Privacy-Enhancing Computation: Protect Data in Use 🔐
Discover PEC techniques that enable data to be processed securely without compromising privacy, boosting data security and privacy.

CodeVisium
253 views • May 26, 2025
About this video
Privacy-Enhancing Computation (PEC) refers to a set of cryptographic and system-level techniques that allow data to be processed and analyzed while it remains encrypted or otherwise protected—preventing exposure of sensitive information even during computation. As regulatory and competitive demands for data collaboration rise, PEC offers a path to derive insights without sacrificing confidentiality.
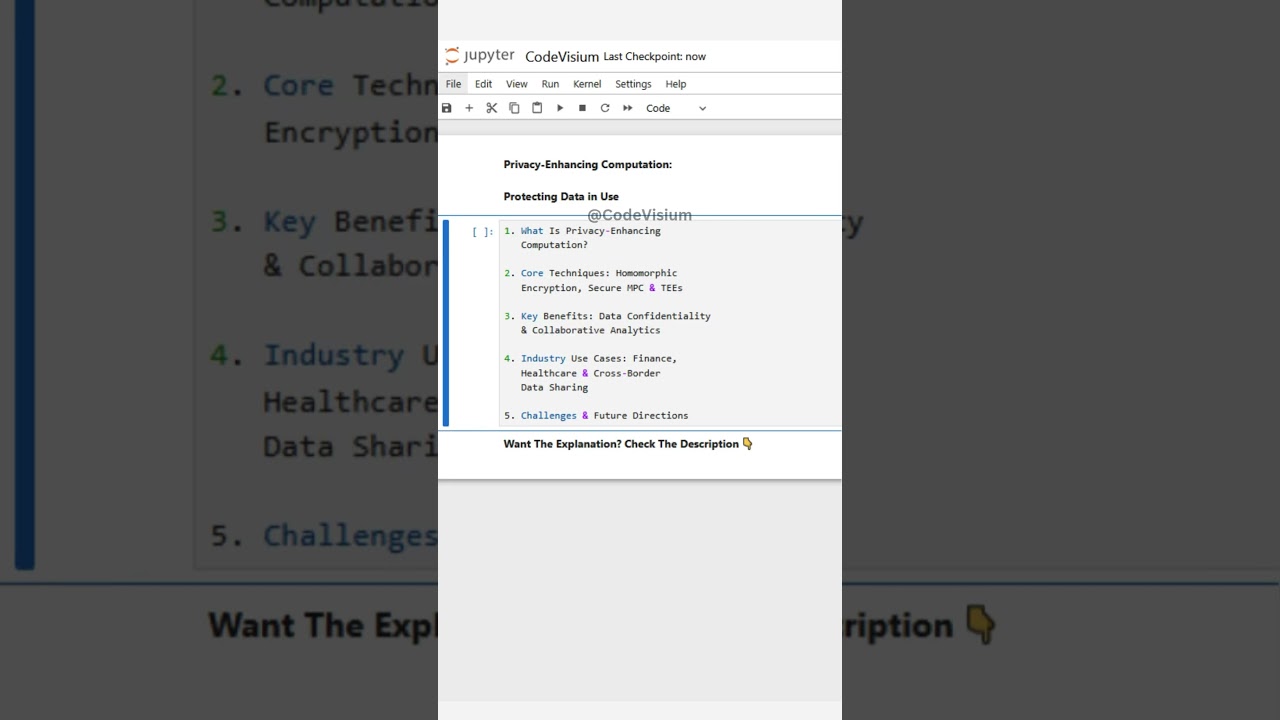
What Is Privacy-Enhancing Computation?
PEC encompasses methods that enable secure data use: instead of decrypting data before analysis, computations occur on protected representations. This ensures that proprietary, personal, or regulated data never appears in clear text outside the data owner’s control.
Core Techniques: Homomorphic Encryption, Secure MPC & TEEs:
Homomorphic Encryption (HE): Allows arithmetic operations directly on ciphertexts, producing encrypted results that decrypt to the correct answer, albeit with performance overhead.
Secure Multi-Party Computation (MPC): Distributes computation among multiple parties, each holding a secret share; together they compute a function without revealing their private inputs.
Trusted Execution Environments (TEEs): Hardware-based enclaves (e.g., Intel SGX, ARM TrustZone) isolate code and data in a secure enclave, protecting it even if the host OS is compromised.
Key Benefits: Data Confidentiality & Collaborative Analytics:
By keeping data encrypted or within secured hardware, PEC ensures absolute confidentiality during processing. Organizations can collaborate—sharing only encrypted datasets—enabling joint analytics, machine learning, and federated data science without exposing underlying records.
Industry Use Cases: Finance, Healthcare & Cross-Border Data Sharing:
Finance: Banks use HE to run fraud detection models on customer transaction data held across multiple institutions without sharing raw records.
Healthcare: Hospitals collaborate on outcomes research by performing MPC over patient data to improve treatment protocols while maintaining HIPAA compliance.
Cross-Border Analytics: Companies employ TEEs in cloud environments to analyze international data across regulatory domains, ensuring GDPR and other privacy law adherence.
Challenges & Future Directions:
Performance and scalability remain the primary hurdles—HE operations can be orders of magnitude slower than plaintext, and MPC protocols incur communication overhead. Emerging compiler toolchains and hardware accelerators (e.g., FPGA implementations of HE) promise to narrow this gap. Standardization efforts are underway to integrate PEC into mainstream analytics and AI pipelines, paving the way for privacy-first data ecosystems.
By mastering Privacy-Enhancing Computation, you’ll be able to architect systems that unlock new collaborative opportunities while upholding the highest data-protection standards. Don’t forget to like, share, and subscribe for more deep-dive tutorials on today’s most trending tech topics throughout your B.Tech journey!
What Is Privacy-Enhancing Computation?
PEC encompasses methods that enable secure data use: instead of decrypting data before analysis, computations occur on protected representations. This ensures that proprietary, personal, or regulated data never appears in clear text outside the data owner’s control.
Core Techniques: Homomorphic Encryption, Secure MPC & TEEs:
Homomorphic Encryption (HE): Allows arithmetic operations directly on ciphertexts, producing encrypted results that decrypt to the correct answer, albeit with performance overhead.
Secure Multi-Party Computation (MPC): Distributes computation among multiple parties, each holding a secret share; together they compute a function without revealing their private inputs.
Trusted Execution Environments (TEEs): Hardware-based enclaves (e.g., Intel SGX, ARM TrustZone) isolate code and data in a secure enclave, protecting it even if the host OS is compromised.
Key Benefits: Data Confidentiality & Collaborative Analytics:
By keeping data encrypted or within secured hardware, PEC ensures absolute confidentiality during processing. Organizations can collaborate—sharing only encrypted datasets—enabling joint analytics, machine learning, and federated data science without exposing underlying records.
Industry Use Cases: Finance, Healthcare & Cross-Border Data Sharing:
Finance: Banks use HE to run fraud detection models on customer transaction data held across multiple institutions without sharing raw records.
Healthcare: Hospitals collaborate on outcomes research by performing MPC over patient data to improve treatment protocols while maintaining HIPAA compliance.
Cross-Border Analytics: Companies employ TEEs in cloud environments to analyze international data across regulatory domains, ensuring GDPR and other privacy law adherence.
Challenges & Future Directions:
Performance and scalability remain the primary hurdles—HE operations can be orders of magnitude slower than plaintext, and MPC protocols incur communication overhead. Emerging compiler toolchains and hardware accelerators (e.g., FPGA implementations of HE) promise to narrow this gap. Standardization efforts are underway to integrate PEC into mainstream analytics and AI pipelines, paving the way for privacy-first data ecosystems.
By mastering Privacy-Enhancing Computation, you’ll be able to architect systems that unlock new collaborative opportunities while upholding the highest data-protection standards. Don’t forget to like, share, and subscribe for more deep-dive tutorials on today’s most trending tech topics throughout your B.Tech journey!
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
253
Duration
0:10
Published
May 26, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.