Signature-Based IDS Explained: Types & How They Protect Your Network 🔒
Discover the fundamentals of signature-based intrusion detection systems, explore their different types, and learn how they safeguard your cybersecurity infrastructure.

TRN CSE Tutorials
51 views • Jun 22, 2025
About this video
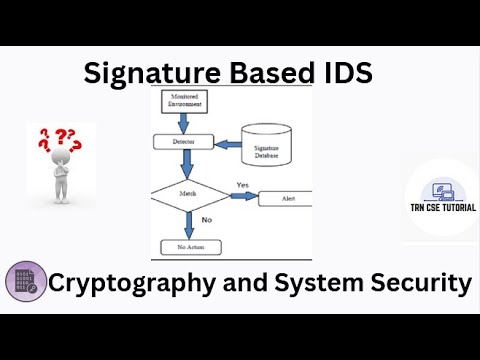
Learn all about signature based intrusion detection systems in this video! Understand the different types of IDS and how they help protect against cyber threats. #cryptography
Like 👍 Share and Subscribe my channel:
TRN CSE TUTORIAL
https://shorturl.at/bICq0
👇 Watch full playlist
Microprocessor 8086, ALP, 8255
https://www.youtube.com/playlist?list=PLSIm6F6G8CqaEvKYZUNa5EjoFQ8RTXhH8
Mumbai University Solved Microprocessor Questions
https://www.youtube.com/playlist?list=PLSIm6F6G8Cqa7Iz45sKBLWykEsT7MOQlD
Cryptography and System Security
https://www.youtube.com/playlist?list=PLSIm6F6G8CqbTvKstfF9vV10CkvmI_zpQ
Like 👍 Share and Subscribe my channel:
TRN CSE TUTORIAL
https://shorturl.at/bICq0
👇 Watch full playlist
Microprocessor 8086, ALP, 8255
https://www.youtube.com/playlist?list=PLSIm6F6G8CqaEvKYZUNa5EjoFQ8RTXhH8
Mumbai University Solved Microprocessor Questions
https://www.youtube.com/playlist?list=PLSIm6F6G8Cqa7Iz45sKBLWykEsT7MOQlD
Cryptography and System Security
https://www.youtube.com/playlist?list=PLSIm6F6G8CqbTvKstfF9vV10CkvmI_zpQ
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
51
Likes
2
Duration
1:52
Published
Jun 22, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.