ESC8 | NTLM Relay Attack & Windows Exploits 🔐
Learn how hackers exploit NTLM relay attacks to compromise Windows authentication protocols in this detailed explanation.

Redfox Security
1.2K views • Aug 31, 2024
About this video
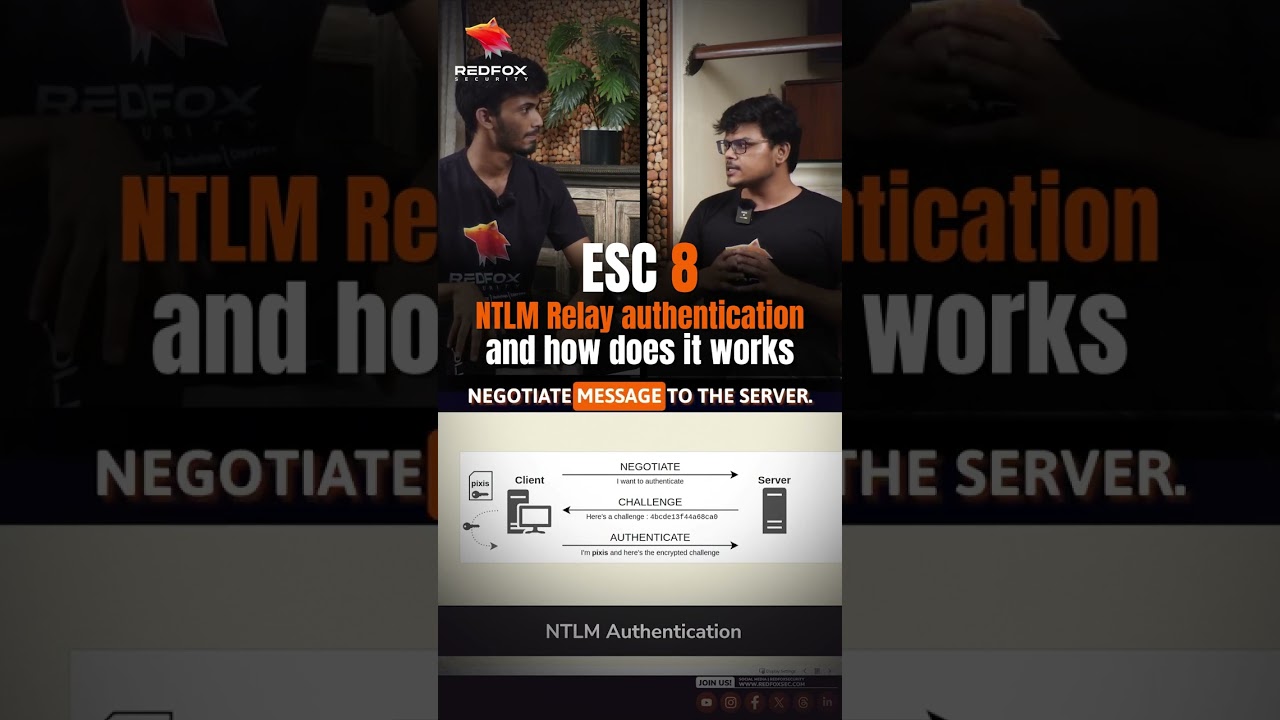
Dive into the mechanics of the *ESC8 NTLM Relay Attack* , a sophisticated method hackers use to exploit *Windows authentication protocols.* This video breaks down *how attackers intercept and relay NTLM authentication requests to escalate privileges and gain unauthorized access within an Active Directory environment.*
*Understanding this attack is critical for IT admins, security professionals, and penetration testers aiming to defend or assess Windows environments effectively.*
*Watch the full video here:* https://youtu.be/ia2ConrqlCQ
*Build your cybersecurity skills with expert-led courses:* https://academy.redfoxsec.com/
*Join the Redfox Security community and stay connected:* https://linktr.ee/redfoxsec
*Powered by Redfox Cyber Security Pvt. Ltd.*
*Important Note:*
This video is for educational purposes only. It demonstrates ethical hacking techniques in authorized, controlled environments. Using these methods without documented consent is prohibited and unethical.
*Disclaimer:*
Redfox Security is not responsible for any misuse or unauthorized actions by viewers.
*Who Are We?*
Redfox Security is a global penetration testing firm with over ten years of cybersecurity experience. We help businesses, from startups to large corporations, protect against threats. Our expert team provides top-tier security consulting services across four countries, dedicated to ensuring your business grows securely.
*Website:* https://redfoxsec.com
*LinkedIn:* https://www.linkedin.com/company/redfoxsec
*Facebook:* https://www.facebook.com/redfoxsec
*Instagram:* https://www.instagram.com/redfoxcybersecurity
*Twitter:* https://x.com/redfoxsec
Like, share, and subscribe for more cybersecurity insights and tutorials.
Turn on notifications so you never miss an upload.
#ESC8 #NTLMRelay #WindowsSecurity #ActiveDirectory #CyberSecurity #PenetrationTesting #RedTeam #InfoSec #RedfoxSecurity #AuthenticationAttack #redfox #redfoxacademy
*Understanding this attack is critical for IT admins, security professionals, and penetration testers aiming to defend or assess Windows environments effectively.*
*Watch the full video here:* https://youtu.be/ia2ConrqlCQ
*Build your cybersecurity skills with expert-led courses:* https://academy.redfoxsec.com/
*Join the Redfox Security community and stay connected:* https://linktr.ee/redfoxsec
*Powered by Redfox Cyber Security Pvt. Ltd.*
*Important Note:*
This video is for educational purposes only. It demonstrates ethical hacking techniques in authorized, controlled environments. Using these methods without documented consent is prohibited and unethical.
*Disclaimer:*
Redfox Security is not responsible for any misuse or unauthorized actions by viewers.
*Who Are We?*
Redfox Security is a global penetration testing firm with over ten years of cybersecurity experience. We help businesses, from startups to large corporations, protect against threats. Our expert team provides top-tier security consulting services across four countries, dedicated to ensuring your business grows securely.
*Website:* https://redfoxsec.com
*LinkedIn:* https://www.linkedin.com/company/redfoxsec
*Facebook:* https://www.facebook.com/redfoxsec
*Instagram:* https://www.instagram.com/redfoxcybersecurity
*Twitter:* https://x.com/redfoxsec
Like, share, and subscribe for more cybersecurity insights and tutorials.
Turn on notifications so you never miss an upload.
#ESC8 #NTLMRelay #WindowsSecurity #ActiveDirectory #CyberSecurity #PenetrationTesting #RedTeam #InfoSec #RedfoxSecurity #AuthenticationAttack #redfox #redfoxacademy
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
1.2K
Likes
21
Duration
0:52
Published
Aug 31, 2024
User Reviews
4.5
(1)