Enhanced Keccak Cryptographic Functions Portfolio 🛡️ | FOSDEM 2017 Presentation
Discover a comprehensive collection of optimized cryptographic functions based on Keccak, expanding beyond SHA-3. Presented by Gilles Van Assche at FOSDEM 2017, this overview highlights advancements in secure hashing and cryptography.

FOSDEM
948 views • Mar 6, 2018
About this video
by Gilles Van Assche
At: FOSDEM 2017
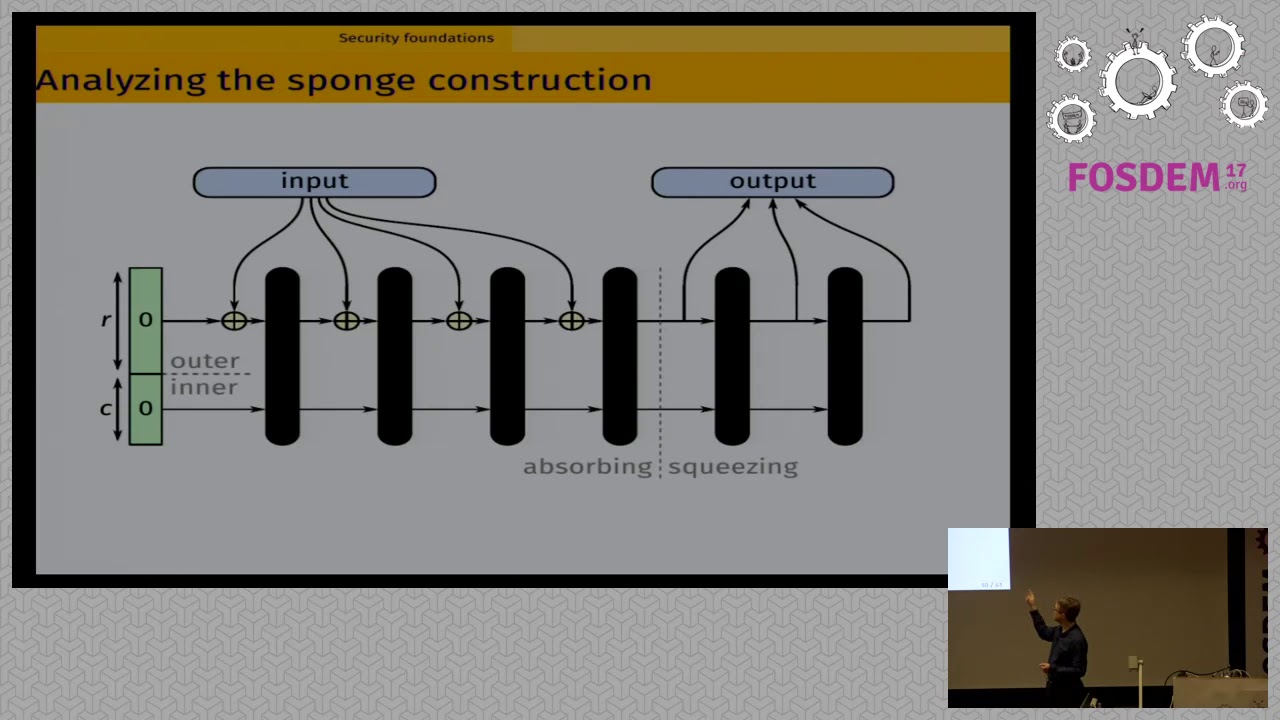
Since its adoption as the SHA-3 standard, Keccak has grown out of the merehashing functionality. We present a consistent set of cryptographic functions,for fast hashing, pseudo-random bit generation, authentication orauthenticated encryption, that enjoy very competitive safety margin vs speedratios. We highlight the bases for the security of these functions and diveinto their software implementations.
Beyond the FIPS 202 standard functions derived from Keccak (i.e., SHA-3 hashfunctions and SHAKE{128,256} extendable output functions), we present severalinteresting proposals, consistently based on the same permutation or its roundfunction. Among others:
* For authenticated encryption, Ketje and Keyak are schemes that were selected for the third round of the [CAESAR competition](http://competitions.cr.yp.to/caesar-submissions.html). In particular, Keyak proposes interesting features when protecting a stream of data flowing on a network. It exploits the parallelism in modern processors to achieve a high throughput. * [KangarooTwelve](http://eprint.iacr.org/2016/770.pdf) is a recently published arbitrary-output-length hash function. We designed it so that the implementation can automatically adapt to the available degree of parallelism. On Intel's Haswell and Skylake architectures, it achieves a speed below 1.5 cycles/byte for long inputs.
Two key aspects will be covered.
First, the essential goal of these functions is to remain secure despiteadvances in cryptanalysis. We will explain explain how we base the security ontwo strong pillars: the track record of third-party cryptanalysis and thegeneric security of the underlying construction.
Second, we will explore the [Keccak CodePackage](https://github.com/gvanas/KeccakCodePackage) and its two-levelstructure. The high-level cryptographic services are implemented in plain C,without any specific optimizations. The low-level services implement thepermutations and the state input/output functions, for which we provideoptimized code for different platforms. Another interesting topic to discussis how the parallelism is exploited on modern processors with SIMD units.
Room: Janson
Scheduled start: 2017-02-05 09:00:00
At: FOSDEM 2017
Since its adoption as the SHA-3 standard, Keccak has grown out of the merehashing functionality. We present a consistent set of cryptographic functions,for fast hashing, pseudo-random bit generation, authentication orauthenticated encryption, that enjoy very competitive safety margin vs speedratios. We highlight the bases for the security of these functions and diveinto their software implementations.
Beyond the FIPS 202 standard functions derived from Keccak (i.e., SHA-3 hashfunctions and SHAKE{128,256} extendable output functions), we present severalinteresting proposals, consistently based on the same permutation or its roundfunction. Among others:
* For authenticated encryption, Ketje and Keyak are schemes that were selected for the third round of the [CAESAR competition](http://competitions.cr.yp.to/caesar-submissions.html). In particular, Keyak proposes interesting features when protecting a stream of data flowing on a network. It exploits the parallelism in modern processors to achieve a high throughput. * [KangarooTwelve](http://eprint.iacr.org/2016/770.pdf) is a recently published arbitrary-output-length hash function. We designed it so that the implementation can automatically adapt to the available degree of parallelism. On Intel's Haswell and Skylake architectures, it achieves a speed below 1.5 cycles/byte for long inputs.
Two key aspects will be covered.
First, the essential goal of these functions is to remain secure despiteadvances in cryptanalysis. We will explain explain how we base the security ontwo strong pillars: the track record of third-party cryptanalysis and thegeneric security of the underlying construction.
Second, we will explore the [Keccak CodePackage](https://github.com/gvanas/KeccakCodePackage) and its two-levelstructure. The high-level cryptographic services are implemented in plain C,without any specific optimizations. The low-level services implement thepermutations and the state input/output functions, for which we provideoptimized code for different platforms. Another interesting topic to discussis how the parallelism is exploited on modern processors with SIMD units.
Room: Janson
Scheduled start: 2017-02-05 09:00:00
Video Information
Views
948
Likes
11
Duration
40:18
Published
Mar 6, 2018
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now