Poison Pixels: How Cybercriminals Use Image Steganography & How to Fight Back 🛡️
Discover how cybercriminals leverage steganography to hide malicious content in images, and learn effective strategies to detect and combat this growing threat in cybersecurity.

RSA Conference
951 views • May 31, 2018
About this video
Simon Wiseman, CTO, Deep Secure
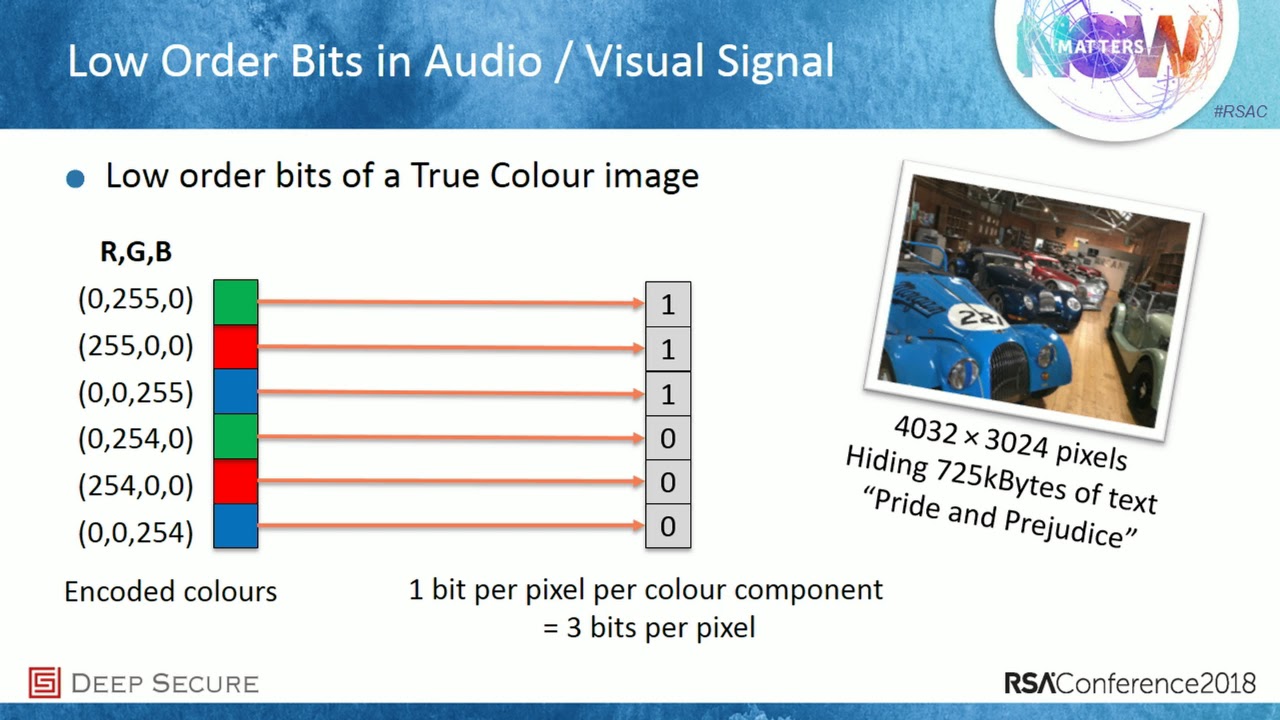
Image steganography is becoming the attack vector of choice for cyber criminals. This session explains what Stegware is, how it is being used (anti-virus evasion, covert command & control channels, data exfiltration), how it works (redundant data, LSB injection, ordering), why detection strategies will continue to fail to tackle the problem and how transformation can annihilate it.
Learning Objectives:
1: Learn why steganography is now the attack vector of choice for cybercriminals.
2: Understand precisely how it renders detection-based cybersecurity ineffective.
3: Discover a ground-breaking approach to destroying the steganography threat.
https://www.rsaconference.com/events/us18/agenda/sessions/9490-poison-pixels-combatting-image-steganography-in
Image steganography is becoming the attack vector of choice for cyber criminals. This session explains what Stegware is, how it is being used (anti-virus evasion, covert command & control channels, data exfiltration), how it works (redundant data, LSB injection, ordering), why detection strategies will continue to fail to tackle the problem and how transformation can annihilate it.
Learning Objectives:
1: Learn why steganography is now the attack vector of choice for cybercriminals.
2: Understand precisely how it renders detection-based cybersecurity ineffective.
3: Discover a ground-breaking approach to destroying the steganography threat.
https://www.rsaconference.com/events/us18/agenda/sessions/9490-poison-pixels-combatting-image-steganography-in
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
951
Likes
7
Duration
40:57
Published
May 31, 2018
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.