Network Information Hiding, Chapter 7b: Countermeasures for Sophisticated Hiding Techniques
An online class session by Prof. Dr. Steffen Wendzel covering advanced countermeasures against sophisticated network information hiding techniques, including slides, exercises, and reading assignments.

Steffen Wendzel
546 views • May 22, 2020
About this video
This is a video of a whole online class on network information hiding by Prof. Dr. Steffen Wendzel.
Slides, exercises and reading assignments:
https://github.com/cdpxe/Network-Covert-Channels-A-University-level-Course/blob/master/README.md
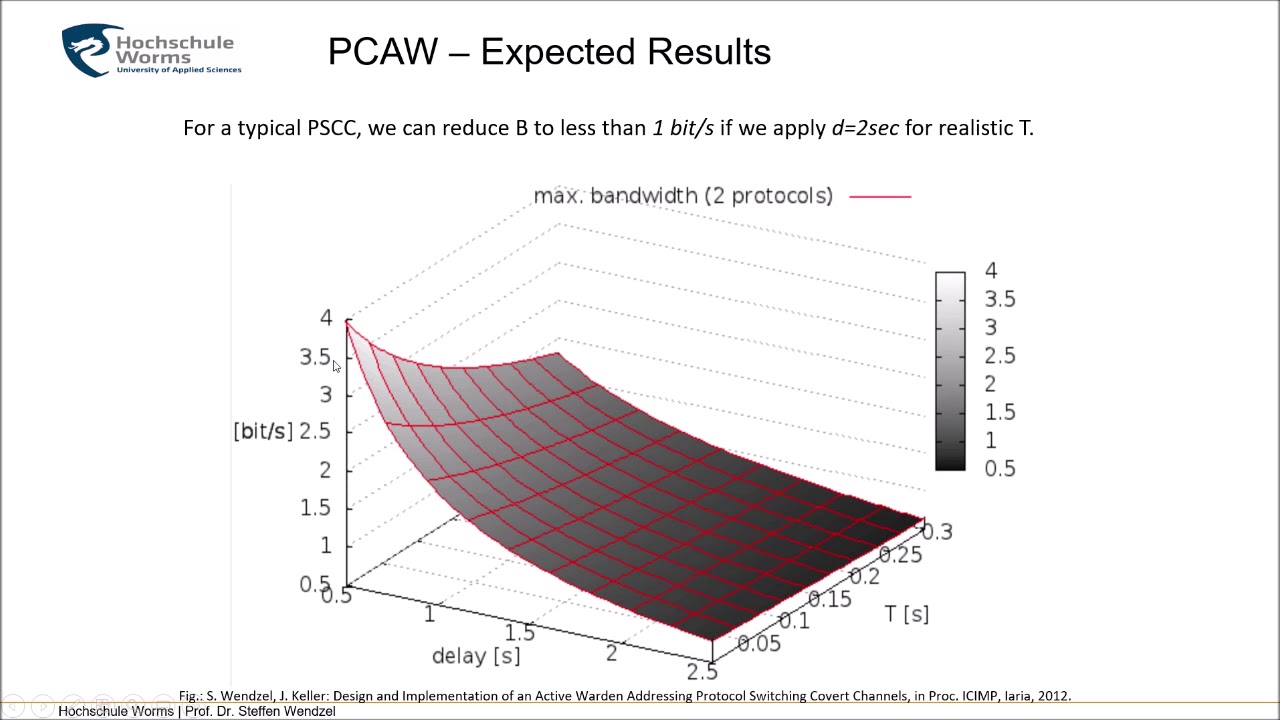
This session introduces countermeasures for sophisticated hiding techniques, namely the the Protocol Channel-aware Active Warden (PCAW) to combad protocol channels (and protocol hopping covert channels) as well as the Dynamic Warden to combat the NEL phase. Both countermeasures are of a limiting nature, i.e., they limit the available bitrate of the covert channels or extend the time it takes to transfer some piece of information.
Please note that fundamental countermeasures that are *not* specific for networks were already introduced in chapter 3 (https://www.youtube.com/watch?v=6cjsPzLscd8). Hiding patterns, including the inter-packet times pattern, were introduced in chapter 5 (https://www.youtube.com/watch?v=0ztPHur0LUY). Sophisticated Hiding Methods were introduced in Chapter 6 (https://www.youtube.com/watch?v=YicdOu10FmE) and Basic Network Level Countermeasures were introduced in Chapter 7a (https://www.youtube.com/watch?v=DW8eT5NtoxE).
List of my publications: https://wendzel.de/pub/
Me on ResearchGate: https://www.researchgate.net/profile/Steffen_Wendzel
Slides, exercises and reading assignments:
https://github.com/cdpxe/Network-Covert-Channels-A-University-level-Course/blob/master/README.md
This session introduces countermeasures for sophisticated hiding techniques, namely the the Protocol Channel-aware Active Warden (PCAW) to combad protocol channels (and protocol hopping covert channels) as well as the Dynamic Warden to combat the NEL phase. Both countermeasures are of a limiting nature, i.e., they limit the available bitrate of the covert channels or extend the time it takes to transfer some piece of information.
Please note that fundamental countermeasures that are *not* specific for networks were already introduced in chapter 3 (https://www.youtube.com/watch?v=6cjsPzLscd8). Hiding patterns, including the inter-packet times pattern, were introduced in chapter 5 (https://www.youtube.com/watch?v=0ztPHur0LUY). Sophisticated Hiding Methods were introduced in Chapter 6 (https://www.youtube.com/watch?v=YicdOu10FmE) and Basic Network Level Countermeasures were introduced in Chapter 7a (https://www.youtube.com/watch?v=DW8eT5NtoxE).
List of my publications: https://wendzel.de/pub/
Me on ResearchGate: https://www.researchgate.net/profile/Steffen_Wendzel
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
546
Likes
3
Duration
25:48
Published
May 22, 2020
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.