ECC Demystified: Unlocking the Secrets of Elliptic Curve Cryptography 🔐
Discover the true role of Elliptic Curve Cryptography in hashing and encryption. This guide simplifies ECC's concepts and reveals how it powers today's secure communications.

Network Technician
3 views • Oct 19, 2025
About this video
Elliptic Curve Cryptography (ECC) is the engine of modern security, yet its practical applications are often a source of confusion. This presentation tackles two of the most common misconceptions head-on: what is ECC's relationship with hashing, and how is it actually used for encryption?
This guide provides clear, definitive answers, explaining that ECC is neither a hash function nor a tool for bulk encryption. Instead, it is a powerful set of primitives that works with these other tools to build secure systems. Through detailed diagrams and a step-by-step walkthrough of a real-world hybrid encryption scheme, you will gain a precise understanding of ECC's proper role.
In this presentation, you will learn:
The clear distinction between ECC and hash functions, and a visual guide to how ECC uses hashing as a critical component in the ECDSA digital signature process.
Why asymmetric cryptography like ECC is never used for direct, bulk encryption, explained with the "Armored Truck vs. Delivery Van" analogy.
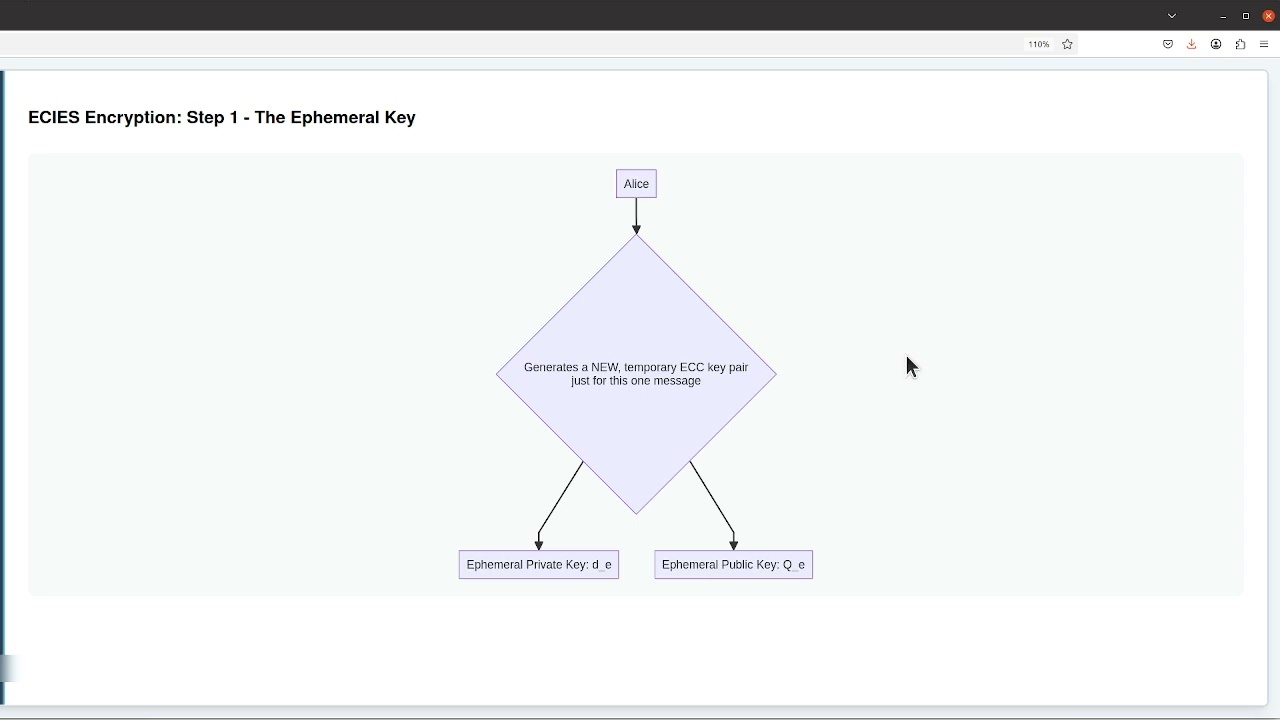
A complete, multi-step breakdown of the Elliptic Curve Integrated Encryption Scheme (ECIES), the standard method for hybrid encryption.
How an ephemeral key exchange (ECDH), a Key Derivation Function (KDF), and a fast symmetric cipher (like AES) all work together in a secure, efficient process.
Perfect for developers, students, and security professionals, this presentation clears up the fog around ECC, revealing how its core primitives—key exchange and digital signatures—are brilliantly combined with other cryptographic tools to provide both high performance and robust security.
This guide provides clear, definitive answers, explaining that ECC is neither a hash function nor a tool for bulk encryption. Instead, it is a powerful set of primitives that works with these other tools to build secure systems. Through detailed diagrams and a step-by-step walkthrough of a real-world hybrid encryption scheme, you will gain a precise understanding of ECC's proper role.
In this presentation, you will learn:
The clear distinction between ECC and hash functions, and a visual guide to how ECC uses hashing as a critical component in the ECDSA digital signature process.
Why asymmetric cryptography like ECC is never used for direct, bulk encryption, explained with the "Armored Truck vs. Delivery Van" analogy.
A complete, multi-step breakdown of the Elliptic Curve Integrated Encryption Scheme (ECIES), the standard method for hybrid encryption.
How an ephemeral key exchange (ECDH), a Key Derivation Function (KDF), and a fast symmetric cipher (like AES) all work together in a secure, efficient process.
Perfect for developers, students, and security professionals, this presentation clears up the fog around ECC, revealing how its core primitives—key exchange and digital signatures—are brilliantly combined with other cryptographic tools to provide both high performance and robust security.
Video Information
Views
3
Duration
13:08
Published
Oct 19, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.