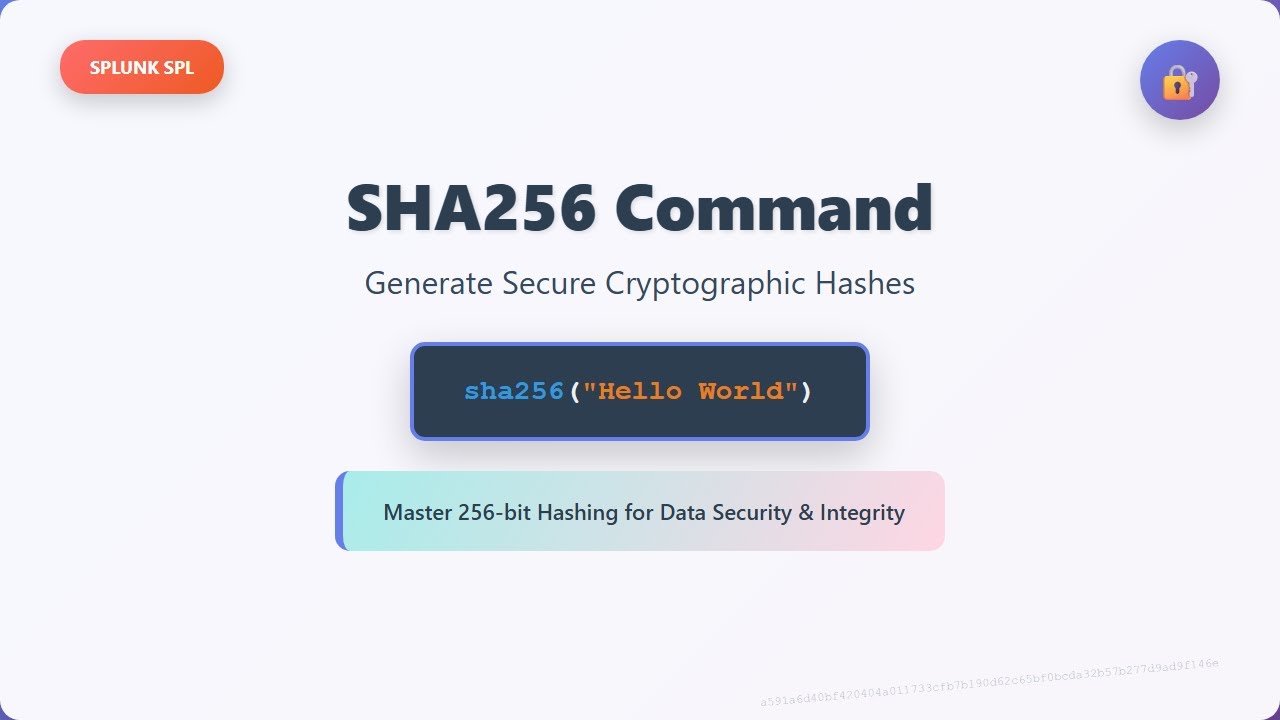
SHA256 Command in Splunk SPL - Generating Secure Cryptographic Hashes
Learn how to use the SHA256 command in Splunk SPL to generate secure 256-bit cryptographic hashes. This tutorial provides a comprehensive overview of the command and its applications.

CodeLucky
11 views • Sep 19, 2025
About this video
🔐 Master the SHA256 command in Splunk SPL for generating secure 256-bit cryptographic hashes! This comprehensive tutorial covers everything you need to know about implementing SHA256 hashing in your Splunk searches.
✨ What You'll Learn:
• SHA256 fundamentals and cryptographic principles
• Basic syntax for string and field inputs
• Real-world examples for password security
• Data integrity verification techniques
• Deduplication strategies using hash values
• Practical audit trail implementation
🎯 Perfect for beginners and intermediate Splunk users looking to enhance their data security skills. Learn how to protect sensitive information, verify file integrity, and identify duplicate records using SHA256 hashing.
💡 Key Topics Covered:
• Secure Hash Algorithm 256-bit overview
• String literal and field value hashing
• Password verification workflows
• File checksum generation
• Duplicate detection methods
• Security best practices
🚀 Take your Splunk SPL skills to the next level with cryptographic hashing techniques that ensure data security and integrity in enterprise environments.
#Splunk #SPL #SHA256 #DataSecurity #CryptographicHashing #SplunkTutorial #DataIntegrity #CyberSecurity #LogAnalysis #codelucky
Chapters:
00:00 - SHA256 Command Introduction
00:26 - What is SHA256?
01:11 - Basic SHA256 Syntax
01:47 - String Input Example
02:35 - Field Input Example
03:21 - Practical Use Cases
04:05 - Real-World Example
04:49 - Key Takeaways
05:35 - Outro
🔗 Stay Connected:
▶️ YouTube: https://youtube.com/@thecodelucky
📱 Instagram: https://instagram.com/thecodelucky
📘 Facebook: https://facebook.com/codeluckyfb
🌐 Website: https://codelucky.com
⭐ Support us by Liking, Subscribing, and Sharing!
💬 Drop your questions in the comments below
🔔 Hit the notification bell to never miss an update
#CodeLucky #WebDevelopment #Programming
✨ What You'll Learn:
• SHA256 fundamentals and cryptographic principles
• Basic syntax for string and field inputs
• Real-world examples for password security
• Data integrity verification techniques
• Deduplication strategies using hash values
• Practical audit trail implementation
🎯 Perfect for beginners and intermediate Splunk users looking to enhance their data security skills. Learn how to protect sensitive information, verify file integrity, and identify duplicate records using SHA256 hashing.
💡 Key Topics Covered:
• Secure Hash Algorithm 256-bit overview
• String literal and field value hashing
• Password verification workflows
• File checksum generation
• Duplicate detection methods
• Security best practices
🚀 Take your Splunk SPL skills to the next level with cryptographic hashing techniques that ensure data security and integrity in enterprise environments.
#Splunk #SPL #SHA256 #DataSecurity #CryptographicHashing #SplunkTutorial #DataIntegrity #CyberSecurity #LogAnalysis #codelucky
Chapters:
00:00 - SHA256 Command Introduction
00:26 - What is SHA256?
01:11 - Basic SHA256 Syntax
01:47 - String Input Example
02:35 - Field Input Example
03:21 - Practical Use Cases
04:05 - Real-World Example
04:49 - Key Takeaways
05:35 - Outro
🔗 Stay Connected:
▶️ YouTube: https://youtube.com/@thecodelucky
📱 Instagram: https://instagram.com/thecodelucky
📘 Facebook: https://facebook.com/codeluckyfb
🌐 Website: https://codelucky.com
⭐ Support us by Liking, Subscribing, and Sharing!
💬 Drop your questions in the comments below
🔔 Hit the notification bell to never miss an update
#CodeLucky #WebDevelopment #Programming
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
11
Duration
5:51
Published
Sep 19, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now