Essential Information Security Measures: Authentication, Digital Signatures, Firewalls & More 🔐
Learn key security techniques like authentication, digital signatures, firewalls, and steganography to protect your data. Master these vital measures to enhance your information security skills!

5-Minute Lessons by Victor
973 views • Dec 6, 2023
About this video
#digitalsignature #authentication #steganography #firewalls #informationsecurity #encryption
By the end of the video, learners will be able to
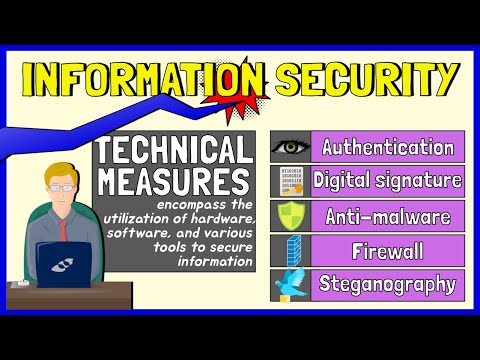
1. Define the concept of authentication.
2. List down authentication factors;
3. Identify examples of single-factor authentication, two-factor authentication, and multi-factor authentication;
4. Explain how digital signature works;
5. Enumerate anti-malware strategies;
6. Differentiate between anti-malware and antivirus solutions.
7. Discuss importance of packetization in data transmission in a network;
8. Explain packet filtering, proxying, and network address translation;
9. Compare and contrast hardware firewalls and software firewalls; and
10. Discuss the purposes of steganography.
Here are the helpful references for this material:
🔗 Barney, N., Schacklett, M. E., & Rosencrance, L. (n.d.). What is Authentication? | Definition from TechTarget. TechTarget. Retrieved December 4, 2023, from https://www.techtarget.com/searchsecurity/definition/authentication
🔗 CryptoPurview. (2019, July 14). How Digital Signature Work And Use In Blockchain. CryptoPurview. Retrieved December 4, 2023, from https://cryptopurview.com/how-digital-signature-work-and-use-in-blockchain/
🔗 Forcepoint. (n.d.). Firewalls: Defined, Explained, and Explored. Forcepoint. Retrieved December 4, 2023, from https://www.forcepoint.com/cyber-edu/firewall
🔗 Fruhlinger, J. (2020, January 17). What is information security? Definition, principles, and jobs. CSO Online. Retrieved December 4, 2023, from https://www.csoonline.com/article/568841/what-is-information-security-definition-principles-and-jobs.html
🔗 Mendible, J. G. (2021, May 6). What is a hash and what is its role in the electronic signature? Uanataca. Retrieved December 4, 2023, from https://web.uanataca.com/en/blog/technology/hash-and-electronic-signature
🔗 Verma, E. (2023, October 20). What is Steganography? A Complete Guide with Types & Examples. Simplilearn.com. Retrieved December 4, 2023, from https://www.simplilearn.com/what-is-steganography-article
If you find the video helpful, please like, share, comment, and consider subscribing. Thanks for your time!
By the end of the video, learners will be able to
1. Define the concept of authentication.
2. List down authentication factors;
3. Identify examples of single-factor authentication, two-factor authentication, and multi-factor authentication;
4. Explain how digital signature works;
5. Enumerate anti-malware strategies;
6. Differentiate between anti-malware and antivirus solutions.
7. Discuss importance of packetization in data transmission in a network;
8. Explain packet filtering, proxying, and network address translation;
9. Compare and contrast hardware firewalls and software firewalls; and
10. Discuss the purposes of steganography.
Here are the helpful references for this material:
🔗 Barney, N., Schacklett, M. E., & Rosencrance, L. (n.d.). What is Authentication? | Definition from TechTarget. TechTarget. Retrieved December 4, 2023, from https://www.techtarget.com/searchsecurity/definition/authentication
🔗 CryptoPurview. (2019, July 14). How Digital Signature Work And Use In Blockchain. CryptoPurview. Retrieved December 4, 2023, from https://cryptopurview.com/how-digital-signature-work-and-use-in-blockchain/
🔗 Forcepoint. (n.d.). Firewalls: Defined, Explained, and Explored. Forcepoint. Retrieved December 4, 2023, from https://www.forcepoint.com/cyber-edu/firewall
🔗 Fruhlinger, J. (2020, January 17). What is information security? Definition, principles, and jobs. CSO Online. Retrieved December 4, 2023, from https://www.csoonline.com/article/568841/what-is-information-security-definition-principles-and-jobs.html
🔗 Mendible, J. G. (2021, May 6). What is a hash and what is its role in the electronic signature? Uanataca. Retrieved December 4, 2023, from https://web.uanataca.com/en/blog/technology/hash-and-electronic-signature
🔗 Verma, E. (2023, October 20). What is Steganography? A Complete Guide with Types & Examples. Simplilearn.com. Retrieved December 4, 2023, from https://www.simplilearn.com/what-is-steganography-article
If you find the video helpful, please like, share, comment, and consider subscribing. Thanks for your time!
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
973
Likes
6
Duration
14:09
Published
Dec 6, 2023
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.