Pass-the-Hash Attack in Cybersecurity 🔑
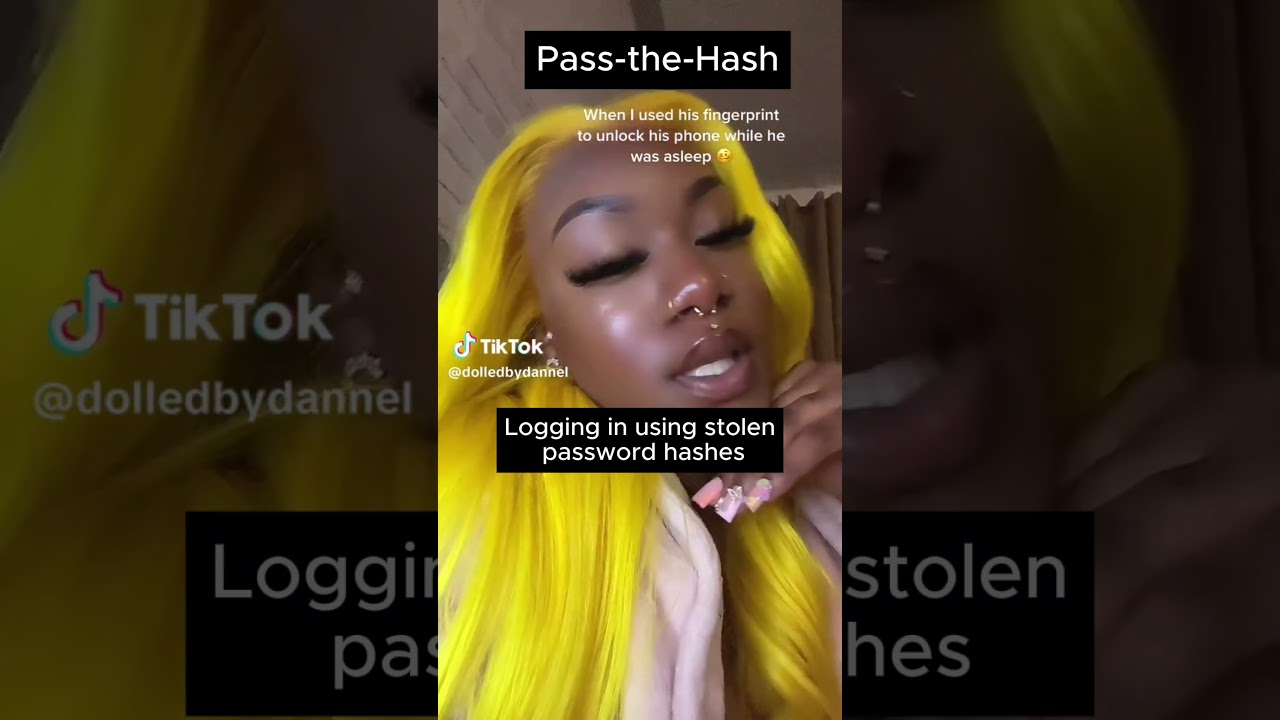
Learn about Pass-the-Hash attacks, cryptanalysis, and secure design, akin to unlocking a phone with a fingerprint while asleep.

Quick Cybersecurity Study
52 views • Mar 12, 2025
About this video
📱 **Pass-the-Hash Attack in Cryptanalysis & Secure by Design = Using Your BF’s Fingerprint to Unlock His Phone While He’s Asleep!** 🔐✨
Just like bypassing a password by using stored biometrics, **Pass-the-Hash Attacks** steal and reuse hashed passwords to gain unauthorized access **without needing the actual password**. 💻⚠️
With **Secure by Design**, multi-factor authentication (MFA) and credential encryption help prevent these attacks! ✅🔐
#CyberSecurity #PassTheHash #Cryptanalysis #CyberAttack #SecureByDesign #CyberDefense #DataProtection #InfoSec #TechEducation #CyberSecTraining #VisualLearning #CyberSecurityCertification #ITKnowledge #TechForBeginners #LearnCyberSecurity #SecurityAwareness #CyberSecCommunity
Just like bypassing a password by using stored biometrics, **Pass-the-Hash Attacks** steal and reuse hashed passwords to gain unauthorized access **without needing the actual password**. 💻⚠️
With **Secure by Design**, multi-factor authentication (MFA) and credential encryption help prevent these attacks! ✅🔐
#CyberSecurity #PassTheHash #Cryptanalysis #CyberAttack #SecureByDesign #CyberDefense #DataProtection #InfoSec #TechEducation #CyberSecTraining #VisualLearning #CyberSecurityCertification #ITKnowledge #TechForBeginners #LearnCyberSecurity #SecurityAwareness #CyberSecCommunity
Video Information
Views
52
Duration
0:10
Published
Mar 12, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.