Master Cryptography & Network Security: Special Discount Offer 🔐
Unlock essential skills in cryptography, computer security, and networks with this comprehensive course. Enroll now on Coursera and enjoy a special discount!

Ho Manh Hung
5 views • Sep 28, 2020
About this video
Link to this course on coursera( Special discount)
https://click.linksynergy.com/deeplink?id=Gw/ETjJoU9M&mid=40328&murl=https%3A%2F%2Fwww.coursera.org%2Flearn%2Fcrypto
This is the best Computer Security and Networks course
Cryptography I overview
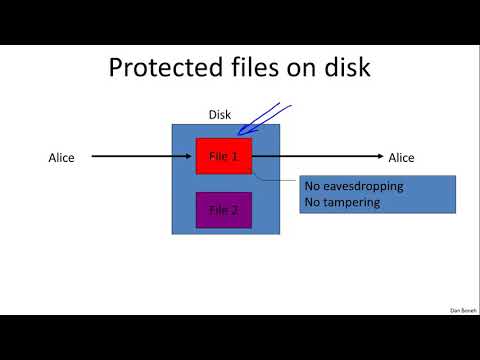
Cryptography is an indispensable tool for protecting information in computer systems. In this course you will learn the inner workings of cryptographic systems and how to correctly use them in real-world applications. The course begins with a detailed discussion of how two parties who have a shared secret key can communicate securely when a powerful adversary eavesdrops and tampers with traffic. We will examine many deployed protocols and analyze mistakes in existing systems. The second half of the course discusses public-key techniques that let two parties generate a shared secret key. Throughout the course participants will be exposed to many exciting open problems in the field and work on fun (optional) programming projects. In a second course (Crypto II) we will cover more advanced cryptographic tasks such as zero-knowledge, privacy mechanisms, and other forms of encryption.
You can download this course and watch offline for free after enroll
https://click.linksynergy.com/deeplink?id=Gw/ETjJoU9M&mid=40328&murl=https%3A%2F%2Fwww.coursera.org%2Flearn%2Fcrypto
This is the best Computer Security and Networks course
Cryptography I overview
Cryptography is an indispensable tool for protecting information in computer systems. In this course you will learn the inner workings of cryptographic systems and how to correctly use them in real-world applications. The course begins with a detailed discussion of how two parties who have a shared secret key can communicate securely when a powerful adversary eavesdrops and tampers with traffic. We will examine many deployed protocols and analyze mistakes in existing systems. The second half of the course discusses public-key techniques that let two parties generate a shared secret key. Throughout the course participants will be exposed to many exciting open problems in the field and work on fun (optional) programming projects. In a second course (Crypto II) we will cover more advanced cryptographic tasks such as zero-knowledge, privacy mechanisms, and other forms of encryption.
You can download this course and watch offline for free after enroll
Video Information
Views
5
Duration
10:35
Published
Sep 28, 2020
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.