Man-in-the-Middle Attack: Eavesdropping & Security
Learn how man-in-the-middle attacks intercept communications and how to secure against eavesdropping in cryptanalysis. 🔐

Quick Cybersecurity Study
449 views • Mar 11, 2025
About this video
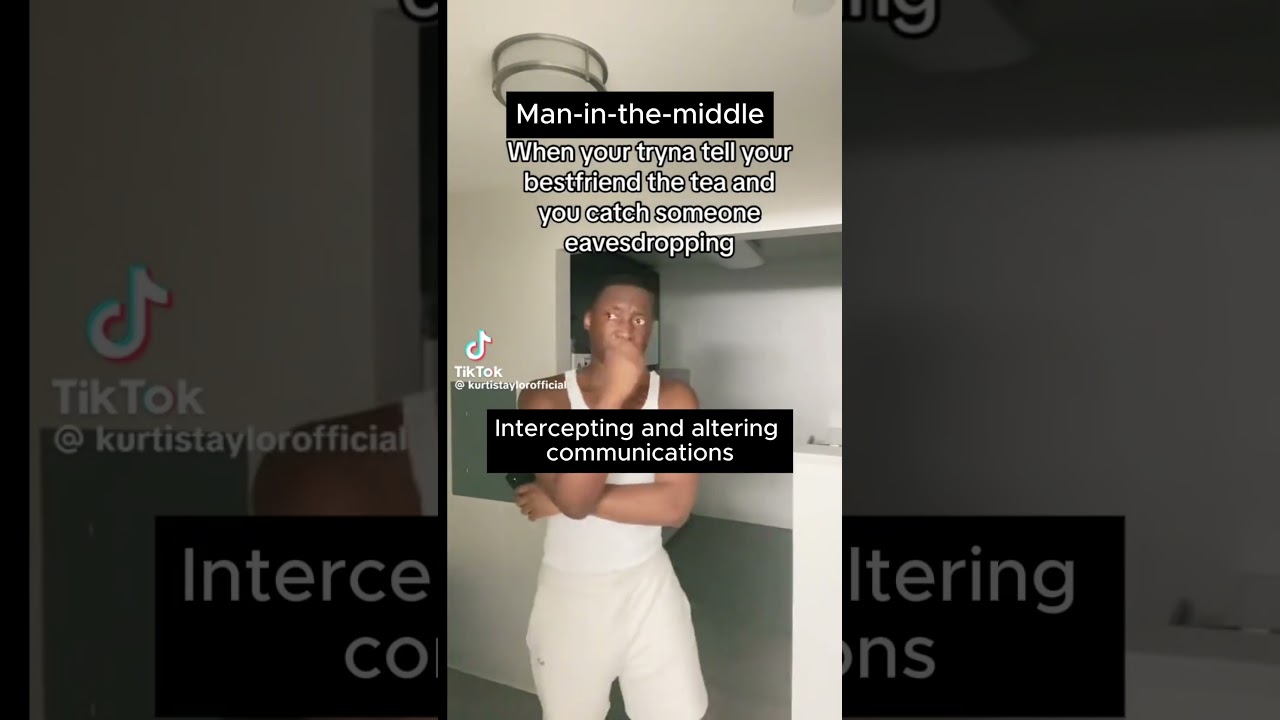
🕵️♂️ **Man-in-the-Middle Attack in Cryptanalysis & Secure by Design = Telling Someone Something… But Catching Someone Eavesdropping!** 🔐✨
Just like someone secretly listening in on your conversation, **Man-in-the-Middle (MitM) Attacks** intercept communication between two parties to steal or alter information—without them knowing. 💻⚠️
With **Secure by Design**, encryption and authentication prevent attackers from snooping on sensitive data! ✅🔐
#CyberSecurity #ManInTheMiddleAttack #Cryptanalysis #Encryption #SecureByDesign #CyberDefense #DataProtection #InfoSec #TechEducation #CyberSecTraining #VisualLearning #CyberSecurityCertification #ITKnowledge #TechForBeginners #LearnCyberSecurity #SecurityAwareness #CyberSecCommunity
Just like someone secretly listening in on your conversation, **Man-in-the-Middle (MitM) Attacks** intercept communication between two parties to steal or alter information—without them knowing. 💻⚠️
With **Secure by Design**, encryption and authentication prevent attackers from snooping on sensitive data! ✅🔐
#CyberSecurity #ManInTheMiddleAttack #Cryptanalysis #Encryption #SecureByDesign #CyberDefense #DataProtection #InfoSec #TechEducation #CyberSecTraining #VisualLearning #CyberSecurityCertification #ITKnowledge #TechForBeginners #LearnCyberSecurity #SecurityAwareness #CyberSecCommunity
Video Information
Views
449
Likes
4
Duration
0:06
Published
Mar 11, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.