Must-Know Cybersecurity Interview Questions for 2025 🔐 | CodeVisium
Prepare for your cybersecurity interview with the top questions for 2025! Learn about key concepts like the CIA triad, ethical hacking, and more to boost your chances of success.

CodeVisium
216 views • Sep 18, 2025
About this video
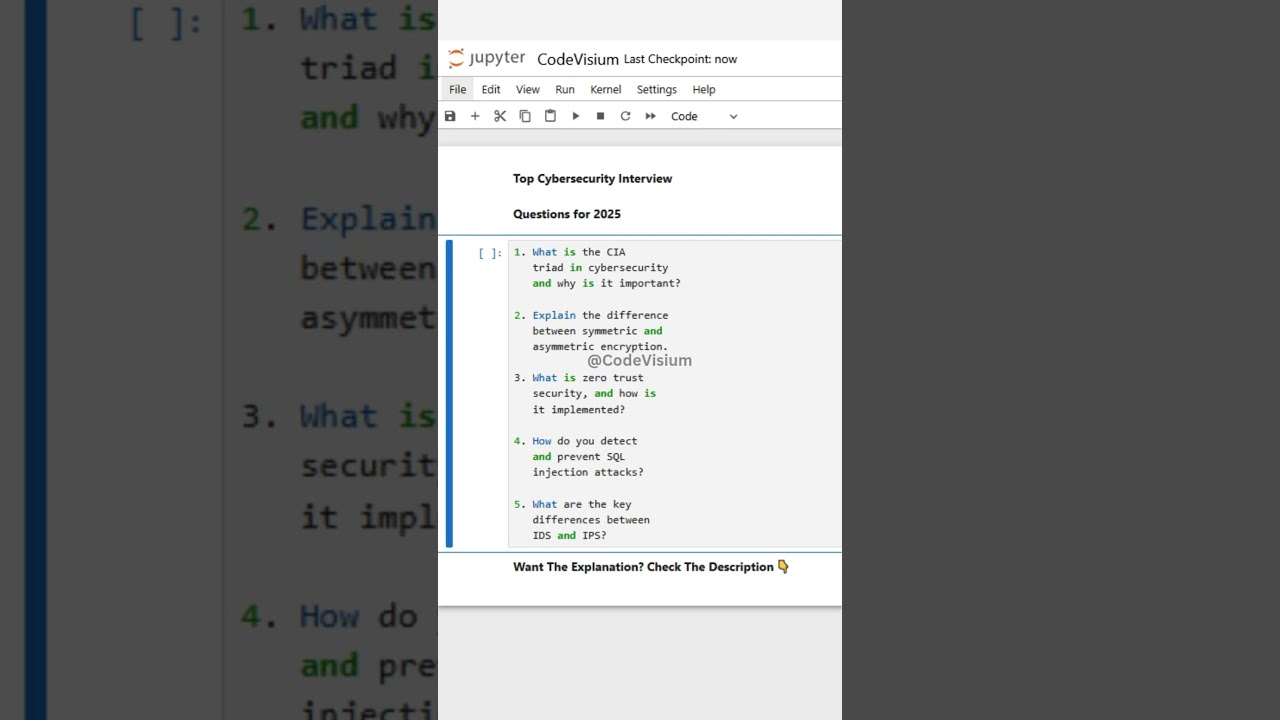
1. What is the CIA triad in cybersecurity and why is it important?
The CIA triad stands for Confidentiality, Integrity, and Availability:
Confidentiality: Ensuring only authorized users can access sensitive information (e.g., encryption, access controls).
Integrity: Ensuring data is accurate and not tampered with (e.g., hashing, checksums).
Availability: Ensuring systems and data are accessible when needed (e.g., redundancy, DDoS protection).
It’s the foundation of all cybersecurity frameworks and interviewers ask this to test fundamental knowledge.
2. Explain the difference between symmetric and asymmetric encryption.
Symmetric encryption: Same key is used for encryption and decryption. It’s fast but requires secure key sharing (e.g., AES, DES).
Asymmetric encryption: Uses a public key for encryption and a private key for decryption. More secure but computationally slower (e.g., RSA, ECC).
In real systems, both are combined—public key cryptography establishes a secure channel, and symmetric encryption handles bulk data transfer.
3. What is zero trust security, and how is it implemented?
Zero Trust assumes no device, user, or network should be inherently trusted—even if inside the corporate perimeter. Key practices include:
Least privilege access (only minimum permissions required).
Continuous authentication (MFA, conditional access).
Microsegmentation (isolating workloads to reduce attack surface).
Monitoring and logging (detecting anomalies).
Zero trust is trending in 2025 because of the rise in remote work and cloud adoption.
4. How do you detect and prevent SQL injection attacks?
Detection: Monitor logs for unusual queries, use intrusion detection systems (IDS).
Prevention:
Use parameterized queries/prepared statements.
Input validation and sanitization.
Apply the principle of least privilege to databases.
Regular vulnerability scanning and patching.
SQL injection is still one of the OWASP Top 10 vulnerabilities, making this a must-know interview question.
5. What are the key differences between IDS and IPS?
IDS (Intrusion Detection System): Monitors traffic and alerts admins of suspicious activities but does not block them.
IPS (Intrusion Prevention System): Actively blocks or mitigates threats in real-time.
Think of IDS as a security camera and IPS as a security guard. Modern systems often integrate both for layered defense.
Cybersecurity roles like Security Analyst, Ethical Hacker, SOC Analyst, and Security Engineer are booming in 2025 due to increasing cyber threats, ransomware attacks, and data breaches. These questions are frequently asked because they test your ability to:
Understand fundamental security principles (CIA triad, encryption).
Design modern architectures (zero trust).
Handle real-world attack vectors (SQL injection).
Differentiate between monitoring and prevention systems (IDS vs IPS).
By mastering these cybersecurity interview questions, you’ll show employers you can protect critical systems, secure cloud infrastructures, and stay ahead of evolving threats.
#Cybersecurity #EthicalHacking #InfoSec #ZeroTrust #Encryption #SQLInjection #IDS #IPS #InterviewPrep #CodeVisium
The CIA triad stands for Confidentiality, Integrity, and Availability:
Confidentiality: Ensuring only authorized users can access sensitive information (e.g., encryption, access controls).
Integrity: Ensuring data is accurate and not tampered with (e.g., hashing, checksums).
Availability: Ensuring systems and data are accessible when needed (e.g., redundancy, DDoS protection).
It’s the foundation of all cybersecurity frameworks and interviewers ask this to test fundamental knowledge.
2. Explain the difference between symmetric and asymmetric encryption.
Symmetric encryption: Same key is used for encryption and decryption. It’s fast but requires secure key sharing (e.g., AES, DES).
Asymmetric encryption: Uses a public key for encryption and a private key for decryption. More secure but computationally slower (e.g., RSA, ECC).
In real systems, both are combined—public key cryptography establishes a secure channel, and symmetric encryption handles bulk data transfer.
3. What is zero trust security, and how is it implemented?
Zero Trust assumes no device, user, or network should be inherently trusted—even if inside the corporate perimeter. Key practices include:
Least privilege access (only minimum permissions required).
Continuous authentication (MFA, conditional access).
Microsegmentation (isolating workloads to reduce attack surface).
Monitoring and logging (detecting anomalies).
Zero trust is trending in 2025 because of the rise in remote work and cloud adoption.
4. How do you detect and prevent SQL injection attacks?
Detection: Monitor logs for unusual queries, use intrusion detection systems (IDS).
Prevention:
Use parameterized queries/prepared statements.
Input validation and sanitization.
Apply the principle of least privilege to databases.
Regular vulnerability scanning and patching.
SQL injection is still one of the OWASP Top 10 vulnerabilities, making this a must-know interview question.
5. What are the key differences between IDS and IPS?
IDS (Intrusion Detection System): Monitors traffic and alerts admins of suspicious activities but does not block them.
IPS (Intrusion Prevention System): Actively blocks or mitigates threats in real-time.
Think of IDS as a security camera and IPS as a security guard. Modern systems often integrate both for layered defense.
Cybersecurity roles like Security Analyst, Ethical Hacker, SOC Analyst, and Security Engineer are booming in 2025 due to increasing cyber threats, ransomware attacks, and data breaches. These questions are frequently asked because they test your ability to:
Understand fundamental security principles (CIA triad, encryption).
Design modern architectures (zero trust).
Handle real-world attack vectors (SQL injection).
Differentiate between monitoring and prevention systems (IDS vs IPS).
By mastering these cybersecurity interview questions, you’ll show employers you can protect critical systems, secure cloud infrastructures, and stay ahead of evolving threats.
#Cybersecurity #EthicalHacking #InfoSec #ZeroTrust #Encryption #SQLInjection #IDS #IPS #InterviewPrep #CodeVisium
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
216
Likes
2
Duration
0:10
Published
Sep 18, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.