Overview of Cryptographic Techniques
This overview presents various cryptographic techniques, offering insights into their applications and significance in the field of cybersecurity. Join Hector as he explores the fundamental concepts and practices that underpin modern cryptography.

Magalyn Melgarejo
244 views • Nov 5, 2017
About this video
Subscribe today and give the gift of knowledge to yourself or a friend
overview of cryptographic techniques
Overview of Cryptographic Techniques . Hector M Lugo-Cordero CIS 4361 Secure Operating System Administration. 1. Resources Used. Lecture slides from Dr Ratan Guha CNT 6519 Wireless Security Forensics Cryptography and Network Security, Fourth Edition, by William Stallings Slideshow 2971598 by garry
show1 : overview of cryptographic techniques
show2 : overview of cryptographic techniques
show3 : resources used
show4 : resources used
show5 : outline
show6 : outline
show7 : some basic terminology
show8 : some basic terminology
show9 : conventional encryption principles
show10 : conventional encryption principles
show11 : characteristics of cryptographic techniques
show12 : characteristics of cryptographic techniques
show13 : symmetric encryption
show14 : symmetric encryption
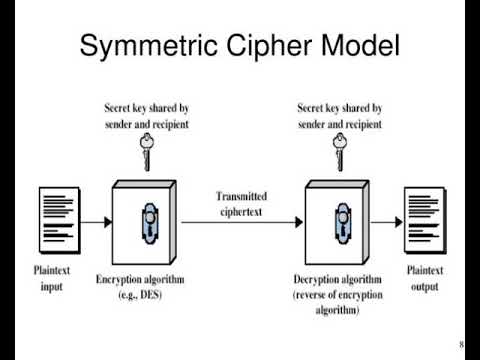
show15 : symmetric cipher model
show16 : symmetric cipher model
show17 : requirements
show18 : requirements
show19 : brute force search
show20 : brute force search
show21 : classical substitution ciphers
show22 : classical substitution ciphers
show23 : caesar cipher
show24 : caesar cipher
show25 : caesar cipher1
show26 : caesar cipher1
show27 : monoalphabetic cipher
show28 : monoalphabetic cipher
show29 : playfair cipher
show30 : playfair cipher
show31 : playfair key matrix
overview of cryptographic techniques
Overview of Cryptographic Techniques . Hector M Lugo-Cordero CIS 4361 Secure Operating System Administration. 1. Resources Used. Lecture slides from Dr Ratan Guha CNT 6519 Wireless Security Forensics Cryptography and Network Security, Fourth Edition, by William Stallings Slideshow 2971598 by garry
show1 : overview of cryptographic techniques
show2 : overview of cryptographic techniques
show3 : resources used
show4 : resources used
show5 : outline
show6 : outline
show7 : some basic terminology
show8 : some basic terminology
show9 : conventional encryption principles
show10 : conventional encryption principles
show11 : characteristics of cryptographic techniques
show12 : characteristics of cryptographic techniques
show13 : symmetric encryption
show14 : symmetric encryption
show15 : symmetric cipher model
show16 : symmetric cipher model
show17 : requirements
show18 : requirements
show19 : brute force search
show20 : brute force search
show21 : classical substitution ciphers
show22 : classical substitution ciphers
show23 : caesar cipher
show24 : caesar cipher
show25 : caesar cipher1
show26 : caesar cipher1
show27 : monoalphabetic cipher
show28 : monoalphabetic cipher
show29 : playfair cipher
show30 : playfair cipher
show31 : playfair key matrix
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
244
Likes
1
Duration
5:01
Published
Nov 5, 2017
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.