Symmetric vs Asymmetric Encryption: Key Differences Explained 🔐
Discover the essential differences between symmetric and asymmetric encryption to boost your CISSP prep. Perfect for quick crypto insights! #CyberSecShorts

Cyber Security Learning
420 views • Jun 9, 2025
About this video
Symmetric vs Asymmetric Encryption Explained | Learn the Crypto Essentials for CISSP Success #CyberSecShorts
Welcome to this high-impact CISSP Flashcard Short where we decode one of the most fundamental yet essential topics in cybersecurity: Encryption, and more specifically, the key differences between Symmetric and Asymmetric encryption systems. Understanding this distinction is critical for CISSP candidates and cybersecurity professionals alike, as it's foundational to secure communication, data confidentiality, and authentication systems worldwide.
🔐 What Is Encryption and Why Does It Matter?
Encryption is the process of converting plaintext into unreadable ciphertext to prevent unauthorized access. The CISSP exam will test not only your understanding of encryption fundamentals but also your ability to apply them in practical security scenarios.
There are two primary types of encryption:
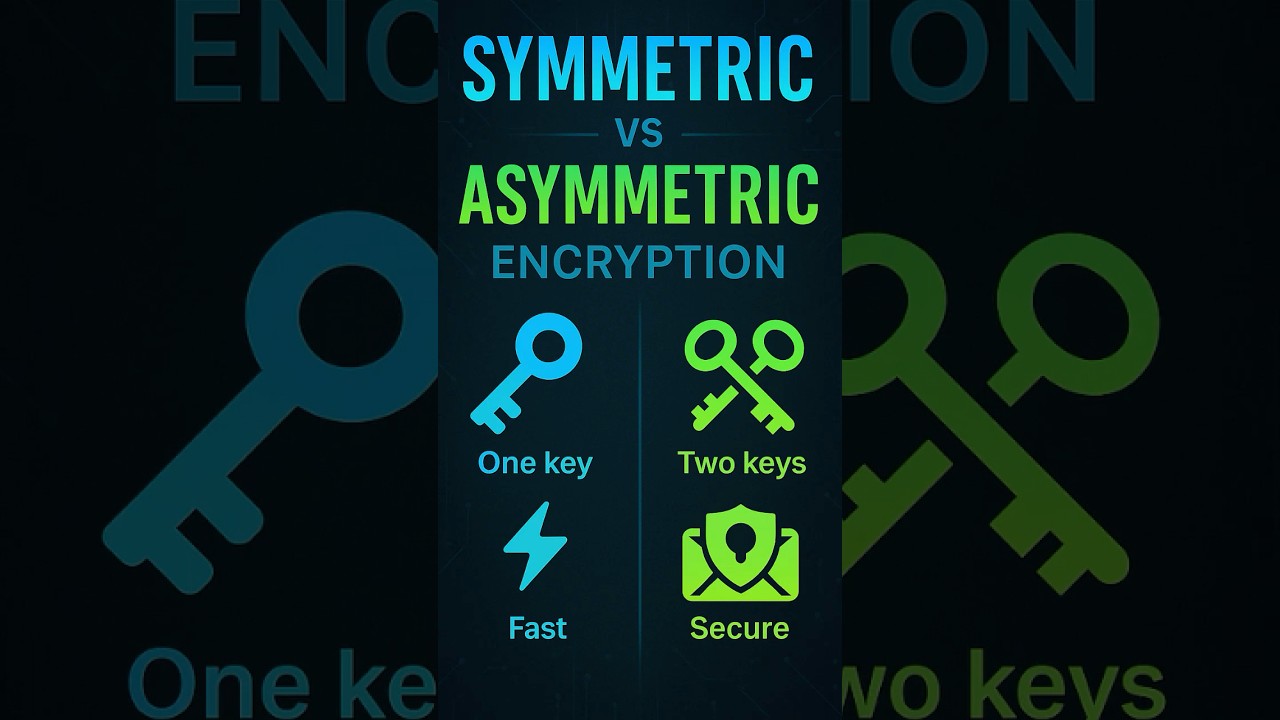
Symmetric Encryption – One key to encrypt and decrypt.
Asymmetric Encryption – Two keys: public and private.
Each has its own advantages, use cases, and vulnerabilities. Let’s break it down.
✅ Symmetric Encryption: Fast and Efficient
One Key Only: The same key is used for both encryption and decryption.
Speed: It's faster and less resource-intensive—ideal for encrypting large amounts of data.
Use Cases:
Disk encryption
VPN tunnels (e.g., IPSec)
Secure backups
Internal data protection
Examples:
AES (Advanced Encryption Standard)
DES, 3DES
Blowfish, Twofish, RC5, RC6
Pros:
High speed and efficiency
Strong for large data volumes
Cons:
Key distribution is a challenge
If one person loses the key—security is compromised
🔑 Asymmetric Encryption: Secure Communication at a Distance
Two Keys: Public key (to encrypt) and private key (to decrypt).
Security Model: You don’t need to share a private key—making it ideal for open communication.
Use Cases:
Secure email (e.g., PGP)
TLS/SSL handshakes
Digital signatures
Secure key exchanges (e.g., Diffie-Hellman)
Examples:
RSA
ECC (Elliptic Curve Cryptography)
Diffie-Hellman
DSA, El Gamal
Pros:
Solves the key exchange problem
Enables authentication and non-repudiation
Cons:
Slower and more computationally intensive
Less suitable for encrypting large data
🧠 CISSP Exam Tip:
Understand the hybrid model used in most secure systems:
Asymmetric encryption is used to exchange a symmetric key.
The symmetric key is then used for bulk encryption during a secure session (e.g., HTTPS).
📚 Real-World Applications of Encryption
E-commerce: Your credit card details are protected by asymmetric key exchange and symmetric session encryption.
Secure Messaging Apps: Use end-to-end encryption powered by asymmetric cryptography, with session keys derived via symmetric algorithms.
Cloud Storage: Data is encrypted symmetrically at rest and shared securely using asymmetric encryption.
🎯 CISSP Domain Alignment
This topic is featured in multiple CISSP domains:
Domain 3: Security Architecture and Engineering
Domain 5: Identity and Access Management (IAM)
Domain 8: Software Development Security
📌 Quick Comparison Table:
Feature Symmetric Asymmetric
Keys Used One shared key Public and private key
Speed Fast Slower
Use Case Bulk data encryption Key exchange, identity
Example Algorithms AES, DES, RC6 RSA, ECC, DSA
💡 Important Concepts to Remember:
Symmetric = Speed, simplicity, performance
Asymmetric = Secure sharing, authentication, key exchange
Hybrid systems use both for maximum effectiveness
🏆 Who Should Watch This Short?
CISSP candidates
Cybersecurity students
Infosec analysts
Network engineers
Security architects
IT managers & consultants
#CISSP #Encryption #CyberSecurity #SymmetricVsAsymmetric #CryptoBasics #SecurityFundamentals #InfoSec #CISSPFlashcards #SecureCommunication #ExamPrep #FlashcardShort #CyberEducation
Welcome to this high-impact CISSP Flashcard Short where we decode one of the most fundamental yet essential topics in cybersecurity: Encryption, and more specifically, the key differences between Symmetric and Asymmetric encryption systems. Understanding this distinction is critical for CISSP candidates and cybersecurity professionals alike, as it's foundational to secure communication, data confidentiality, and authentication systems worldwide.
🔐 What Is Encryption and Why Does It Matter?
Encryption is the process of converting plaintext into unreadable ciphertext to prevent unauthorized access. The CISSP exam will test not only your understanding of encryption fundamentals but also your ability to apply them in practical security scenarios.
There are two primary types of encryption:
Symmetric Encryption – One key to encrypt and decrypt.
Asymmetric Encryption – Two keys: public and private.
Each has its own advantages, use cases, and vulnerabilities. Let’s break it down.
✅ Symmetric Encryption: Fast and Efficient
One Key Only: The same key is used for both encryption and decryption.
Speed: It's faster and less resource-intensive—ideal for encrypting large amounts of data.
Use Cases:
Disk encryption
VPN tunnels (e.g., IPSec)
Secure backups
Internal data protection
Examples:
AES (Advanced Encryption Standard)
DES, 3DES
Blowfish, Twofish, RC5, RC6
Pros:
High speed and efficiency
Strong for large data volumes
Cons:
Key distribution is a challenge
If one person loses the key—security is compromised
🔑 Asymmetric Encryption: Secure Communication at a Distance
Two Keys: Public key (to encrypt) and private key (to decrypt).
Security Model: You don’t need to share a private key—making it ideal for open communication.
Use Cases:
Secure email (e.g., PGP)
TLS/SSL handshakes
Digital signatures
Secure key exchanges (e.g., Diffie-Hellman)
Examples:
RSA
ECC (Elliptic Curve Cryptography)
Diffie-Hellman
DSA, El Gamal
Pros:
Solves the key exchange problem
Enables authentication and non-repudiation
Cons:
Slower and more computationally intensive
Less suitable for encrypting large data
🧠 CISSP Exam Tip:
Understand the hybrid model used in most secure systems:
Asymmetric encryption is used to exchange a symmetric key.
The symmetric key is then used for bulk encryption during a secure session (e.g., HTTPS).
📚 Real-World Applications of Encryption
E-commerce: Your credit card details are protected by asymmetric key exchange and symmetric session encryption.
Secure Messaging Apps: Use end-to-end encryption powered by asymmetric cryptography, with session keys derived via symmetric algorithms.
Cloud Storage: Data is encrypted symmetrically at rest and shared securely using asymmetric encryption.
🎯 CISSP Domain Alignment
This topic is featured in multiple CISSP domains:
Domain 3: Security Architecture and Engineering
Domain 5: Identity and Access Management (IAM)
Domain 8: Software Development Security
📌 Quick Comparison Table:
Feature Symmetric Asymmetric
Keys Used One shared key Public and private key
Speed Fast Slower
Use Case Bulk data encryption Key exchange, identity
Example Algorithms AES, DES, RC6 RSA, ECC, DSA
💡 Important Concepts to Remember:
Symmetric = Speed, simplicity, performance
Asymmetric = Secure sharing, authentication, key exchange
Hybrid systems use both for maximum effectiveness
🏆 Who Should Watch This Short?
CISSP candidates
Cybersecurity students
Infosec analysts
Network engineers
Security architects
IT managers & consultants
#CISSP #Encryption #CyberSecurity #SymmetricVsAsymmetric #CryptoBasics #SecurityFundamentals #InfoSec #CISSPFlashcards #SecureCommunication #ExamPrep #FlashcardShort #CyberEducation
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
420
Duration
0:53
Published
Jun 9, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.