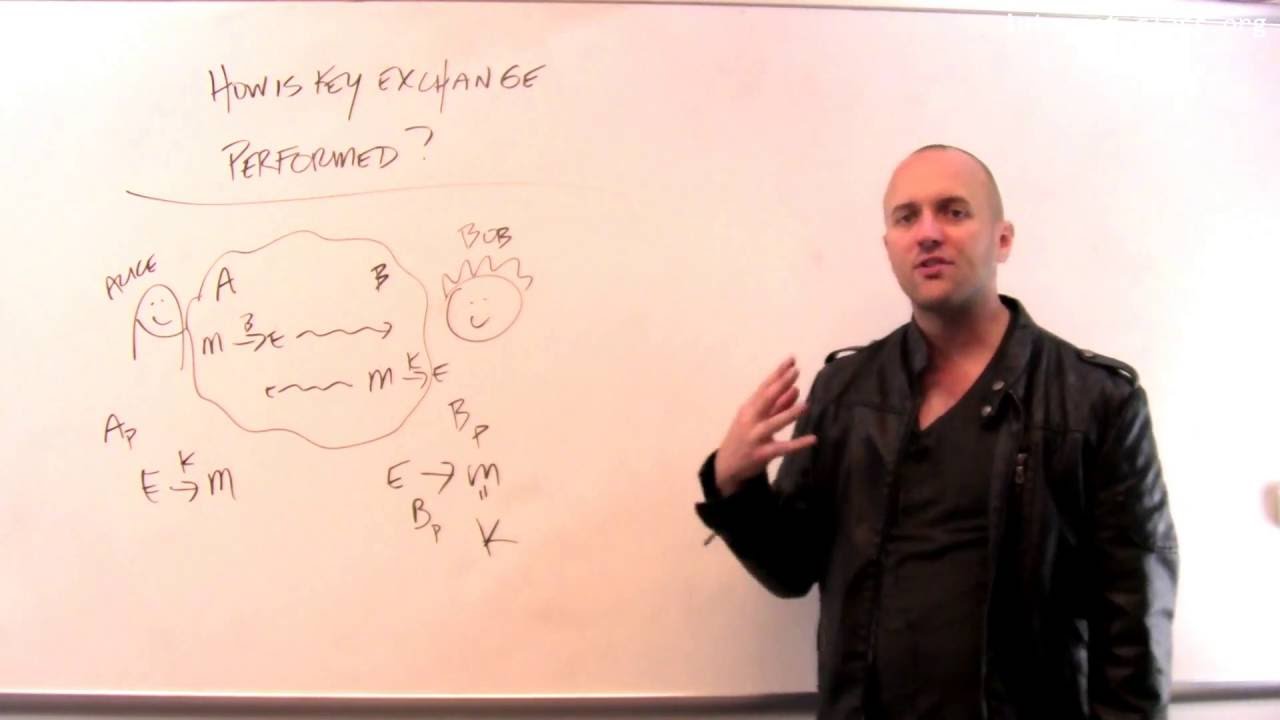
How do two parties exchange keys to communicate securely?
While asymmetric (public-key) encryption does allow two parties to communicate security without exchanging keys, asymmetric encryption requires expensive com...

internet-class
2.5K views • Oct 17, 2016
About this video
While asymmetric (public-key) encryption does allow two parties to communicate security without exchanging keys, asymmetric encryption requires expensive computation for each message. Symmetric key algorithms are much more efficient. As a result, the two techniques are usually applied to establish and maintain a secure connection. Asymmetric encryption is used to protect the initial part of the connection where symmetric keys are exchanged. Once communicating parties agree on symmetric keys, symmetric encryption is used for the remainder of the communication.
Credits: Talking: Geoffrey Challen (Assistant Professor, Computer Science and Engineering, University at Buffalo). Producing: Greg Bunyea (Undergraduate, Computer Science and Engineering, University at Buffalo).
Part of the https://www.internet-class.org online internet course. A blue Systems Research Group (https://blue.cse.buffalo.edu) production.
Credits: Talking: Geoffrey Challen (Assistant Professor, Computer Science and Engineering, University at Buffalo). Producing: Greg Bunyea (Undergraduate, Computer Science and Engineering, University at Buffalo).
Part of the https://www.internet-class.org online internet course. A blue Systems Research Group (https://blue.cse.buffalo.edu) production.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
2.5K
Likes
43
Duration
4:47
Published
Oct 17, 2016
User Reviews
4.5
(2) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now