Master CBC Padding Attacks in Cryptography 🔐
Learn how CBC padding attacks exploit cryptographic vulnerabilities and how to defend against them. Perfect for aspiring security professionals seeking practical insights!

Ton Tuong Linh
249 views • Nov 7, 2020
About this video
Link to this course:
https://click.linksynergy.com/deeplink?id=Gw/ETjJoU9M&mid=40328&murl=https%3A%2F%2Fwww.coursera.org%2Flearn%2Fcrypto
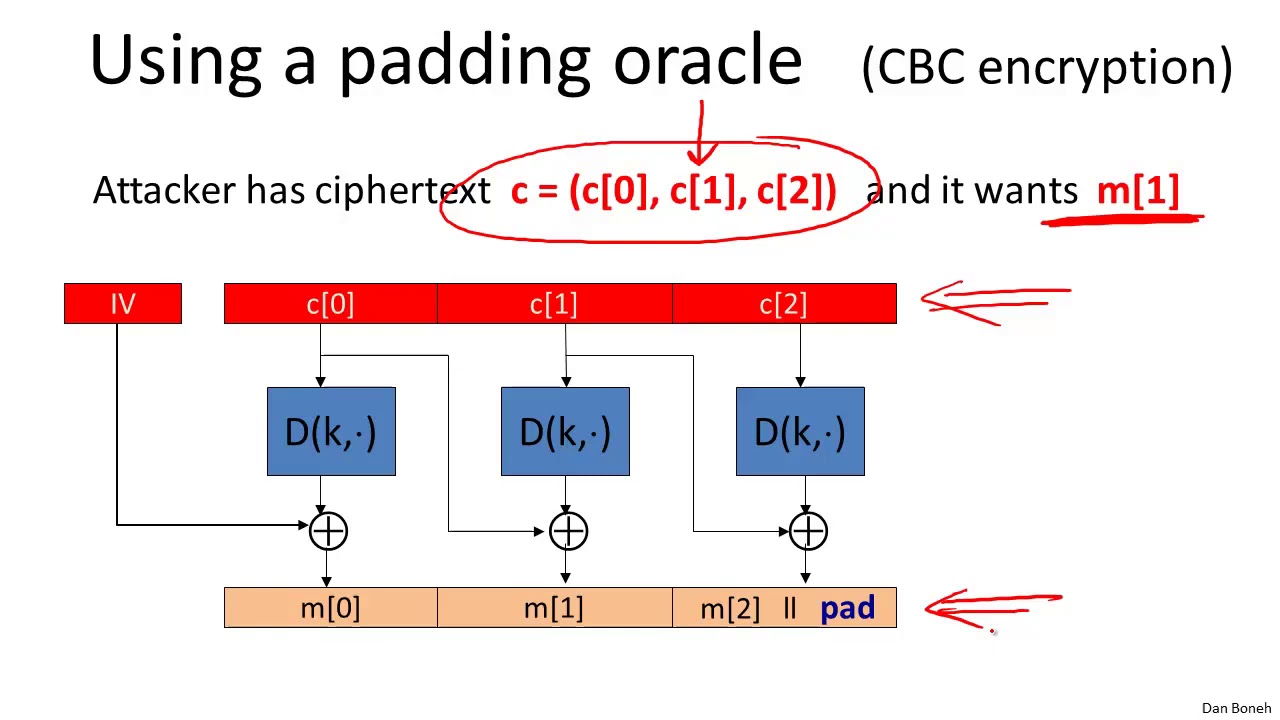
CBC Padding Attacks - Cryptography I
Cryptography is an indispensable tool for protecting information in computer systems. In this course you will learn the inner workings of cryptographic systems and how to correctly use them in real-world applications. The course begins with a detailed discussion of how two parties who have a shared secret key can communicate securely when a powerful adversary eavesdrops and tampers with traffic. We will examine many deployed protocols and analyze mistakes in existing systems. The second half of the course discusses public-key techniques that let two parties generate a shared secret key. Throughout the course participants will be exposed to many exciting open problems in the field and work on fun (optional) programming projects. In a second course (Crypto II) we will cover more advanced cryptographic tasks such as zero-knowledge, privacy mechanisms, and other forms of encryption.
Cryptography, Cryptographic Attacks, Public-Key Cryptography, Symmetric-Key Algorithm
Cutting edge cryptography topics. Good explanations and slides, but pause button is highly recommended. Can be a bit too mathematical for the general public, and not very formal for mathematicians.,A really interesting and in-depth course. It is pretty challenging and requires good math/proof skills, but still quite fun. The course could use more study materials, for example lecture notes.
Week 4. This week's topic is authenticated encryption: encryption methods that ensure both confidentiality and integrity. We will also discuss a few odds and ends such as how to search on encrypted data. This is our last week studying symmetric encryption. Next week we start with key management and public-key cryptography. As usual there is also an extra credit programming project. This week's project involves a bit of networking to experiment with a chosen ciphertext attack on a toy web site.
CBC Padding Attacks - Cryptography I
Copyright Disclaimer under Section 107 of the copyright act 1976, allowance is made for fair use for purposes such as criticism, comment, news reporting, scholarship, and research. Fair use is a use permitted by copyright statute that might otherwise be infringing. Non-profit, educational or personal use tips the balance in favour of fair use.
https://click.linksynergy.com/deeplink?id=Gw/ETjJoU9M&mid=40328&murl=https%3A%2F%2Fwww.coursera.org%2Flearn%2Fcrypto
CBC Padding Attacks - Cryptography I
Cryptography is an indispensable tool for protecting information in computer systems. In this course you will learn the inner workings of cryptographic systems and how to correctly use them in real-world applications. The course begins with a detailed discussion of how two parties who have a shared secret key can communicate securely when a powerful adversary eavesdrops and tampers with traffic. We will examine many deployed protocols and analyze mistakes in existing systems. The second half of the course discusses public-key techniques that let two parties generate a shared secret key. Throughout the course participants will be exposed to many exciting open problems in the field and work on fun (optional) programming projects. In a second course (Crypto II) we will cover more advanced cryptographic tasks such as zero-knowledge, privacy mechanisms, and other forms of encryption.
Cryptography, Cryptographic Attacks, Public-Key Cryptography, Symmetric-Key Algorithm
Cutting edge cryptography topics. Good explanations and slides, but pause button is highly recommended. Can be a bit too mathematical for the general public, and not very formal for mathematicians.,A really interesting and in-depth course. It is pretty challenging and requires good math/proof skills, but still quite fun. The course could use more study materials, for example lecture notes.
Week 4. This week's topic is authenticated encryption: encryption methods that ensure both confidentiality and integrity. We will also discuss a few odds and ends such as how to search on encrypted data. This is our last week studying symmetric encryption. Next week we start with key management and public-key cryptography. As usual there is also an extra credit programming project. This week's project involves a bit of networking to experiment with a chosen ciphertext attack on a toy web site.
CBC Padding Attacks - Cryptography I
Copyright Disclaimer under Section 107 of the copyright act 1976, allowance is made for fair use for purposes such as criticism, comment, news reporting, scholarship, and research. Fair use is a use permitted by copyright statute that might otherwise be infringing. Non-profit, educational or personal use tips the balance in favour of fair use.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
249
Likes
2
Duration
14:07
Published
Nov 7, 2020
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now