Tools and Methods Used in Cybercrime Part 3 | Dr. Reshma Kadam
This video discusses various tools and techniques employed in cybercrime, including keyloggers and spyware, different types of keyloggers, and software-based keyloggers.

Reshma Patil
353 views • Jan 20, 2022
About this video
This video contains information about:
- Tools and Methods Used in Cybercrime
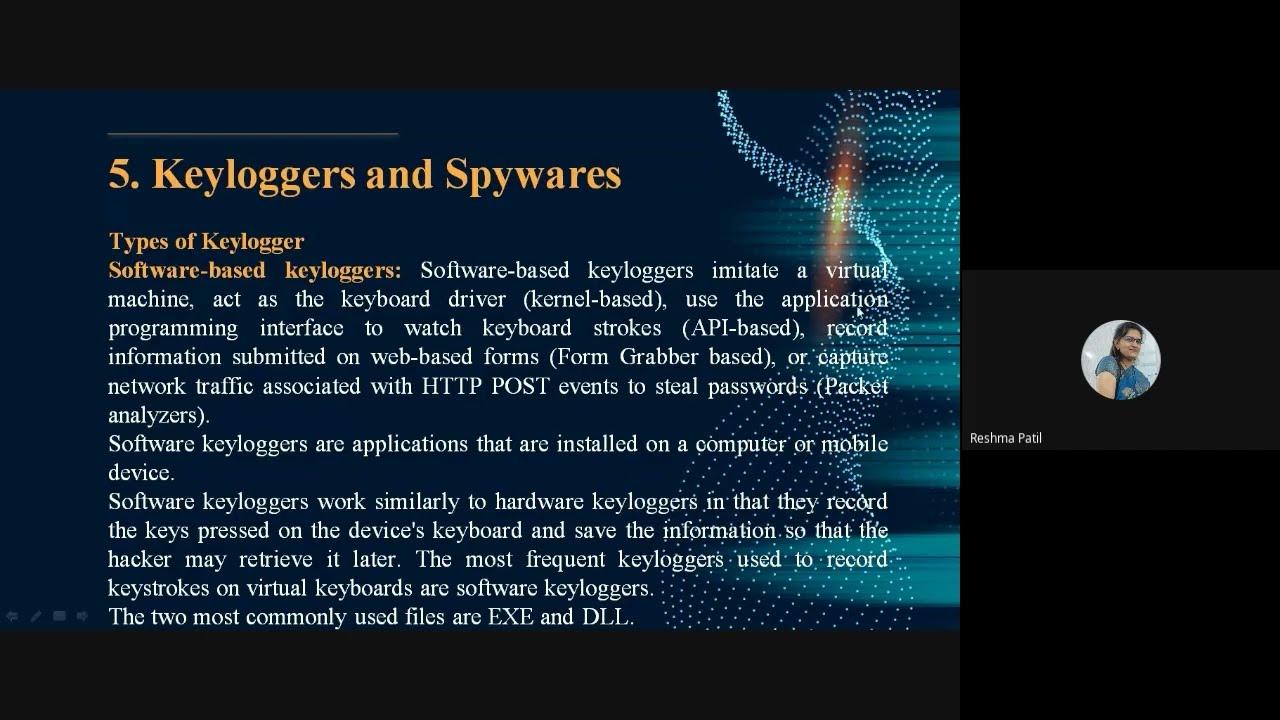
- Keylogger and Spywares
- Types of Keyloggers
- Software-based Keyloggers
- Hardware-based Keyloggers
- Acoustic Keylogging
- Antikeylogger
- Benefits of Antikeylogger
- Spywares
- Virus and Worms
- Viruses
- Worms
- Countermeasures for viruses and worms
- Tojan Horses
- Backdoors
- Tojan Horses and Backdoors
- Functions of Backdoors
- Tips to protect from Trojan Horses and Backdoors
- Difference between Trojan , Virus and Worm
- Tools and Methods Used in Cybercrime
- Keylogger and Spywares
- Types of Keyloggers
- Software-based Keyloggers
- Hardware-based Keyloggers
- Acoustic Keylogging
- Antikeylogger
- Benefits of Antikeylogger
- Spywares
- Virus and Worms
- Viruses
- Worms
- Countermeasures for viruses and worms
- Tojan Horses
- Backdoors
- Tojan Horses and Backdoors
- Functions of Backdoors
- Tips to protect from Trojan Horses and Backdoors
- Difference between Trojan , Virus and Worm
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
353
Likes
4
Duration
43:01
Published
Jan 20, 2022
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.