Non-Repudiation & Encryption Made Simple 🔐 | Cybersecurity & Cryptography for Beginners
Learn the essentials of non-repudiation and encryption in cybersecurity. This beginner-friendly video covers key cryptographic concepts like hashing to help you understand how data security works.

Fortray Global Services Limited
136 views • Dec 27, 2021
About this video
Non-Repudiation & Encryption Explained | Cybersecurity & Cryptography Basics for Beginners
This video explains key cryptographic concepts, including hashing, encryption, authentication, and non-repudiation. It compares symmetric and asymmetric encryption, highlights their strengths and weaknesses, and discusses the performance limitations and security trade-offs involved in cryptographic processes.
Video Chapters
0:00 - 0:31 – Cryptographic use cases and the importance of authentication and non-repudiation.
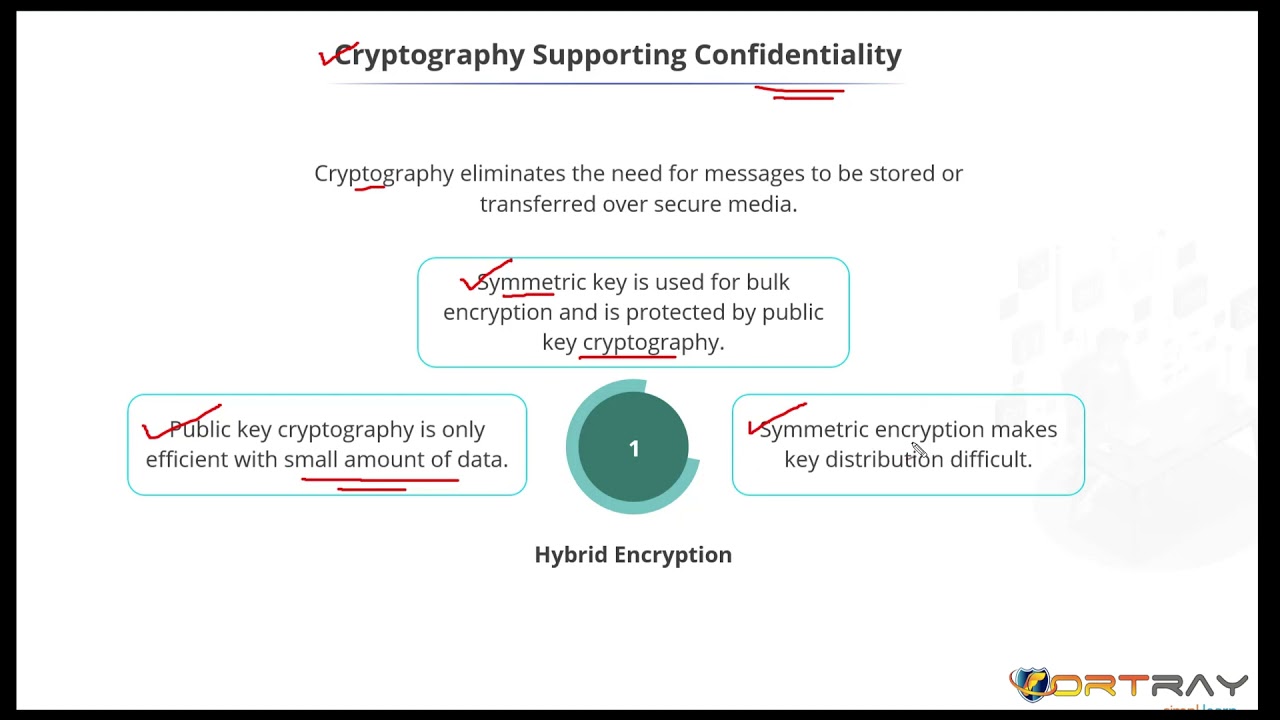
1:32 - 2:59 - Parameters of Cryptography: Confidentiality
3:00 - 4:51 - Cryptographic Performance Limitations
4:52 - 5:44 - Key Takeaways
5:48 - 7:00 - Quiz
To learn more about Fortray
Website: https://wwww.fortray.com/
Fortray Blogs
https://www.fortray.com/blog/
Learn More About Our Cybersecurity Engineer Traineeship Program
https://www.fortray.com/itcareerswitch/cybersecurity-job-placement-after-training-certification-course-online/
Learn More About Our Network Security Engineer Job Guarantee Program
https://career.fortray.com/network-cyber-security-engineer-job-guarantee-master-online-course-certification-training-Program/
👉FOLLOW US ON SOCIAL MEDIA:
✔ Pinterest: https://uk.pinterest.com/Fortraydigital/
✔ Instagram: https://www.instagram.com/fortrayglobalservices/
✔ Facebook: https://www.facebook.com/fortraynet
✔ YouTube: https://www.youtube.com/@fortrayglobalservices/
📢 Subscribe to Fortray Global Services for expert-led IT & Business Analysis training!
👍 Like, Comment & Share if you found this helpful!
This video explains key cryptographic concepts, including hashing, encryption, authentication, and non-repudiation. It compares symmetric and asymmetric encryption, highlights their strengths and weaknesses, and discusses the performance limitations and security trade-offs involved in cryptographic processes.
Video Chapters
0:00 - 0:31 – Cryptographic use cases and the importance of authentication and non-repudiation.
1:32 - 2:59 - Parameters of Cryptography: Confidentiality
3:00 - 4:51 - Cryptographic Performance Limitations
4:52 - 5:44 - Key Takeaways
5:48 - 7:00 - Quiz
To learn more about Fortray
Website: https://wwww.fortray.com/
Fortray Blogs
https://www.fortray.com/blog/
Learn More About Our Cybersecurity Engineer Traineeship Program
https://www.fortray.com/itcareerswitch/cybersecurity-job-placement-after-training-certification-course-online/
Learn More About Our Network Security Engineer Job Guarantee Program
https://career.fortray.com/network-cyber-security-engineer-job-guarantee-master-online-course-certification-training-Program/
👉FOLLOW US ON SOCIAL MEDIA:
✔ Pinterest: https://uk.pinterest.com/Fortraydigital/
✔ Instagram: https://www.instagram.com/fortrayglobalservices/
✔ Facebook: https://www.facebook.com/fortraynet
✔ YouTube: https://www.youtube.com/@fortrayglobalservices/
📢 Subscribe to Fortray Global Services for expert-led IT & Business Analysis training!
👍 Like, Comment & Share if you found this helpful!
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
136
Likes
2
Duration
7:01
Published
Dec 27, 2021
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now