Lecture 22: Cryptographic Hash Functions – Applications & Digital Signatures 🔐
Discover how cryptographic hash functions are used in message authentication, digital signatures, and more in this comprehensive lecture. Perfect for understanding real-world security applications!

Muhammad Raees
26 views • Sep 4, 2020
About this video
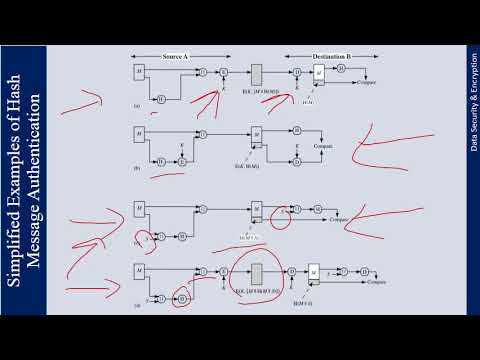
This lecture explains Applications of Cryptographic Hash Functions like Message Authentication, Digital Signatures and few Others. It also provides description of Two Simple Hash Functions and Security Requirements for Cryptographic Hash Functions.
Video Information
Views
26
Likes
1
Duration
39:25
Published
Sep 4, 2020