OWASP Top 10 - 2021 Walkthrough on TryHackMe 🔐
Explore the OWASP Top 10 - 2021 vulnerabilities with this hands-on TryHackMe guide on web security threats.

Djalil Ayed
66.0K views • Mar 8, 2023
About this video
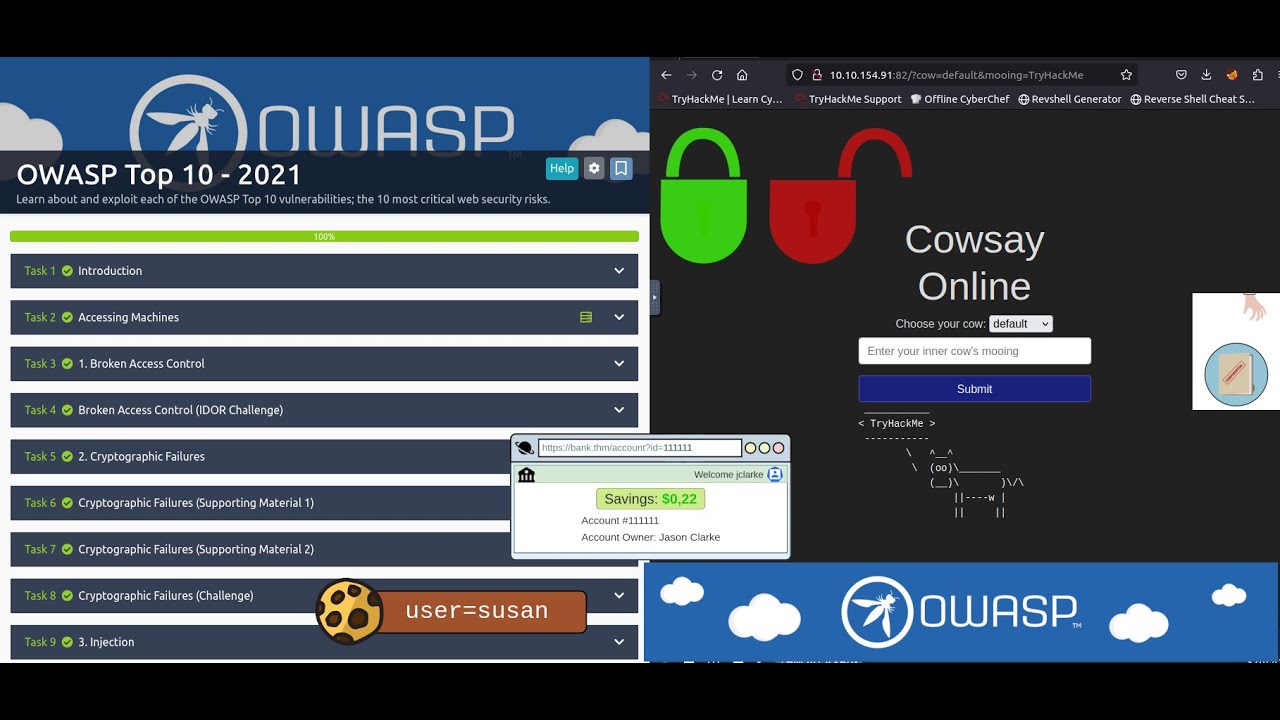
🔥🔥 Dive deep into the OWASP Top 10 - 2021 vulnerabilities with this comprehensive walkthrough of the TryHackMe room! In this video, we'll explore each of the 10 most critical web security risks, showing you how they occur and, more importantly, how to exploit them. Perfect for beginners and those looking to solidify their web security skills.
This walkthrough covers:
🚀 Broken Access Control:** (Timestamp: [0:43]) Learn how to bypass authorization checks and gain unauthorized access (IDOR Challenge).
🚀 Cryptographic Failures:** (Timestamp: [2:53]) Understand weak encryption and how to exploit data breaches.
🚀 Injection:** (Timestamp: [07:49]) SQL Injection, command injection.
🚀 Insecure Design:** (Timestamp: [12:08]) Discover how flawed architectural designs lead to vulnerabilities.
🚀 Security Misconfiguration:** (Timestamp: [14:23]) Identify and exploit common misconfigurations in web servers and applications.
🚀 Vulnerable and Outdated Components:** (Timestamp: [16:02]) Learn how to exploit known vulnerabilities in outdated software.
🚀 Identification and Authentication Failures:** (Timestamp: [21:39]) Explore weak authentication mechanisms and bypass login systems.
🚀 Software and Data Integrity Failures:** (Timestamp: [23:51]) Understand how to manipulate data and code to achieve unauthorized actions.
🚀 Security Logging & Monitoring Failures:** (Timestamp: [28:58]) Learn how to evade detection and exploit insufficient logging.
🚀 Server-Side Request Forgery (SSRF):** (Timestamp: [29:48]) Discover how to exploit SSRF vulnerabilities to access internal resources.
🔥🔥 This room is designed for beginners, so no prior security knowledge is required. We'll break down each vulnerability into easy-to-understand concepts and demonstrate practical exploitation techniques.
🔥 Room Link: https://tryhackme.com/room/owasptop102021
🟢 FOR ADMIN AREA FLAG:🟢 https://youtu.be/Yc4jzWb_h4Q
🔥 What you'll learn: ✨✨✨✨
✨ Practical exploitation of all OWASP Top 10 - 2021 vulnerabilities.
✨ How these vulnerabilities occur in real-world applications.
✨ Step-by-step walkthroughs of each challenge in the TryHackMe room.
✨ Essential web security skills for beginners.
👍 If you found this video helpful, please like, comment, and subscribe for more cybersecurity walkthroughs!
#OWASP #OWASPTop10 #WebSecurity #Cybersecurity #EthicalHacking #TryHackMe #Vulnerability #Injection #SSRF #BrokenAccessControl #SecurityMisconfiguration #Beginner #Tutorial #CTF #cryptographicfailures #insecuredesign #brokenaccesscontrol #injection #securitymisconfiguration #vulnerablecomponents #identificationfailures #softwareintegrity #securitylogging #serversideforegery
👍 Like, Subscribe, and Comment to stay updated with our latest cybersecurity tutorials. If you have any questions or need further clarification on any concept, feel free to drop a comment below!
👍 these tutorials are for educational purposes and to encourage responsible and legal use of hacking knowledge.
This walkthrough covers:
🚀 Broken Access Control:** (Timestamp: [0:43]) Learn how to bypass authorization checks and gain unauthorized access (IDOR Challenge).
🚀 Cryptographic Failures:** (Timestamp: [2:53]) Understand weak encryption and how to exploit data breaches.
🚀 Injection:** (Timestamp: [07:49]) SQL Injection, command injection.
🚀 Insecure Design:** (Timestamp: [12:08]) Discover how flawed architectural designs lead to vulnerabilities.
🚀 Security Misconfiguration:** (Timestamp: [14:23]) Identify and exploit common misconfigurations in web servers and applications.
🚀 Vulnerable and Outdated Components:** (Timestamp: [16:02]) Learn how to exploit known vulnerabilities in outdated software.
🚀 Identification and Authentication Failures:** (Timestamp: [21:39]) Explore weak authentication mechanisms and bypass login systems.
🚀 Software and Data Integrity Failures:** (Timestamp: [23:51]) Understand how to manipulate data and code to achieve unauthorized actions.
🚀 Security Logging & Monitoring Failures:** (Timestamp: [28:58]) Learn how to evade detection and exploit insufficient logging.
🚀 Server-Side Request Forgery (SSRF):** (Timestamp: [29:48]) Discover how to exploit SSRF vulnerabilities to access internal resources.
🔥🔥 This room is designed for beginners, so no prior security knowledge is required. We'll break down each vulnerability into easy-to-understand concepts and demonstrate practical exploitation techniques.
🔥 Room Link: https://tryhackme.com/room/owasptop102021
🟢 FOR ADMIN AREA FLAG:🟢 https://youtu.be/Yc4jzWb_h4Q
🔥 What you'll learn: ✨✨✨✨
✨ Practical exploitation of all OWASP Top 10 - 2021 vulnerabilities.
✨ How these vulnerabilities occur in real-world applications.
✨ Step-by-step walkthroughs of each challenge in the TryHackMe room.
✨ Essential web security skills for beginners.
👍 If you found this video helpful, please like, comment, and subscribe for more cybersecurity walkthroughs!
#OWASP #OWASPTop10 #WebSecurity #Cybersecurity #EthicalHacking #TryHackMe #Vulnerability #Injection #SSRF #BrokenAccessControl #SecurityMisconfiguration #Beginner #Tutorial #CTF #cryptographicfailures #insecuredesign #brokenaccesscontrol #injection #securitymisconfiguration #vulnerablecomponents #identificationfailures #softwareintegrity #securitylogging #serversideforegery
👍 Like, Subscribe, and Comment to stay updated with our latest cybersecurity tutorials. If you have any questions or need further clarification on any concept, feel free to drop a comment below!
👍 these tutorials are for educational purposes and to encourage responsible and legal use of hacking knowledge.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
66.0K
Likes
623
Duration
33:36
Published
Mar 8, 2023
User Reviews
4.4
(13) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now