Ultimate Guide to Internet Infrastructure Security 🔐
Discover essential strategies to protect internet infrastructure, including telematics and trust issues. Learn how to safeguard digital assets effectively!

Jochen Schiller
106 views • Feb 4, 2024
About this video
00:00 - Telematics Chapter 8 Internet Infrastructure Security
00:07 - Content of this Chapter
00:43 - Content of this Chapter
00:49 - Whom do we trust on the Internet
01:05 - Whom do we trust on the Internet
02:17 - An example of a simple attack
02:37 - An example of a simple attack
02:57 - Who would do harm and why?
03:10 - Content of this Chapter
03:13 - Let’s briefly recap how security works
03:25 - There are different security objectives
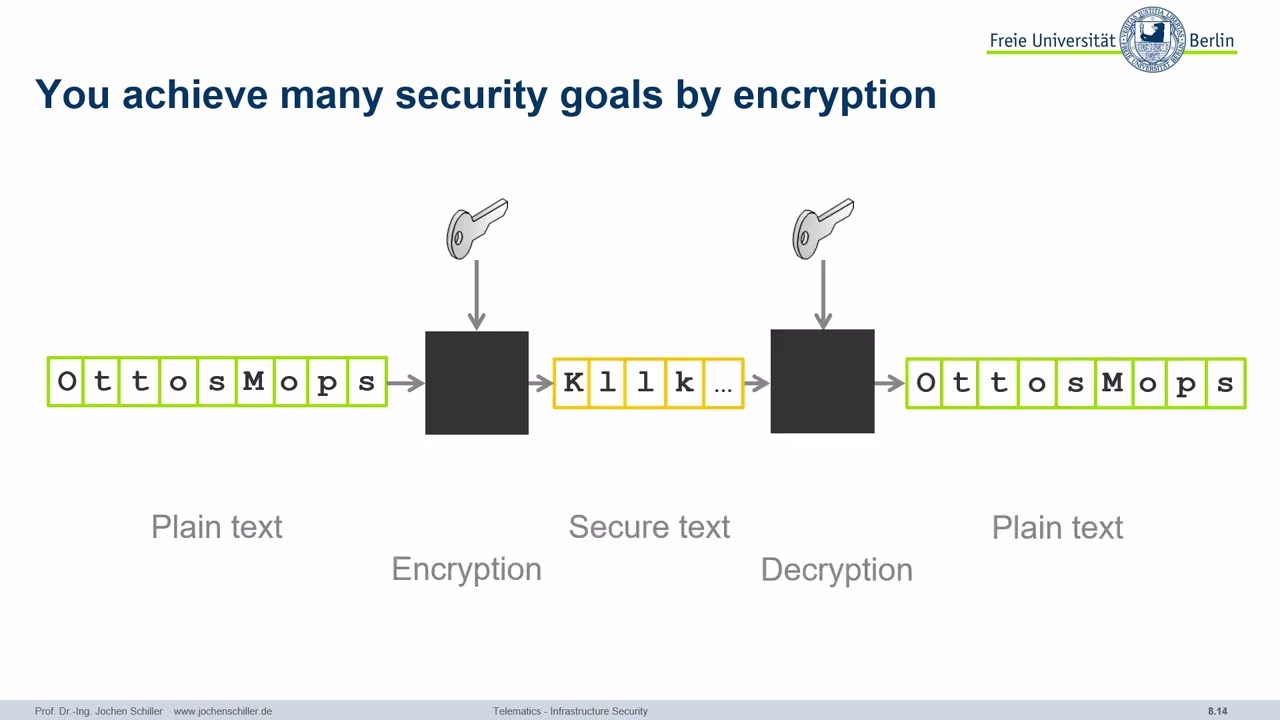
04:02 - You achieve many security goals by encryption
04:06 - You achieve many security goals by encryption
04:09 - You achieve many security goals by encryption
04:16 - You achieve many security goals by encryption
04:56 - Content of this Chapter
05:07 - Symmetric vs. asymmetric cryptography
06:24 - Symmetric vs. asymmetric cryptography
07:18 - Private public key encryption
09:36 - One challenge in public private key crypto is to obtain trust in public key
12:17 - Chain of trust (simplified)
15:39 - Example: Classical E-Mail protection via PGP
22:00 - Questions & Tasks
00:07 - Content of this Chapter
00:43 - Content of this Chapter
00:49 - Whom do we trust on the Internet
01:05 - Whom do we trust on the Internet
02:17 - An example of a simple attack
02:37 - An example of a simple attack
02:57 - Who would do harm and why?
03:10 - Content of this Chapter
03:13 - Let’s briefly recap how security works
03:25 - There are different security objectives
04:02 - You achieve many security goals by encryption
04:06 - You achieve many security goals by encryption
04:09 - You achieve many security goals by encryption
04:16 - You achieve many security goals by encryption
04:56 - Content of this Chapter
05:07 - Symmetric vs. asymmetric cryptography
06:24 - Symmetric vs. asymmetric cryptography
07:18 - Private public key encryption
09:36 - One challenge in public private key crypto is to obtain trust in public key
12:17 - Chain of trust (simplified)
15:39 - Example: Classical E-Mail protection via PGP
22:00 - Questions & Tasks
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
106
Likes
2
Duration
23:12
Published
Feb 4, 2024
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now