations. Attackers don’t just watch — they act.
For instance, imagine an online banking transaction. If a cybercriminal intercepts and modifies a money transfer request, redirecting the funds to their own account, that's a clear example of an active attack.
These types of attacks are usually detectable, as they cause visible changes or disruptions in system behavior, such as altered data, denied access, or system crashes.
This video is ideal for anyone interested in cybersecurity fundamentals, ethical hacking, or information security awareness.
Whether you're a beginner, a student, or an IT professional brushing up your knowledge, this short will help you understand a crucial cybersecurity concept in under 60 seconds.
📌 Don't forget to like, comment, and subscribe for more quick cybersecurity explainers and real-world examples!
Watch full video on active and passive attacks -
https://youtu.be/B89i747yC4A
#ActiveAttack #CyberSecurityBasics #EthicalHacking #InfoSec #CyberThreats #CyberAwareness #DataProtection #CyberSecurityTips #CyberAttackExplained #HackerTactics #DigitalSecurity #OnlineSafety #NetworkSecurity #CyberEssentials #CyberSecurityEducation #ITSecurity #CyberDefense #SystemSecurity #BankingFraud #DigitalThreats #CyberExplained #InternetSecurity #ActiveVsPassiveAttacks #CyberShorts #InfoSecurity101 #HackPrevention #CyberCrimeAwareness #RealLifeCyberAttack #TechShorts #DataBreachAlert
Unlike passive attacks that only observe or monitor, active attacks involve direct interference with system operations. Attackers don’t just watch — they act.
For instance, imagine an online banking transaction. If a cybercriminal intercepts and modifies a money transfer request, redirecting the funds to their own account, that's a clear example of an active attack.
These types of attacks are usually detectable, as they cause visible changes or disruptions in system behavior, such as altered data, denied access, or system crashes.
This video is ideal for anyone interested in cybersecurity fundamentals, ethical hacking, or information security awareness.
Whether you're a beginner, a student, or an IT professional brushing up your knowledge, this short will help you understand a crucial cybersecurity concept in under 60 seconds.
📌 Don't forget to like, comment, and subscribe for more quick cybersecurity explainers and real-world examples!
Watch full video on active and passive attacks -
https://youtu.be/B89i747yC4A
#ActiveAttack #CyberSecurityBasics #EthicalHacking #InfoSec #CyberThreats #CyberAwareness #DataProtection #CyberSecurityTips #CyberAttackExplained #HackerTactics #DigitalSecurity #OnlineSafety #NetworkSecurity #CyberEssentials #CyberSecurityEducation #ITSecurity #CyberDefense #SystemSecurity #BankingFraud #DigitalThreats #CyberExplained #InternetSecurity #ActiveVsPassiveAttacks #CyberShorts #InfoSecurity101 #HackPrevention #CyberCrimeAwareness #RealLifeCyberAttack #TechShorts #DataBreachAlert
Video Information
Views
460
Likes
3
Duration
0:40
Published
Jun 14, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.