Secure and Reversible Data Hiding in Encrypted JPEG Files 🔒
Discover a novel method for embedding and extracting data seamlessly in encrypted JPEG images without compromising security or image quality. Perfect for privacy-sensitive applications!

ArihantTechnoSolutions ATS
89 views • Sep 23, 2018
About this video
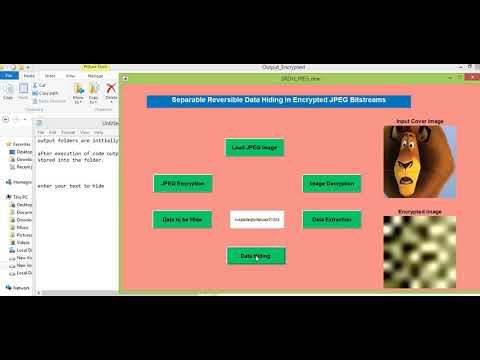
Separable Reversible Data Hiding in Encrypted JPEG Bitstreams
--
For a given JPEG bitstream and an encryption key, the content owner generates a ciphertext bitstream after syntax parsing and encryption. In the process, the file size is kept unchanged and the format is compliant to common JPEG decoders. When a remote server receives the encrypted bitstream, the data hider parses the bitstream and hides additional messages in it using an embedding key. After the marked encrypted bitstream is constructed, the file size and format compliance are preserved. In this scheme, the server can extract additional messages from the marked encrypted bitstream using the embedding key. On the recipient side, the additional messages can also be extracted from the received bitstream if the embedding key is available. A recipient with only the encryption key can view an approximate image by a direct decryption. If both the encryption and embedding keys are available, the recipient can losslessly recover the original bitstream after decrypting the marked encrypted JPEG bitstream.
Separable Reversible Data Hiding in Encrypted JPEG Bitstreams, Reversible data hiding, information hiding, image recovery, JPEG encryption, JPEG Bitstreams
--
For More Details, Contact Us
****************************
Arihant Techno Solutions,
Mail us to Order this Project:
arihantsinfo@gmail.com
--
For a given JPEG bitstream and an encryption key, the content owner generates a ciphertext bitstream after syntax parsing and encryption. In the process, the file size is kept unchanged and the format is compliant to common JPEG decoders. When a remote server receives the encrypted bitstream, the data hider parses the bitstream and hides additional messages in it using an embedding key. After the marked encrypted bitstream is constructed, the file size and format compliance are preserved. In this scheme, the server can extract additional messages from the marked encrypted bitstream using the embedding key. On the recipient side, the additional messages can also be extracted from the received bitstream if the embedding key is available. A recipient with only the encryption key can view an approximate image by a direct decryption. If both the encryption and embedding keys are available, the recipient can losslessly recover the original bitstream after decrypting the marked encrypted JPEG bitstream.
Separable Reversible Data Hiding in Encrypted JPEG Bitstreams, Reversible data hiding, information hiding, image recovery, JPEG encryption, JPEG Bitstreams
--
For More Details, Contact Us
****************************
Arihant Techno Solutions,
Mail us to Order this Project:
arihantsinfo@gmail.com
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
89
Duration
4:11
Published
Sep 23, 2018
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now