Mastering Block Ciphers: Modes of Operation Explained 🔐
Discover how block ciphers work, explore ideal cipher concepts, and learn about popular modes like CBC and Counter Mode to enhance your information security knowledge.

Aleksander Essex
42.1K views • Oct 2, 2020
About this video
Information Security - Week 3
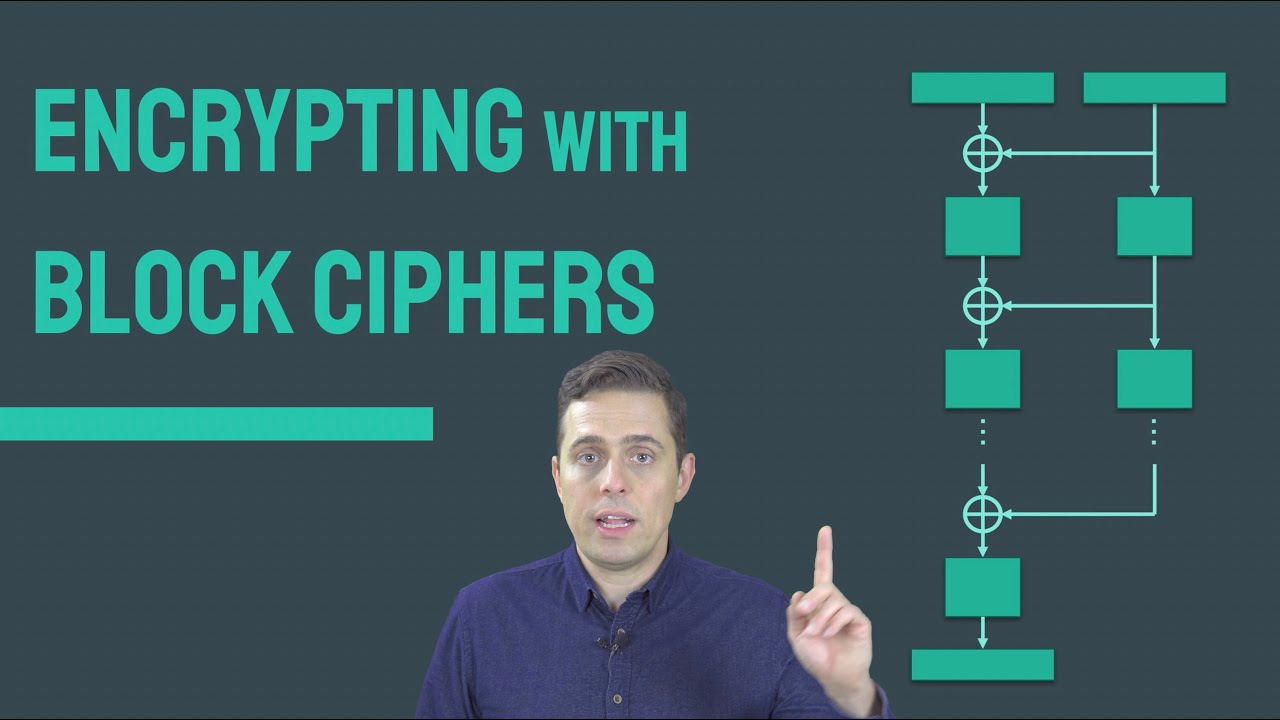
In this video: block ciphers, ideal block ciphers, cipher modes of operation, cipher-block chaining, CBC mode, counter mode, CTR mode, randomized encryption, initialization vectors, the Advanced Encryption Standard, AES
Undergraduate course on networking security and cryptography taught by Aleksander Essex, Ph.D., P.Eng., Associate professor of Software Engineering, Associate Chair (Graduate), Department of Electrical and Computer Engineering, Western University, Canada
Website:
https://essex.cc
Twitter:
https://twitter.com/aleksessex
Course topics include:
Confidentiality, authenticity, integrity, ciphers, plaintext, ciphertext, encryption, decryption, keys, key generation function, uniform random, semantic security, bits of security, brute force, Kerckhoff's principle, semantic security, ciphertext indistinguishability, IND-CPA, INC-CCA, block ciphers, message padding, PKCS 7, modes of operation, initialization vector, pseudo-random permutation, counter mode, cipher block chaining, electronic codebook mode, counter mode, CBC, ECB, CTR, Advanced Encryption Standard, AES, hash functions, random oracles, pre-image resistance, collision resistance, SHA-1, SHA-256, SHA3, SHA-513, MD5, message authentication codes, MACs, Galois counter mode, GCM, AEC-GCM, public-key cryptography, Diffie-Hellman, public-key agreement, Elliptic curve Diffie-Hellman, DHE, ECDHE, digital signatures, ECDSA, RSA signatures, PKCS v1.5, digital certificates, X.509, public-key infrastructure, PKI, certificate pinning, certificate revocation, CRL, trust store, Transport Layer Security, TLS, TLS 1.2, TLS 1.3, HTTP over TLS, HTTPS Secure Shell, SSH, ciphersuite, client hello, server hello, VPNs, TOR, 802.11, wifi encryption, client authentication, passwords, password hashing, password lengths, single sign-on, federated identity
----
Music: Arp Bounce - Geographer
Support by RFM - NCM: https://bit.ly/2xGHypM
Slide template: Slidesgo including Flaticons with infographics & images by Freepik
In this video: block ciphers, ideal block ciphers, cipher modes of operation, cipher-block chaining, CBC mode, counter mode, CTR mode, randomized encryption, initialization vectors, the Advanced Encryption Standard, AES
Undergraduate course on networking security and cryptography taught by Aleksander Essex, Ph.D., P.Eng., Associate professor of Software Engineering, Associate Chair (Graduate), Department of Electrical and Computer Engineering, Western University, Canada
Website:
https://essex.cc
Twitter:
https://twitter.com/aleksessex
Course topics include:
Confidentiality, authenticity, integrity, ciphers, plaintext, ciphertext, encryption, decryption, keys, key generation function, uniform random, semantic security, bits of security, brute force, Kerckhoff's principle, semantic security, ciphertext indistinguishability, IND-CPA, INC-CCA, block ciphers, message padding, PKCS 7, modes of operation, initialization vector, pseudo-random permutation, counter mode, cipher block chaining, electronic codebook mode, counter mode, CBC, ECB, CTR, Advanced Encryption Standard, AES, hash functions, random oracles, pre-image resistance, collision resistance, SHA-1, SHA-256, SHA3, SHA-513, MD5, message authentication codes, MACs, Galois counter mode, GCM, AEC-GCM, public-key cryptography, Diffie-Hellman, public-key agreement, Elliptic curve Diffie-Hellman, DHE, ECDHE, digital signatures, ECDSA, RSA signatures, PKCS v1.5, digital certificates, X.509, public-key infrastructure, PKI, certificate pinning, certificate revocation, CRL, trust store, Transport Layer Security, TLS, TLS 1.2, TLS 1.3, HTTP over TLS, HTTPS Secure Shell, SSH, ciphersuite, client hello, server hello, VPNs, TOR, 802.11, wifi encryption, client authentication, passwords, password hashing, password lengths, single sign-on, federated identity
----
Music: Arp Bounce - Geographer
Support by RFM - NCM: https://bit.ly/2xGHypM
Slide template: Slidesgo including Flaticons with infographics & images by Freepik
Video Information
Views
42.1K
Likes
836
Duration
21:42
Published
Oct 2, 2020
User Reviews
4.7
(8) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.