LABS 28: Mastering White Space Steganography to Conceal Data in Network Communications 🕵️♂️
Explore how to hide sensitive information using white space steganography techniques in network traffic. Learn practical methods for covert data transmission and detection avoidance.

Ethical Hacking Project
2.0K views • Jul 22, 2018
About this video
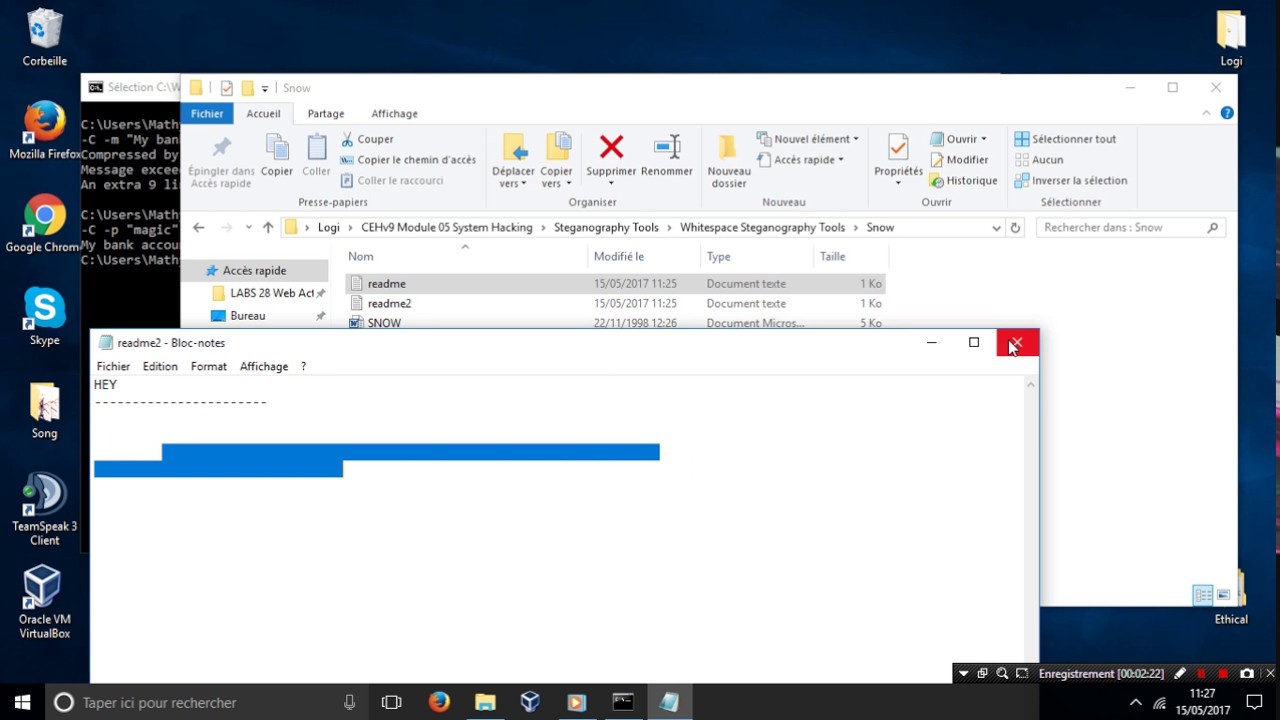
Lab Scenario :
Network steganography describes all the methods used for transmitting data over a network without it being detected. Several methods for hiding data in a network have been proposed, but the main drawback of most of them is that they do not offer a secondary lyer of protection. If steganography is detected, the data is in plain text. Attackers use steganoraphy to transfer sensitive information out of the target system un detected to be an expert Ethical Hacker and Penetration Tester, you must have sound knowledge of various steganography techniques.
Network steganography describes all the methods used for transmitting data over a network without it being detected. Several methods for hiding data in a network have been proposed, but the main drawback of most of them is that they do not offer a secondary lyer of protection. If steganography is detected, the data is in plain text. Attackers use steganoraphy to transfer sensitive information out of the target system un detected to be an expert Ethical Hacker and Penetration Tester, you must have sound knowledge of various steganography techniques.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
2.0K
Likes
13
Duration
2:25
Published
Jul 22, 2018
User Reviews
4.1
(1) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now