Evaluating the Efficiency of Hybrid Encryption on Embedded Devices 🔒
Discover how a hybrid encryption scheme performs on embedded systems, highlighting its speed and security for IoT and embedded applications.

Computer Science & IT Conference Proceedings
37 views • Oct 5, 2024
About this video
Performance Measurement of a Hybrid Encryption Scheme on an Embedded System
Luis Alejandro Vargas Oviedo, Edwar Jacinto Gómez and Fernando Martínez Santa, Universidad Distrital Francisco Jose de Caldas, Colombia
Abstract
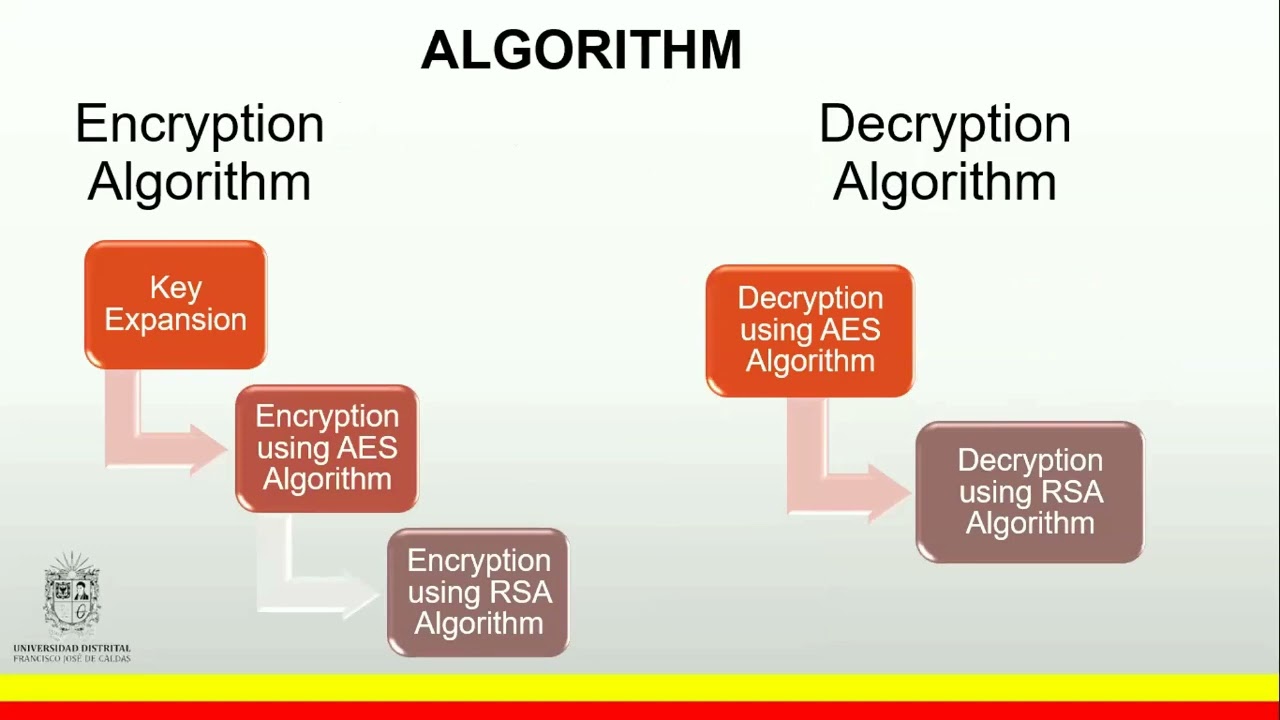
In the last decades, information security has become a priority with exponential growth since technological developments must be supported so that their operation has reliable levels to store relevant data, and the levels of reliability are those required by the current environment. This is key to developing modern requirements that apply to data protection. It should be noted that the most common tool to encrypt information in code is AES (Advanced Encryption Standard), which is a block cipher algorithm that assigns binary keys and performs rounds of exchange to hide the message; on the other hand, is RSA (Rivest - Shamir - Adleman) which is an algorithm used for key assignment. Finally, the HASH key extension function is used for cryptographic analysis to verify the authenticity and origin of the data. In this research, a source code that combines the AES, RSA, and HASH encryption algorithms is designed to run on two hybrid acceleration units to compare the data processing in terms of time and reliability.
Keywords
Information Security, Key Extension, System Embedded, Mixed Encryption Scheme, Hybrid Acceleration Unit
Full Text : https://aircconline.com/csit/papers/vol14/csit141805.pdf
Abstract URL : https://aircconline.com/csit/abstract/v14n18/csit141805.html
Volume URL : https://airccse.org/csit/V14N18.html
#informationsecurity #security #blockchain #cybersecurity #protection #cryptography
Luis Alejandro Vargas Oviedo, Edwar Jacinto Gómez and Fernando Martínez Santa, Universidad Distrital Francisco Jose de Caldas, Colombia
Abstract
In the last decades, information security has become a priority with exponential growth since technological developments must be supported so that their operation has reliable levels to store relevant data, and the levels of reliability are those required by the current environment. This is key to developing modern requirements that apply to data protection. It should be noted that the most common tool to encrypt information in code is AES (Advanced Encryption Standard), which is a block cipher algorithm that assigns binary keys and performs rounds of exchange to hide the message; on the other hand, is RSA (Rivest - Shamir - Adleman) which is an algorithm used for key assignment. Finally, the HASH key extension function is used for cryptographic analysis to verify the authenticity and origin of the data. In this research, a source code that combines the AES, RSA, and HASH encryption algorithms is designed to run on two hybrid acceleration units to compare the data processing in terms of time and reliability.
Keywords
Information Security, Key Extension, System Embedded, Mixed Encryption Scheme, Hybrid Acceleration Unit
Full Text : https://aircconline.com/csit/papers/vol14/csit141805.pdf
Abstract URL : https://aircconline.com/csit/abstract/v14n18/csit141805.html
Volume URL : https://airccse.org/csit/V14N18.html
#informationsecurity #security #blockchain #cybersecurity #protection #cryptography
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
37
Duration
10:37
Published
Oct 5, 2024
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.