Master CISSP Domain 5 with Proven Questions & Answers 📘
Boost your CISSP exam prep with our comprehensive Domain 5 questions, answers, and score guide. Download the PDF now at learnexams.com to ace your certification!

smart education
58 views • Nov 6, 2023
About this video
download pdf at https://learnexams.com/search/study?query=aqa
..CISSP Domain 5: Questions & Answers: A+ Score Guide
Course
Institution
CISSP Domain
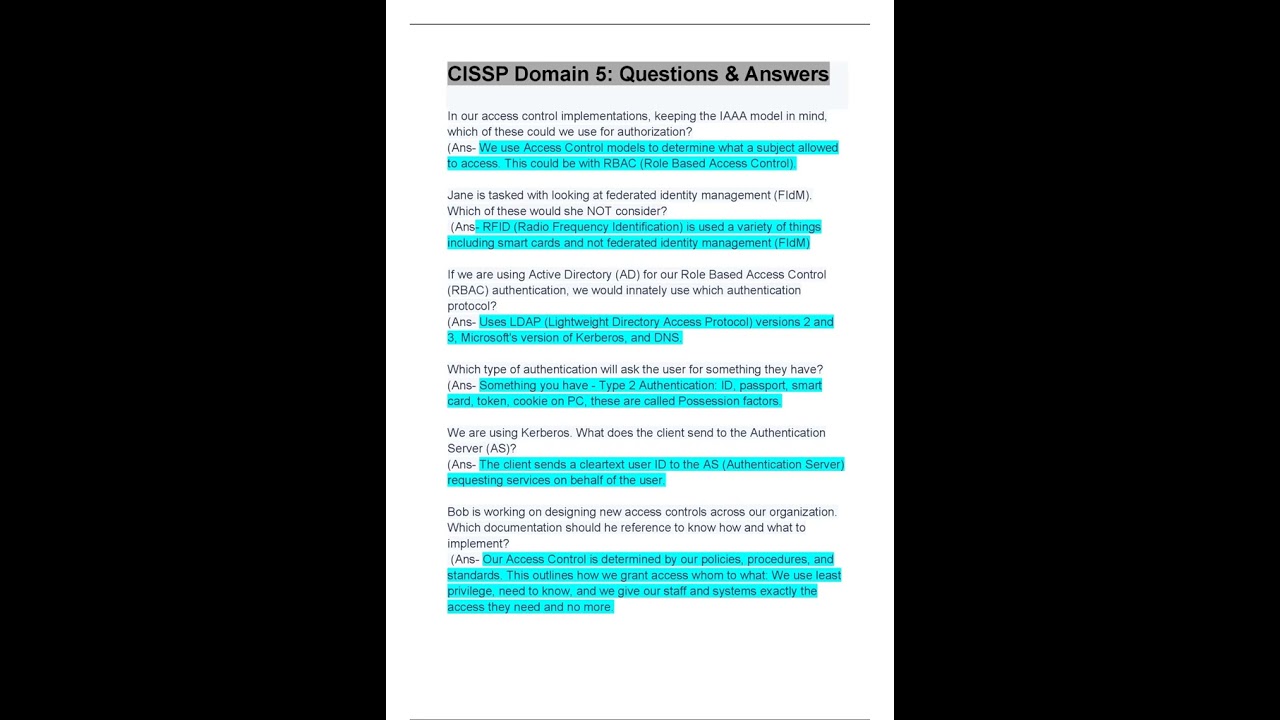
In our access control implementations, keeping the IAAA model in mind, which of these could we use for authorization? (Ans- We use Access Control models to determine what a subject allowed to access. This could be with RBAC (Role Based Access Control). Jane is tasked with looking at federated identity management (FIdM). Which of these would she NOT consider? (Ans- RFID (Radio Frequency Identification) is used a variety of things including smart cards and not federated identity management (FIdM) If we are using Active Directory (AD) for our Role Based Access Control (RBAC) authentication, we would innately use which authentication protocol? (Ans- Uses LDAP (Lightweight Directory Access Protocol) versions 2 and 3, Microsoft's version of Kerberos, and DNS. Which type of authentication will ask the user for something they have? (Ans- Something you have - Type 2 Authentication: ID, passport, smart card, token, cookie on PC, these are called Possession factors. We are using Kerberos. What does the client send to the Authentication Server (AS)? (Ans- The client sends a cleartext user ID to the AS (Authentication Server) requesting services on behalf of the user. Bob is working on designing new access controls across our organization. Which documentation should he reference to know how and what to implement? (Ans- Our Access Control is determined by our policies, procedures, and standards. This outlines how we grant access whom to what: We use least privilege, need to know, and we give our staff and systems exactly the access they need and no more.
..
..
.. download pdf at this website;https://learnexams.com/
email us at;support@learnexams.com
instagram at;https://www.instagram.com/learnexams_/
..CISSP Domain 5: Questions & Answers: A+ Score Guide
Course
Institution
CISSP Domain
In our access control implementations, keeping the IAAA model in mind, which of these could we use for authorization? (Ans- We use Access Control models to determine what a subject allowed to access. This could be with RBAC (Role Based Access Control). Jane is tasked with looking at federated identity management (FIdM). Which of these would she NOT consider? (Ans- RFID (Radio Frequency Identification) is used a variety of things including smart cards and not federated identity management (FIdM) If we are using Active Directory (AD) for our Role Based Access Control (RBAC) authentication, we would innately use which authentication protocol? (Ans- Uses LDAP (Lightweight Directory Access Protocol) versions 2 and 3, Microsoft's version of Kerberos, and DNS. Which type of authentication will ask the user for something they have? (Ans- Something you have - Type 2 Authentication: ID, passport, smart card, token, cookie on PC, these are called Possession factors. We are using Kerberos. What does the client send to the Authentication Server (AS)? (Ans- The client sends a cleartext user ID to the AS (Authentication Server) requesting services on behalf of the user. Bob is working on designing new access controls across our organization. Which documentation should he reference to know how and what to implement? (Ans- Our Access Control is determined by our policies, procedures, and standards. This outlines how we grant access whom to what: We use least privilege, need to know, and we give our staff and systems exactly the access they need and no more.
..
..
.. download pdf at this website;https://learnexams.com/
email us at;support@learnexams.com
instagram at;https://www.instagram.com/learnexams_/
Video Information
Views
58
Likes
2
Duration
0:11
Published
Nov 6, 2023
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.