ECB (Electronic Code Book) Explained in Urdu/Hindi | Complete Tutorial Part 28 🔐
Learn everything about ECB (Electronic Code Book) mode in Urdu/Hindi with this detailed lecture. Perfect for students and cybersecurity enthusiasts. Watch now!
IT Expert Rai Jazib
432 views • Aug 2, 2018
About this video
Welcome back to our channel
Title:- ECB (Electronic Code Book) || urdu hindi | electronic code book lecture | ECB tutorial | part 28
===
Topics Covered in the playlist (Try to Ignore this):
Electronic Code Book,ECB,ecb mode encryption example in hindi,ecb mode encryption example,ecb mode encryption example in urdu,electronic code book in hindi,electronic code book mode,electronic code book mode in hindi,electronic code book explanation with example,electronic code book explanation with example in hindi,what is electronic code book mode,what is electronic code book mode in hindi,what is ecb,what is ecb in hindi,concept of ecb,concept of ecb in hindi
cipher feedback mode in cryptography,cipher feedback mode in cryptography in hindi,cipher feedback mode example,cipher feedback mode example in hindi,Block Cipher Modes : Cipher Feedback Mode Explained,Block Cipher Modes : Cipher Feedback Mode Explained in Hindi,Cipher Feedback Mode Explanation with example in hindi,Cipher Feedback Mode Explanation with example,cfb mode encryption example in urdu,cfb mode encryption example,cfb mode encryption example in hindi,cipher,mode
• Introduction to Network Security, Information security, network security. Computer security, Security Trends, OSI Security Architecture, Security Attacks, Security Services, Security Mechanisms, A model for Network Security
• Symmetric encryption principles, Shift cipher, Rot-13 cipher, Ceasar cipher
• Cryptography, Cryptanalysis techniques,
• Security Threats in Ad-hoc Social Networks,
• Polyalphabetic ciphers, brute force search
• Fiestel cipher structure, Data Encryption Standard
• DES
• DES
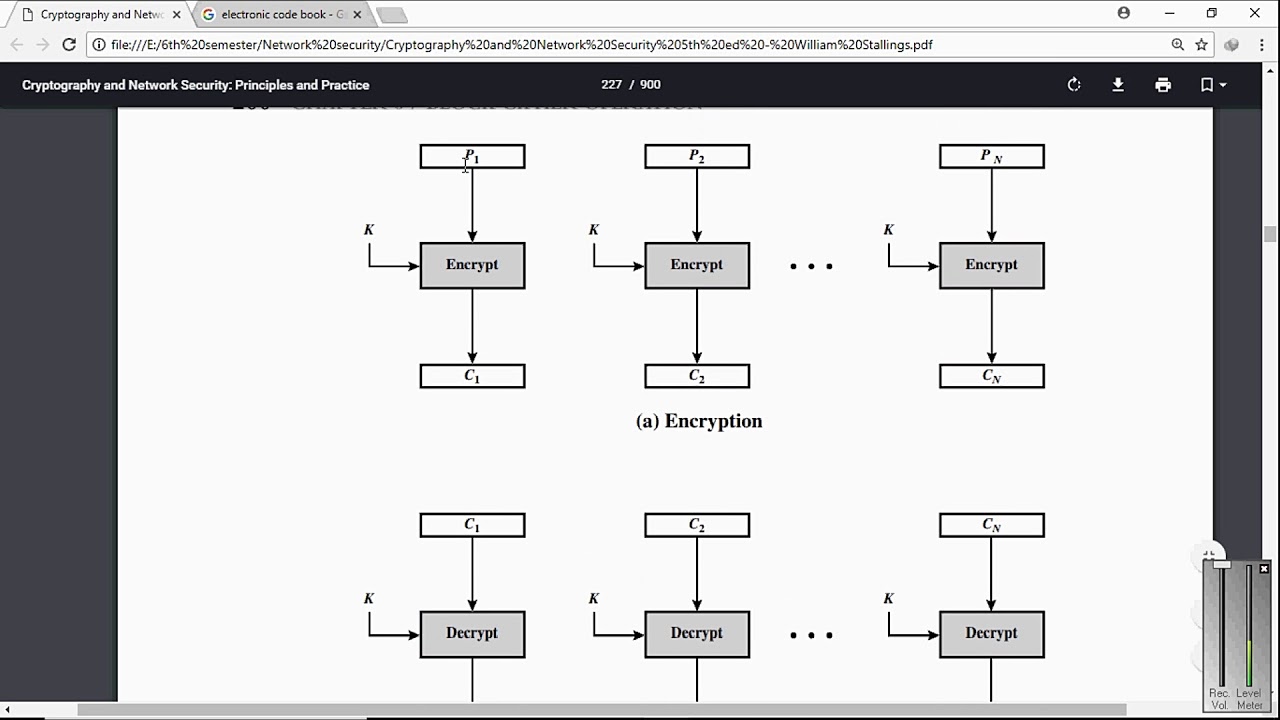
• Cipher Block Modes of Operations
• CBM
• Secret key cryptography, key distribution scenario and issues, PRNGs
• Public key cryptography
• Diffie-hellman key agreement, exchange and its security, public key applications
• Quiz # 2
• Mid Term Week
• Mid Term Week
• RSA, Digital signature
RSA security
• Secret sharing, Threshold based SS
• Blakley’s scheme, Entity authentication
• S-MIME
• IP Security Overview, IP Security Policy
• Web Security, Threats and approaches, SSL
• Legal and ethical aspects
• System Security, Intruders, Intrusion Detection, Audit Records, Statistical Anomaly detection
• Rule based intrusion detection, Distributed intrusion detection, honeypots,
• Password management, protection, Strategies to choose password
• Malicious Software’s
• The Need for Firewalls
• Firewall Characteristics
• Types of Firewalls
• Firewall Basing
• Firewall Location and Configurations
Tags:-
#General Knowledge-GK
#EH_BY_IT_Expert_Rai_Jazib
#Birds_Lover
#IT_Expert_Rai_Jazib
#Worlds_color
______________/LINKS\_____________________________
► Facebook:➜ https://www.facebook.com/IT-Expert-Rai-jazib-423950851519009
► Twitter:➜ https://twitter.com/Rai_jazib
► Pinterest:➜ https://www.pinterest.com/raijazib/
► Website:➜ https://itexpertraijazib.blogspot.com/
================================================
Title:- ECB (Electronic Code Book) || urdu hindi | electronic code book lecture | ECB tutorial | part 28
===
Topics Covered in the playlist (Try to Ignore this):
Electronic Code Book,ECB,ecb mode encryption example in hindi,ecb mode encryption example,ecb mode encryption example in urdu,electronic code book in hindi,electronic code book mode,electronic code book mode in hindi,electronic code book explanation with example,electronic code book explanation with example in hindi,what is electronic code book mode,what is electronic code book mode in hindi,what is ecb,what is ecb in hindi,concept of ecb,concept of ecb in hindi
cipher feedback mode in cryptography,cipher feedback mode in cryptography in hindi,cipher feedback mode example,cipher feedback mode example in hindi,Block Cipher Modes : Cipher Feedback Mode Explained,Block Cipher Modes : Cipher Feedback Mode Explained in Hindi,Cipher Feedback Mode Explanation with example in hindi,Cipher Feedback Mode Explanation with example,cfb mode encryption example in urdu,cfb mode encryption example,cfb mode encryption example in hindi,cipher,mode
• Introduction to Network Security, Information security, network security. Computer security, Security Trends, OSI Security Architecture, Security Attacks, Security Services, Security Mechanisms, A model for Network Security
• Symmetric encryption principles, Shift cipher, Rot-13 cipher, Ceasar cipher
• Cryptography, Cryptanalysis techniques,
• Security Threats in Ad-hoc Social Networks,
• Polyalphabetic ciphers, brute force search
• Fiestel cipher structure, Data Encryption Standard
• DES
• DES
• Cipher Block Modes of Operations
• CBM
• Secret key cryptography, key distribution scenario and issues, PRNGs
• Public key cryptography
• Diffie-hellman key agreement, exchange and its security, public key applications
• Quiz # 2
• Mid Term Week
• Mid Term Week
• RSA, Digital signature
RSA security
• Secret sharing, Threshold based SS
• Blakley’s scheme, Entity authentication
• S-MIME
• IP Security Overview, IP Security Policy
• Web Security, Threats and approaches, SSL
• Legal and ethical aspects
• System Security, Intruders, Intrusion Detection, Audit Records, Statistical Anomaly detection
• Rule based intrusion detection, Distributed intrusion detection, honeypots,
• Password management, protection, Strategies to choose password
• Malicious Software’s
• The Need for Firewalls
• Firewall Characteristics
• Types of Firewalls
• Firewall Basing
• Firewall Location and Configurations
Tags:-
#General Knowledge-GK
#EH_BY_IT_Expert_Rai_Jazib
#Birds_Lover
#IT_Expert_Rai_Jazib
#Worlds_color
______________/LINKS\_____________________________
► Facebook:➜ https://www.facebook.com/IT-Expert-Rai-jazib-423950851519009
► Twitter:➜ https://twitter.com/Rai_jazib
► Pinterest:➜ https://www.pinterest.com/raijazib/
► Website:➜ https://itexpertraijazib.blogspot.com/
================================================
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
432
Likes
3
Duration
11:08
Published
Aug 2, 2018