ICICS 2022 Keynote: Practical Privacy Solutions for Blockchain Networks 🔒
Discover innovative approaches to enhance privacy in blockchain systems with Guang Gong from the University of Waterloo. Explore the latest research on securing blockchain networks in both permissionless and permissioned settings.

UniKentCyberSec
62 views • Oct 31, 2022
About this video
Speaker: Guang Gong, University of Waterloo, Canada
Session Chair: Liqun Chen, University of Surrey, UK
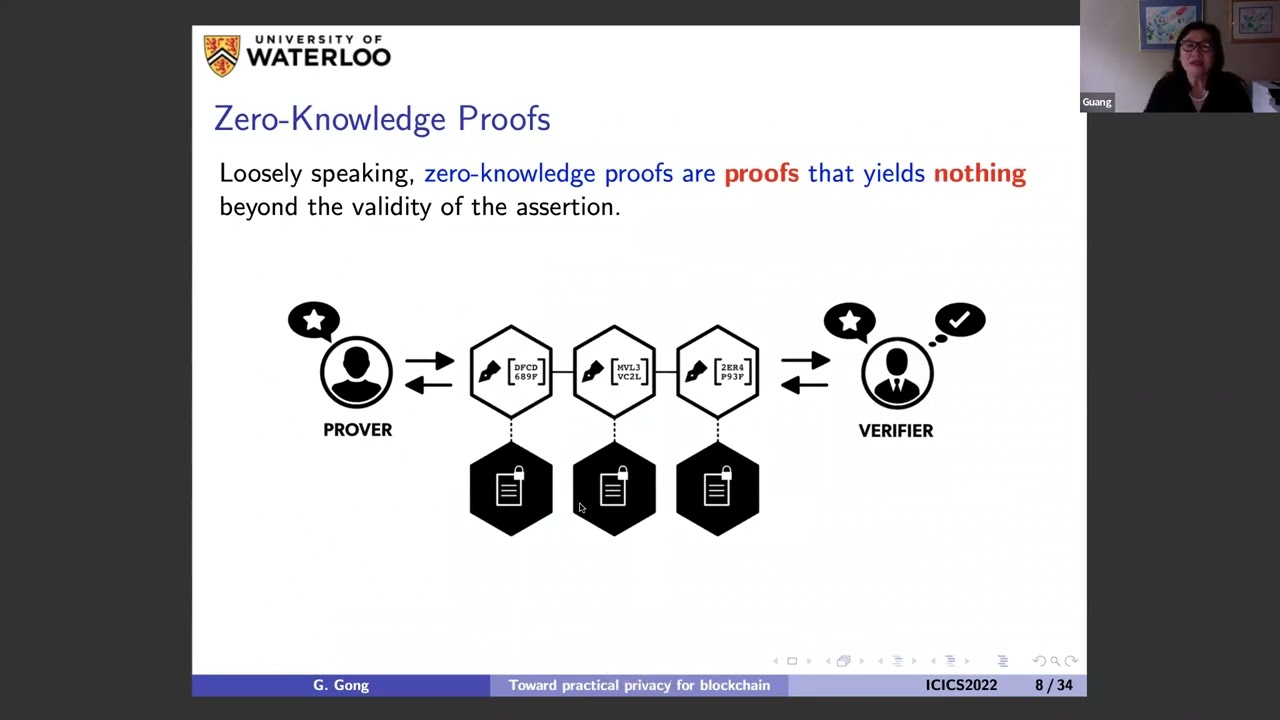
Abstract: Permissionless and permissioned blockchain systems, which are decentralized and capable of transferring trusted consensus, computation, and immutable data between untrusted entities, have strong potential for numerous applications where value or data is transferred/shared, stored and processed. All existing blockchain privacy solutions employ advanced “cryptographic engines”, namely zero-knowledge proof verifiable computation schemes. Currently, the zero-knowledge Succinct Non-interactive Argument of Knowledge (zkSNARK) approach is the most promising, which is built on (fully) homomorphic encryption (e.g., GGPR13/Groth16 implemented in Zcash) or probabilistic check proofs (PCP) (e.g., the lightweight coin Ligero, Stark and Aurora). In this talk, I will first present an overview for the current research along this line, then I will provide a concrete example of zkSNARK schemes, namely, Polaris, our recent work, for Rank-1 Constraint Satisfaction (RICS) circuits. The verifier’s costs and the proof size are bounded by the square of logarithm of the size of an arithmetic circuit. It does not require a trusted setup and plausibly post-quantum secure when employed secure hash function is plausibly post-quantum resistant. For instance, for verifying a SHA-256 preimage (about 23k AND gates) in zero-knowledge with 128 bits security, the proof size is less than 150kB and the verification time is less than 11ms, both competitive to existing systems with better concrete verifiers' complexity.
To read research papers at ICICS 2022, please visit:
https://icics2022.cyber.kent.ac.uk/program.php
or
https://link.springer.com/book/9783031157769
Session Chair: Liqun Chen, University of Surrey, UK
Abstract: Permissionless and permissioned blockchain systems, which are decentralized and capable of transferring trusted consensus, computation, and immutable data between untrusted entities, have strong potential for numerous applications where value or data is transferred/shared, stored and processed. All existing blockchain privacy solutions employ advanced “cryptographic engines”, namely zero-knowledge proof verifiable computation schemes. Currently, the zero-knowledge Succinct Non-interactive Argument of Knowledge (zkSNARK) approach is the most promising, which is built on (fully) homomorphic encryption (e.g., GGPR13/Groth16 implemented in Zcash) or probabilistic check proofs (PCP) (e.g., the lightweight coin Ligero, Stark and Aurora). In this talk, I will first present an overview for the current research along this line, then I will provide a concrete example of zkSNARK schemes, namely, Polaris, our recent work, for Rank-1 Constraint Satisfaction (RICS) circuits. The verifier’s costs and the proof size are bounded by the square of logarithm of the size of an arithmetic circuit. It does not require a trusted setup and plausibly post-quantum secure when employed secure hash function is plausibly post-quantum resistant. For instance, for verifying a SHA-256 preimage (about 23k AND gates) in zero-knowledge with 128 bits security, the proof size is less than 150kB and the verification time is less than 11ms, both competitive to existing systems with better concrete verifiers' complexity.
To read research papers at ICICS 2022, please visit:
https://icics2022.cyber.kent.ac.uk/program.php
or
https://link.springer.com/book/9783031157769
Video Information
Views
62
Likes
1
Duration
58:22
Published
Oct 31, 2022
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now