No Hat 2025: NTLM Reflection's Rise & Fall 🔐
Explores the history and demise of NTLM reflection, highlighting a Windows RCE incident and its impact over two decades.

BITM Hacklab
159 views • Oct 27, 2025
About this video
NTLM reflection is dead, long live NTLM reflection: Story of an accidental Windows RCE
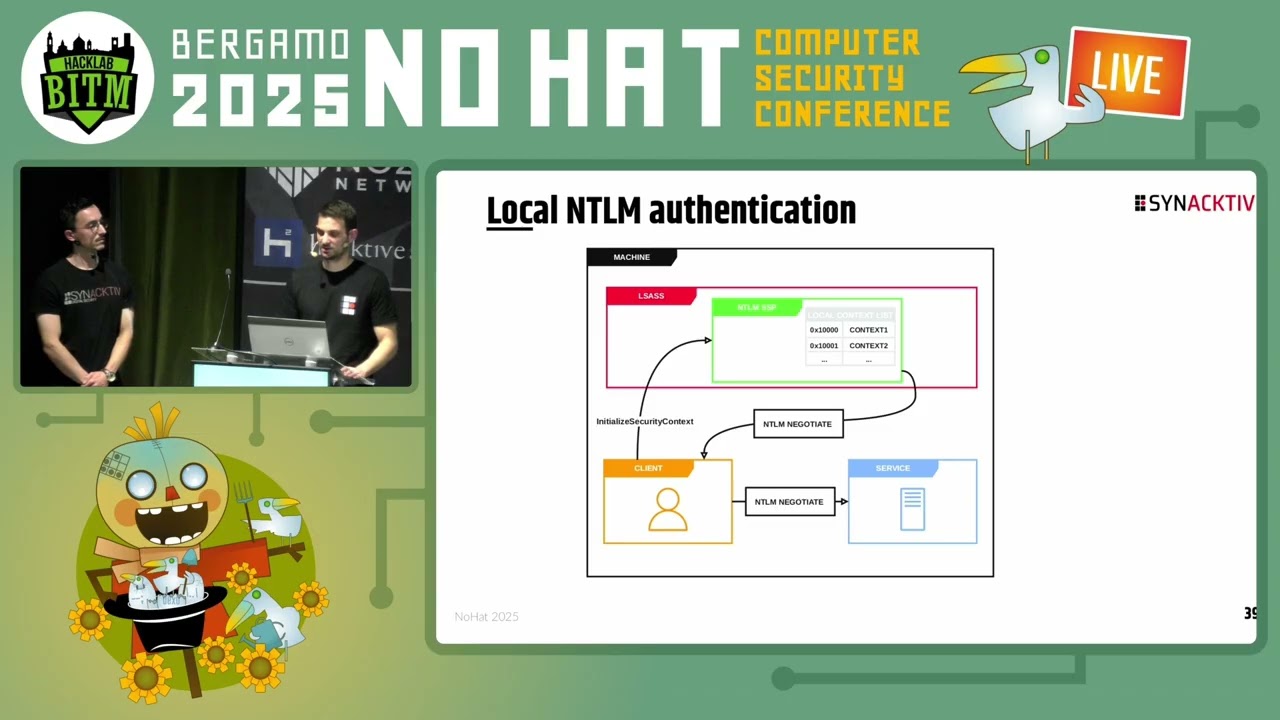
For nearly two decades, Windows has been plagued with NTLM reflection vulnerabilities. This special case of NTLM authentication relay has historically led to local privilege escalation or even remote command execution, although with some limitations. Over time, mitigations against this class of vulnerability were implemented, leading to a false assumption that NTLM reflection attacks were relics of the past. This presentation will shatter that assumption by covering the research that led to the discovery of CVE-2025-33073, a logical vulnerability leading to authenticated RCE as SYSTEM on almost any Windows machine. In this talk, fundamental concepts about authentication relay attacks will be explained, as well as the context surrounding the research. Afterwards, a methodical investigation of the root cause of the vulnerability will be presented, first by analysing network captures and then by performing a thorough reverse-engineering of LSASS internals. Subsequently, we will shift our attention to Kerberos, where we will demonstrate that CVE-2025-33073 is not restricted to NTLM and also affects Kerberos. After a brief reminder of the protocol, in-depth insights in its integration within LSASS will be discussed as well as an undocumented behavior, to understand why this vulnerability also applies to Kerberos. Finally, the patch analysis will be presented. We will detail how it fixes the attack vector described in this presentation and how it may not be enough to eradicate this class of vulnerability. We will conclude by explaining how the exploitation of this vulnerability could have been prevented even before it was found.
Guillaume André - Security Researcher @Synacktiv
Guillaume is a penetration tester and security researcher working at Synacktiv. During his career, he developed a healthy addiction to Windows systems and their internals. He is also passionate about Active Directory security, in which he gathered solid knowledge through several Red Team engagements and internal pentests.
Wilfried Bécard - Researcher @Synacktiv
Wilfried Bécard is a hacker and researcher working at Synacktiv. With a particular interest in Active Directory and Azure exploitation, his passion lies in uncovering new techniques to enhance cybersecurity in these areas. Constantly experimenting, testing, and collaborating with the security community, he aims at improving his knowledge in these fields.
LINKS
No Hat - Website: nohat.it
No Hat - X: @nohatcon
No Hat - BlueSky: https://bsky.app/profile/nohatcon.bsky.social
G. André - LinkedIn: https://linkedin.com/in/guiandre/
G. André - X: @yaumn_
W. Bécard - LinkedIn: https://linkedin.com/in/wilfried-bécard-7392a9151/
W. Bécard - X: @wil_fri3d
For nearly two decades, Windows has been plagued with NTLM reflection vulnerabilities. This special case of NTLM authentication relay has historically led to local privilege escalation or even remote command execution, although with some limitations. Over time, mitigations against this class of vulnerability were implemented, leading to a false assumption that NTLM reflection attacks were relics of the past. This presentation will shatter that assumption by covering the research that led to the discovery of CVE-2025-33073, a logical vulnerability leading to authenticated RCE as SYSTEM on almost any Windows machine. In this talk, fundamental concepts about authentication relay attacks will be explained, as well as the context surrounding the research. Afterwards, a methodical investigation of the root cause of the vulnerability will be presented, first by analysing network captures and then by performing a thorough reverse-engineering of LSASS internals. Subsequently, we will shift our attention to Kerberos, where we will demonstrate that CVE-2025-33073 is not restricted to NTLM and also affects Kerberos. After a brief reminder of the protocol, in-depth insights in its integration within LSASS will be discussed as well as an undocumented behavior, to understand why this vulnerability also applies to Kerberos. Finally, the patch analysis will be presented. We will detail how it fixes the attack vector described in this presentation and how it may not be enough to eradicate this class of vulnerability. We will conclude by explaining how the exploitation of this vulnerability could have been prevented even before it was found.
Guillaume André - Security Researcher @Synacktiv
Guillaume is a penetration tester and security researcher working at Synacktiv. During his career, he developed a healthy addiction to Windows systems and their internals. He is also passionate about Active Directory security, in which he gathered solid knowledge through several Red Team engagements and internal pentests.
Wilfried Bécard - Researcher @Synacktiv
Wilfried Bécard is a hacker and researcher working at Synacktiv. With a particular interest in Active Directory and Azure exploitation, his passion lies in uncovering new techniques to enhance cybersecurity in these areas. Constantly experimenting, testing, and collaborating with the security community, he aims at improving his knowledge in these fields.
LINKS
No Hat - Website: nohat.it
No Hat - X: @nohatcon
No Hat - BlueSky: https://bsky.app/profile/nohatcon.bsky.social
G. André - LinkedIn: https://linkedin.com/in/guiandre/
G. André - X: @yaumn_
W. Bécard - LinkedIn: https://linkedin.com/in/wilfried-bécard-7392a9151/
W. Bécard - X: @wil_fri3d
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
159
Likes
8
Duration
38:42
Published
Oct 27, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now