ShmooCon 2025: Uncovering Covert Channels in QUIC Protocol Headers 🔍
Join David Cheeseman at ShmooCon 2025 as he reveals how to detect and exploit covert communication channels within QUIC protocol headers. Don't miss this insightful session on advanced cybersecurity techniques!

David Cheeseman
102 views • Mar 22, 2025
About this video
Presented by David Cheeseman in the Built It track of ShmooCon 2025, the final ShmooCon for the convention series.
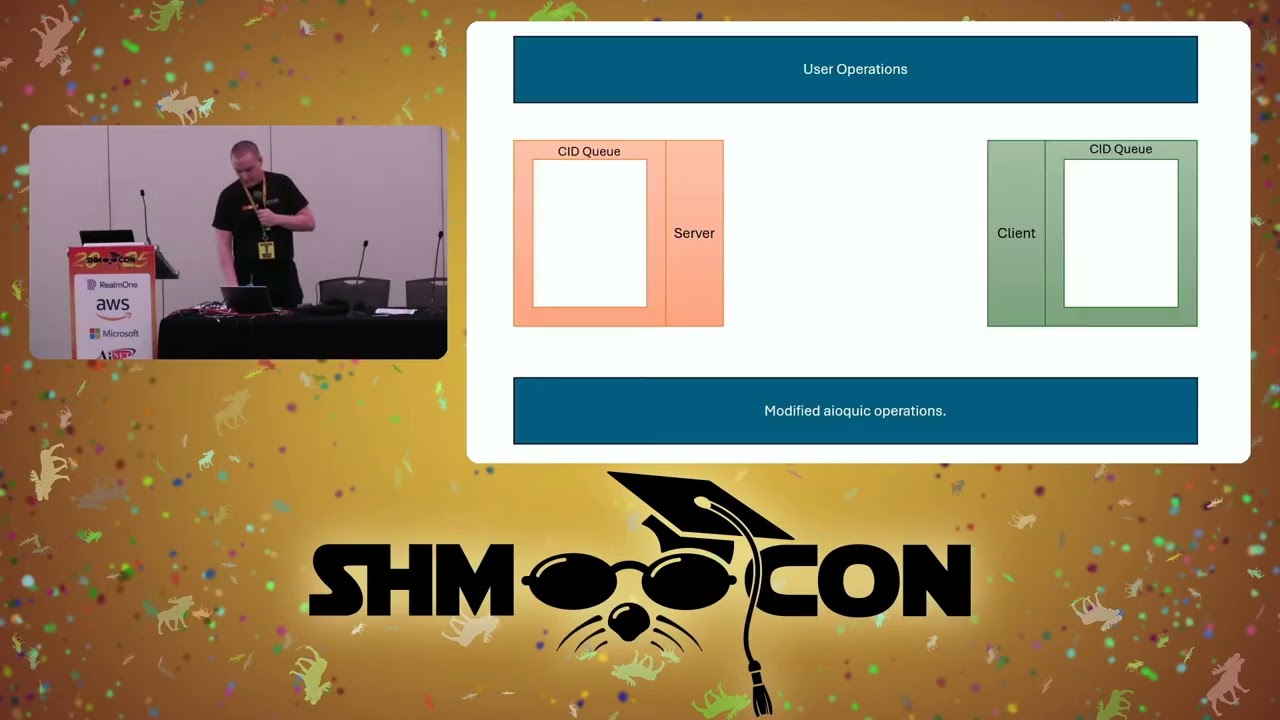
This presentation explores a covert communication channel leveraging high-entropy fields in the QUIC protocol headers. With fields like connection IDs and address validation tokens, QUIC provides an ideal platform for creating channels that evade detection while conforming to protocol entropy requirements. By implementing encryption techniques and leveraging the aioquic library, this work demonstrates covert communication feasibility and discusses potential detection and mitigation strategies. This research provides critical insights into protocol exploitation by leveraging high entropy fields.
David Cheeseman is a US Navy Veteran and cybersecurity professional with experience ranging from AI startups, government contractors, and fortune 50 companies where he’s currently employed. As a US Navy Veteran, he served as a Submarine Officer and Information Professional officer working with nuclear reactors, radio, cryptography, and networking. On the blue team side, he managed cybersecurity for 2 startups, one of which was a government contractor, and later worked in a fortune 50 helping to maintain services which scanned 900k+ assets internally. On the red team side, he studies Cybersecurity at Johns Hopkins University with a focus on Red Team subjects and participate in CTF competitions where he’s made podium placements in small teams and solo competitions.
Code for this project can be found here:
https://github.com/nuvious/quicc
This presentation explores a covert communication channel leveraging high-entropy fields in the QUIC protocol headers. With fields like connection IDs and address validation tokens, QUIC provides an ideal platform for creating channels that evade detection while conforming to protocol entropy requirements. By implementing encryption techniques and leveraging the aioquic library, this work demonstrates covert communication feasibility and discusses potential detection and mitigation strategies. This research provides critical insights into protocol exploitation by leveraging high entropy fields.
David Cheeseman is a US Navy Veteran and cybersecurity professional with experience ranging from AI startups, government contractors, and fortune 50 companies where he’s currently employed. As a US Navy Veteran, he served as a Submarine Officer and Information Professional officer working with nuclear reactors, radio, cryptography, and networking. On the blue team side, he managed cybersecurity for 2 startups, one of which was a government contractor, and later worked in a fortune 50 helping to maintain services which scanned 900k+ assets internally. On the red team side, he studies Cybersecurity at Johns Hopkins University with a focus on Red Team subjects and participate in CTF competitions where he’s made podium placements in small teams and solo competitions.
Code for this project can be found here:
https://github.com/nuvious/quicc
Video Information
Views
102
Likes
1
Duration
17:43
Published
Mar 22, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now