RSA & Public Key Encryption: Learn the Rivest-Shamir-Adleman Algorithm 🔐
Discover how RSA works and explore key network protocols, layered models, and tools like traceroute and socket API in this comprehensive playlist!

Science Traveller
155 views • Jul 30, 2018
About this video
In this playlist you will learn about the following topics
Protocols, Layered Model Network components Uses of networks Traceroute and socket API Protocols and layering Reference models (Internet, OSI) History of the internet
Physical and Direct Link Layer Simple link models (latency, bandwidth-delay product) Media and signals Modulation schemes (baseband, passband) Fundamental limits (Shannon) Framing Error detection schemes (checksum, CRC) Error correction schemes (Hamming)
Retransmissions, Multiple access, Switching Retransmissions (ARQ) Multiplexing schemes (TDM. FDM) Random access / Ethernet (CSMA family) Wireless access / 802.11 Contention-free access / Token Ring LAN switching (switches vs. hubs, spanning tree, backward learning)
Network Layer and Internetworking Datagram and virtual circuit models (IP, MPLS) IP addressing and forwarding (prefixes, longest matching prefix) IP helpers: ARP, DHCP Internetworking (fragmentation, path MTU discovery, ICMP) IPv4 and IPv6 Network Address Translation (NAT)
Routing Shortest cost routing model Dijkstra's algorithm Flooding Distance Vector and Link-state Equal-cost multi-path routing Hierarchical routing (prefixes, aggregation, subnets) Multiple parties and policy (BGP)
Transport Layer, Reliable Transport Sockets, ports and service APIs Reliable and unreliable delivery (TCP, UDP) Connection establishment and teardown Flow control and sliding windows Retransmission timeouts
Congestion Control Fairness and Efficiency Additive Increase Multiplicative Decrease (AIMD) TCP congestion control (slow start, fast retransmission and recovery) Congestion avoidance (ECN)
Web and Content Distribution Naming (DNS) Web protocols (HTTP, caching) Content Distribution Networks (CDNs) Peer-to-Peer (BitTorrent)
Quality of Service and Real-Time Apps Streaming media and Conferencing Scheduling disciplines (FIFO, WFQ) Traffic shaping with Token Buckets Differentiated Services Rate and Delay Guarantees
Optional: Network Security Encryption for Confidentiality and Authenticity Web security (SSL, DNSSEC) Wireless security (802.11i) Firewalls and Virtual Private Networks (VPNs) Distributed Denial of Service (DDOS)
Computer Networks
1 OSI Model in Networking OSI model layers and their function (L1)
2 IP Address Basics: Classful Addressing dotted decimal notation
3 IP Address: Network ID and Host ID Network Mask
4 IP Address Subnet Supernet subnetmask
5 Classless IP Addressing: Subnet Mask, subnet block size, network address
6 Block Allocation of IP address Create subnets from block of IP address
7 Introduction to Interconnecting Devices: REPEATERS HUBS BRIDGE SWITCHES ROUTERS
8 VLAN: Virtual Lan concepts VLAN TRUNK and Switches
9 Address Resolution Protocol (ARP) and Reverse ARP explained Animated
10 Medium Access Control: Aloha and Slotted Aloha Protocol
11 Carrier Sense Multiple Access Protocol CSMA
12 CSMA/CD (Carrier Sense Multiple Access/ Collision Detection)
13 Network Address Translation (NAT)
14 Dynamic Host Configuration Protocol (DHCP)
15 Circuit Switching vs Packet Switching
16 Virtual Circuit Network Virtual Circuit switching
17 Domain Name Server (DNS) Name Server DNS how dns works
18 Internet Control Message Protocol (ICMP) ICMP protocol tutorial part 1
19 Internet Control Message Protocol (ICMP) : Error Message (Part 2)
20 Stop and Wait Protocol Stop and Wair ARQ Stop and Wait Flow control
21 GO BACK N ARQ Protocol Go back N sliding window
22 SELECTIVE REPEAT ARQ selective repeat sliding window protocol
23 Authentication Protocol Man In Middle Attack Replay Attack Nonce
24 Introduction to Public Key Cryptography Public Key Cryptography animation
25 Introduction to Digital Signature Public Key cryptography
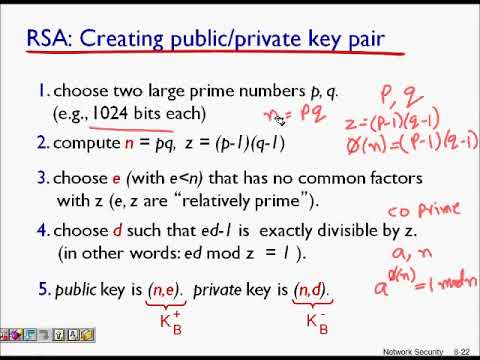
26 RSA Algorithm and public key encryption rivest shamir adleman algorithm
27 Message Digest and Digital Signature Cryptographic Hash Function
28 Certification Authority (CA) Digital Certificate
29 Secure EMail How To Public Private Key Encryption Secure E-Mail PGP
Protocols, Layered Model Network components Uses of networks Traceroute and socket API Protocols and layering Reference models (Internet, OSI) History of the internet
Physical and Direct Link Layer Simple link models (latency, bandwidth-delay product) Media and signals Modulation schemes (baseband, passband) Fundamental limits (Shannon) Framing Error detection schemes (checksum, CRC) Error correction schemes (Hamming)
Retransmissions, Multiple access, Switching Retransmissions (ARQ) Multiplexing schemes (TDM. FDM) Random access / Ethernet (CSMA family) Wireless access / 802.11 Contention-free access / Token Ring LAN switching (switches vs. hubs, spanning tree, backward learning)
Network Layer and Internetworking Datagram and virtual circuit models (IP, MPLS) IP addressing and forwarding (prefixes, longest matching prefix) IP helpers: ARP, DHCP Internetworking (fragmentation, path MTU discovery, ICMP) IPv4 and IPv6 Network Address Translation (NAT)
Routing Shortest cost routing model Dijkstra's algorithm Flooding Distance Vector and Link-state Equal-cost multi-path routing Hierarchical routing (prefixes, aggregation, subnets) Multiple parties and policy (BGP)
Transport Layer, Reliable Transport Sockets, ports and service APIs Reliable and unreliable delivery (TCP, UDP) Connection establishment and teardown Flow control and sliding windows Retransmission timeouts
Congestion Control Fairness and Efficiency Additive Increase Multiplicative Decrease (AIMD) TCP congestion control (slow start, fast retransmission and recovery) Congestion avoidance (ECN)
Web and Content Distribution Naming (DNS) Web protocols (HTTP, caching) Content Distribution Networks (CDNs) Peer-to-Peer (BitTorrent)
Quality of Service and Real-Time Apps Streaming media and Conferencing Scheduling disciplines (FIFO, WFQ) Traffic shaping with Token Buckets Differentiated Services Rate and Delay Guarantees
Optional: Network Security Encryption for Confidentiality and Authenticity Web security (SSL, DNSSEC) Wireless security (802.11i) Firewalls and Virtual Private Networks (VPNs) Distributed Denial of Service (DDOS)
Computer Networks
1 OSI Model in Networking OSI model layers and their function (L1)
2 IP Address Basics: Classful Addressing dotted decimal notation
3 IP Address: Network ID and Host ID Network Mask
4 IP Address Subnet Supernet subnetmask
5 Classless IP Addressing: Subnet Mask, subnet block size, network address
6 Block Allocation of IP address Create subnets from block of IP address
7 Introduction to Interconnecting Devices: REPEATERS HUBS BRIDGE SWITCHES ROUTERS
8 VLAN: Virtual Lan concepts VLAN TRUNK and Switches
9 Address Resolution Protocol (ARP) and Reverse ARP explained Animated
10 Medium Access Control: Aloha and Slotted Aloha Protocol
11 Carrier Sense Multiple Access Protocol CSMA
12 CSMA/CD (Carrier Sense Multiple Access/ Collision Detection)
13 Network Address Translation (NAT)
14 Dynamic Host Configuration Protocol (DHCP)
15 Circuit Switching vs Packet Switching
16 Virtual Circuit Network Virtual Circuit switching
17 Domain Name Server (DNS) Name Server DNS how dns works
18 Internet Control Message Protocol (ICMP) ICMP protocol tutorial part 1
19 Internet Control Message Protocol (ICMP) : Error Message (Part 2)
20 Stop and Wait Protocol Stop and Wair ARQ Stop and Wait Flow control
21 GO BACK N ARQ Protocol Go back N sliding window
22 SELECTIVE REPEAT ARQ selective repeat sliding window protocol
23 Authentication Protocol Man In Middle Attack Replay Attack Nonce
24 Introduction to Public Key Cryptography Public Key Cryptography animation
25 Introduction to Digital Signature Public Key cryptography
26 RSA Algorithm and public key encryption rivest shamir adleman algorithm
27 Message Digest and Digital Signature Cryptographic Hash Function
28 Certification Authority (CA) Digital Certificate
29 Secure EMail How To Public Private Key Encryption Secure E-Mail PGP
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
155
Likes
1
Duration
11:57
Published
Jul 30, 2018
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.