Mastering Authenticated Encryption: Ensuring Data Integrity and Security 🔐
Explore the fundamentals of authenticated encryption, including ciphertext integrity, redundancy in encryption, and popular composition techniques like Encrypt-and-MAC and MAC-then-Encrypt for robust data protection.

Mihir Bellare
1.1K views • Apr 2, 2021
About this video
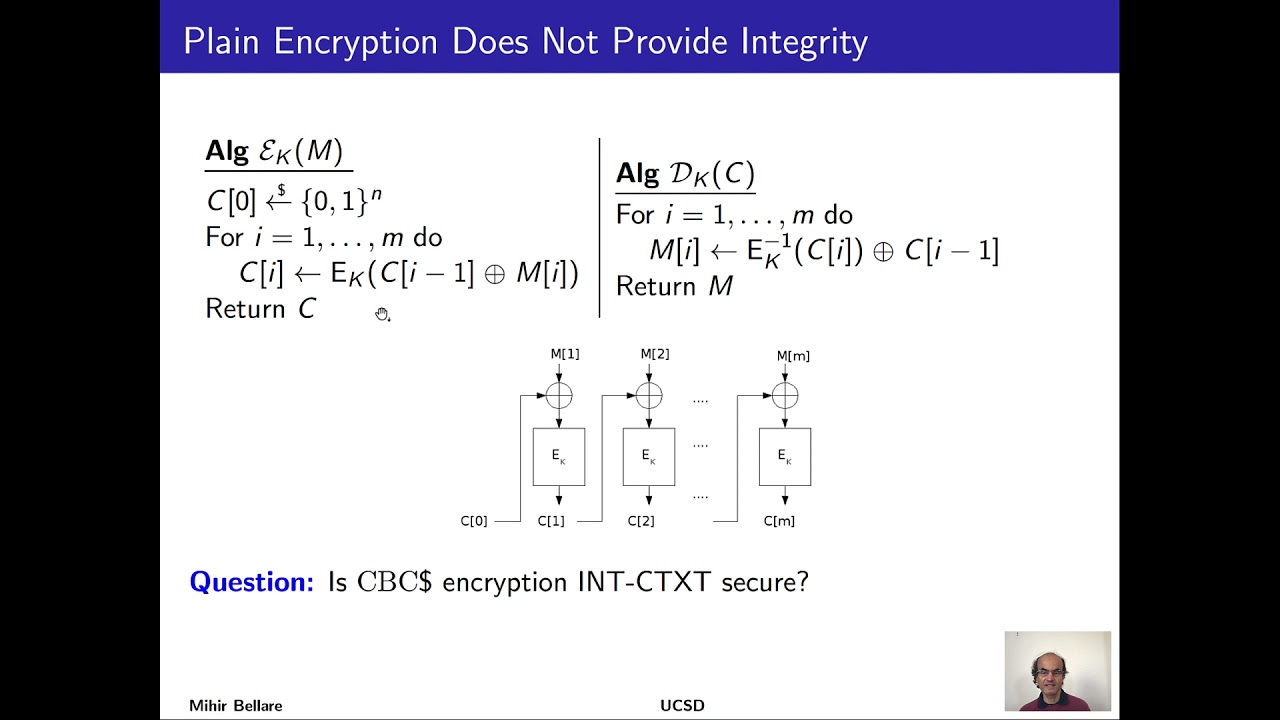
Authenticated encryption. Integrity of ciphertexts (INT-CTXT). Encryption with redundancy and its failure. Generic composition: Encrypt-and-Mac, Mac-then-Encrypt, Encrypt-then-Mac. AEAD. OCB, GCM.
Video Information
Views
1.1K
Likes
14
Duration
01:04:52
Published
Apr 2, 2021
User Reviews
4.3
(1)