Mastering Elliptic Curve Cryptography: How to Find Points on the Curve 🔐
Learn the fundamentals of Elliptic Curve Cryptography (ECC) and discover techniques to identify points on an elliptic curve for enhanced security in cryptographic systems.

Lectures by Shreedarshan K
48.0K views • Jul 19, 2020
About this video
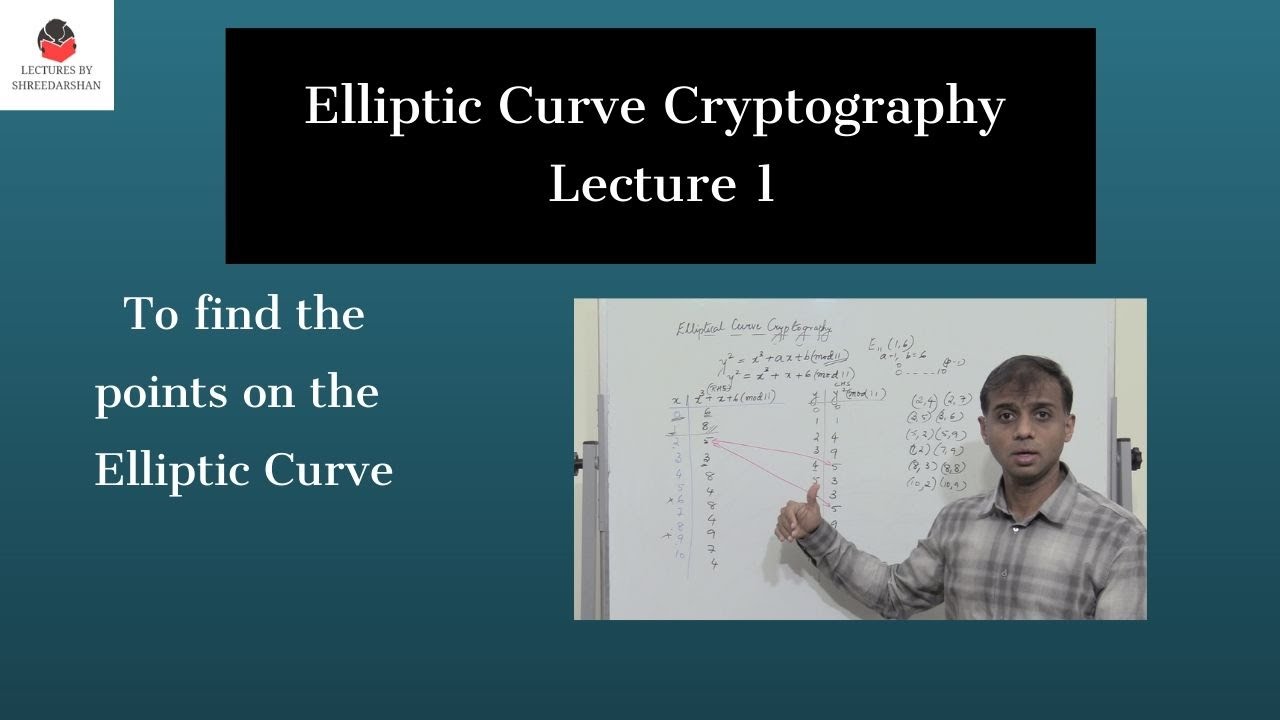
ECC - To find points on the Elliptic Curve
ECC in #Cryptography & Security
#EllipticCurveCryptography #ECC #Security #NetworkSecurity #Cryptography
1] Elliptic Curve Cryptography | Find points on the Elliptic Curve : https://youtu.be/_QR-kTypf4E
2] Elliptic Curve Cryptography |Encryption and Decryption : https://youtu.be/dhJX9kktijo
3] Elliptic Curve Cryptography |Find points P+Q and 2P : https://youtu.be/P1GFZ92EbE0
Thanks for watching.
Do like , share and subscribe
------------------------------------------------------------------------------------------------------------
🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹
Books I have authored:
Bharatiya Katha Vaibhava - Vol 1 , 2 , 3 , 4
For bulk orders and discounts DM
To buy books on Amazon:
Volume 1: https://tinyurl.com/2nrajajs
Volume 2: https://tinyurl.com/yckkrwn3
Volume 3: https://tinyurl.com/mrbf2unr
Volume 4: https://tinyurl.com/2s4ckyz9
🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹
My Social Media Handles
Facebook Page: https://www.facebook.com/profile.php?id=100063985927571
Telegram (Engineering) : https://t.me/EnggEduSDK
Telegram (Class 10) : https://t.me/MathsFor10Std
Instagram (Education) : https://www.instagram.com/edumitr4u/
Instagram (Hinduism & Spirituality) : https://www.instagram.com/bharatiya__samskruti/
Blog : https://naadopaasana.wordpress.com/
YouTube Channel (Hinduism & Spirituality) : https://www.youtube.com/channel/UCNkS1AXwAqIZXhNqrB3Uskw
🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹
📚 Important Course Playlist 📚
1] Cryptography : https://tinyurl.com/3pjs2tnd
2] Digital Electronics : https://tinyurl.com/bdfwbsrk
3] Electronics (1st Year - Basic) : https://tinyurl.com/3vduy32b
4] Error Control Coding : https://tinyurl.com/4wpr8dew
5] Discrete Mathematics : https://tinyurl.com/2p94dyr2
6] Class 10 - [CBSE/NCERT] Mathematics : https://tinyurl.com/kbdb5syw
7] Signals and Systems : https://tinyurl.com/2p8bkpf9
8] Control Systems : https://tinyurl.com/2p9hbn6m
9] Linear Algebra : https://tinyurl.com/2p8nswjw
🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹
=====================================================================
Blowfish Algorithm : https://youtu.be/qso0bla-cOc
Elliptical Curve Cryptography - 1 : https://youtu.be/_QR-kTypf4E
Brute force Attack : https://youtu.be/W9r80z1cfTk
Avalanche Effect in Cryptography : https://youtu.be/b3zEi4YcEHY
Double & Triple DES : https://youtu.be/SjuZQG89dCA
Steganography / Cryptography Differences: https://youtu.be/MaNk2kMhAQA
Four Square Cipher : https://youtu.be/54YwDWVasXo
Route Cipher : https://youtu.be/a801gnJTbAA
Fiestel Cipher Structure: https://youtu.be/EE297gIlkzQ
Network Security - Attacks : https://youtu.be/8Swn1yj4ccs
Network Security - Authentication using Message Encryption : https://youtu.be/UQbWZvSw4IU
Fiestel Cipher Structure: https://youtu.be/EE297gIlkzQ
Diffie Hellman Key Exchange: https://youtu.be/dloRO4tfE1I
Euler's Totient Function [Euler's Phi Function]:https://youtu.be/h-UVsqZvWng
Fermat's Theorem - Explanation with example: https://youtu.be/cq2vIqyfJAg
s DES - Key Generation : https://youtu.be/mS2VC7vbbNc
Differences between s-DES and DES: https://youtu.be/WGqZTYwG_uU
Primitive Root : https://youtu.be/tngcCcZrezA
-----------------------------------------------------------------------
Encryption, Elliptic Curve Cryptography,
Decryption,
Ciphers,
Symmetric Ciphers,
Cryptography,
Network Security,
Polynomials,
Primitive root
DES
Data Encryption Standard
Confusion
Diffusion
Hill Cipher
Playfair Cipher
Caesar Cipher
Hill Cipher
Steganography
Triple DES
Meet in the middle attack
Blowfish Algorithm
Eulers Theorem
Chinese Remainder Theorem
IDEA
GCD
Number Theory
ECC in #Cryptography & Security
#EllipticCurveCryptography #ECC #Security #NetworkSecurity #Cryptography
1] Elliptic Curve Cryptography | Find points on the Elliptic Curve : https://youtu.be/_QR-kTypf4E
2] Elliptic Curve Cryptography |Encryption and Decryption : https://youtu.be/dhJX9kktijo
3] Elliptic Curve Cryptography |Find points P+Q and 2P : https://youtu.be/P1GFZ92EbE0
Thanks for watching.
Do like , share and subscribe
------------------------------------------------------------------------------------------------------------
🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹
Books I have authored:
Bharatiya Katha Vaibhava - Vol 1 , 2 , 3 , 4
For bulk orders and discounts DM
To buy books on Amazon:
Volume 1: https://tinyurl.com/2nrajajs
Volume 2: https://tinyurl.com/yckkrwn3
Volume 3: https://tinyurl.com/mrbf2unr
Volume 4: https://tinyurl.com/2s4ckyz9
🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹
My Social Media Handles
Facebook Page: https://www.facebook.com/profile.php?id=100063985927571
Telegram (Engineering) : https://t.me/EnggEduSDK
Telegram (Class 10) : https://t.me/MathsFor10Std
Instagram (Education) : https://www.instagram.com/edumitr4u/
Instagram (Hinduism & Spirituality) : https://www.instagram.com/bharatiya__samskruti/
Blog : https://naadopaasana.wordpress.com/
YouTube Channel (Hinduism & Spirituality) : https://www.youtube.com/channel/UCNkS1AXwAqIZXhNqrB3Uskw
🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹
📚 Important Course Playlist 📚
1] Cryptography : https://tinyurl.com/3pjs2tnd
2] Digital Electronics : https://tinyurl.com/bdfwbsrk
3] Electronics (1st Year - Basic) : https://tinyurl.com/3vduy32b
4] Error Control Coding : https://tinyurl.com/4wpr8dew
5] Discrete Mathematics : https://tinyurl.com/2p94dyr2
6] Class 10 - [CBSE/NCERT] Mathematics : https://tinyurl.com/kbdb5syw
7] Signals and Systems : https://tinyurl.com/2p8bkpf9
8] Control Systems : https://tinyurl.com/2p9hbn6m
9] Linear Algebra : https://tinyurl.com/2p8nswjw
🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹
=====================================================================
Blowfish Algorithm : https://youtu.be/qso0bla-cOc
Elliptical Curve Cryptography - 1 : https://youtu.be/_QR-kTypf4E
Brute force Attack : https://youtu.be/W9r80z1cfTk
Avalanche Effect in Cryptography : https://youtu.be/b3zEi4YcEHY
Double & Triple DES : https://youtu.be/SjuZQG89dCA
Steganography / Cryptography Differences: https://youtu.be/MaNk2kMhAQA
Four Square Cipher : https://youtu.be/54YwDWVasXo
Route Cipher : https://youtu.be/a801gnJTbAA
Fiestel Cipher Structure: https://youtu.be/EE297gIlkzQ
Network Security - Attacks : https://youtu.be/8Swn1yj4ccs
Network Security - Authentication using Message Encryption : https://youtu.be/UQbWZvSw4IU
Fiestel Cipher Structure: https://youtu.be/EE297gIlkzQ
Diffie Hellman Key Exchange: https://youtu.be/dloRO4tfE1I
Euler's Totient Function [Euler's Phi Function]:https://youtu.be/h-UVsqZvWng
Fermat's Theorem - Explanation with example: https://youtu.be/cq2vIqyfJAg
s DES - Key Generation : https://youtu.be/mS2VC7vbbNc
Differences between s-DES and DES: https://youtu.be/WGqZTYwG_uU
Primitive Root : https://youtu.be/tngcCcZrezA
-----------------------------------------------------------------------
Encryption, Elliptic Curve Cryptography,
Decryption,
Ciphers,
Symmetric Ciphers,
Cryptography,
Network Security,
Polynomials,
Primitive root
DES
Data Encryption Standard
Confusion
Diffusion
Hill Cipher
Playfair Cipher
Caesar Cipher
Hill Cipher
Steganography
Triple DES
Meet in the middle attack
Blowfish Algorithm
Eulers Theorem
Chinese Remainder Theorem
IDEA
GCD
Number Theory
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
48.0K
Likes
941
Duration
13:43
Published
Jul 19, 2020
User Reviews
4.7
(9) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now