Timing Attack: Speeding Through Secure Connections ⏳
Learn how timing attacks exploit connection durations to breach security in just minutes. Understand and defend against them!

Quick Cybersecurity Study
611 views • Mar 14, 2025
About this video
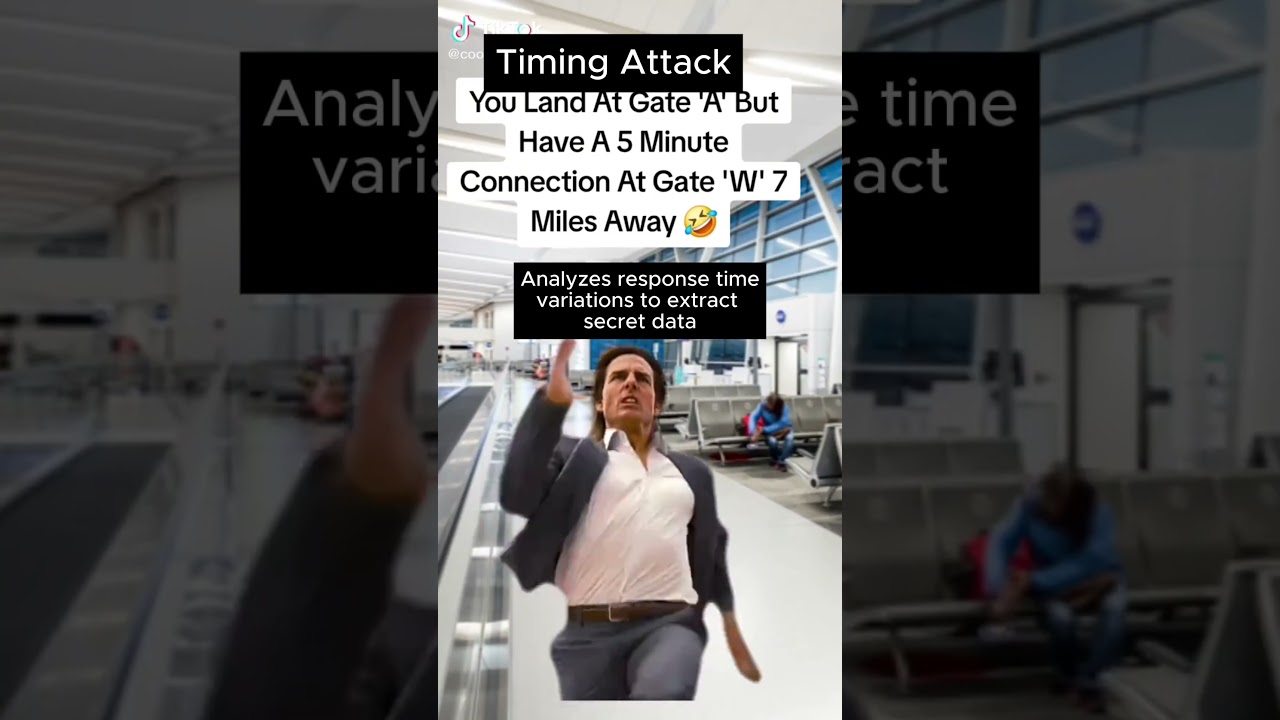
⏳ **Timing Attack in Side-Channel & Secure by Design = Rushing for a 5-Minute Connection from Gate A to Gate W!** 🔐✨
Just like tracking how long it takes to get from one gate to another, **Timing Attacks** analyze the time taken by cryptographic operations to extract sensitive information. 💻⚠️
With **Secure by Design**, constant-time algorithms and timing obfuscation help prevent these attacks! ✅🔐
#CyberSecurity #TimingAttack #SideChannelAttack #Cryptanalysis #SecureByDesign #CyberDefense #InfoSec #TechEducation #CyberSecTraining #VisualLearning #CyberSecurityCertification #ITKnowledge #TechForBeginners #LearnCyberSecurity #SecurityAwareness #CyberSecCommunity
Just like tracking how long it takes to get from one gate to another, **Timing Attacks** analyze the time taken by cryptographic operations to extract sensitive information. 💻⚠️
With **Secure by Design**, constant-time algorithms and timing obfuscation help prevent these attacks! ✅🔐
#CyberSecurity #TimingAttack #SideChannelAttack #Cryptanalysis #SecureByDesign #CyberDefense #InfoSec #TechEducation #CyberSecTraining #VisualLearning #CyberSecurityCertification #ITKnowledge #TechForBeginners #LearnCyberSecurity #SecurityAwareness #CyberSecCommunity
Video Information
Views
611
Likes
5
Duration
0:09
Published
Mar 14, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now