Mastering Symmetric Key Cryptography: Understanding the XOR Cipher 🔐
Discover how the XOR cipher forms the foundation of symmetric key cryptography. Learn its principles, applications, and importance in cybersecurity in this comprehensive guide.

Computer Science Lessons
41.2K views • Mar 3, 2019
About this video
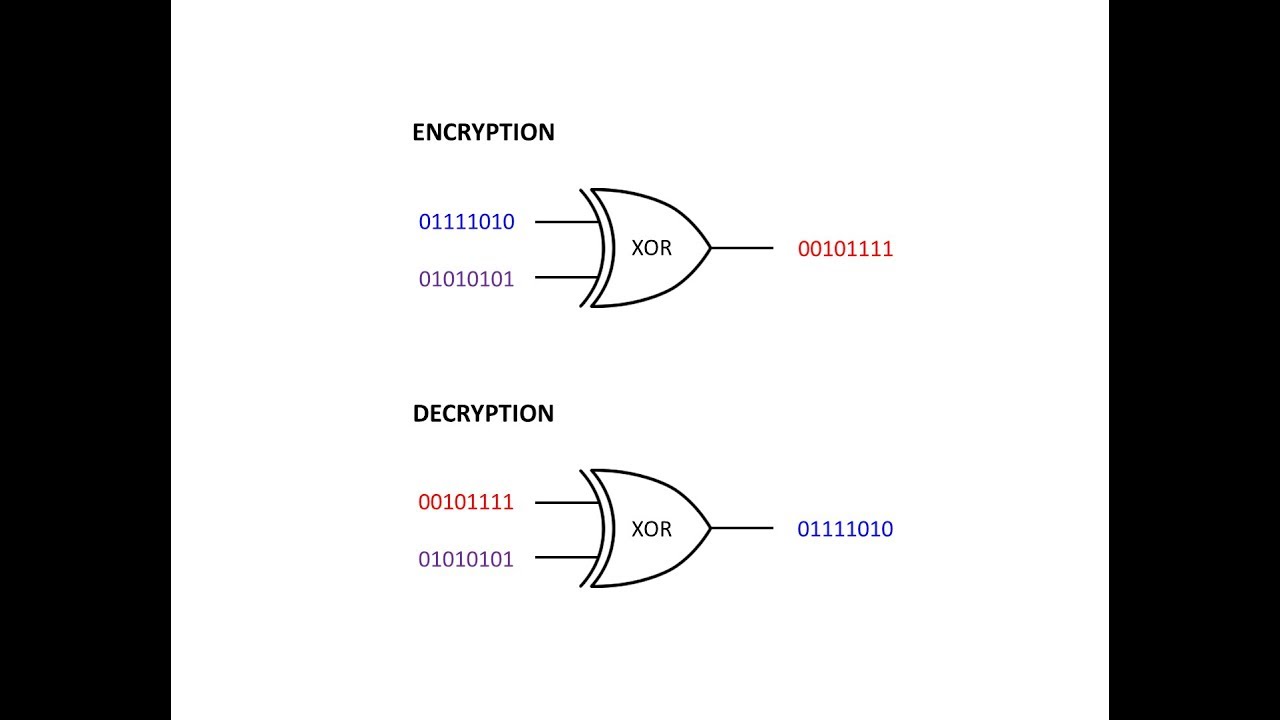
This is the fourth in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers the XOR logical operation, that is the exclusive OR operation, explaining how it can be used to encrypt and decrypt a sequence of binary digits. XOR is an important process that is employed by many modern day ciphers. Using a spreadsheet, this video demonstrates how the XOR logical operation can be applied to a single character ASCII code to encrypt and decrypt it using the same symmetric key, and the same method.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
41.2K
Likes
832
Duration
7:46
Published
Mar 3, 2019
User Reviews
4.7
(8) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.